Ajax PRO Desktop — застосунок для моніторингу та адміністрування систем Ajax. Дозволяє налаштовувати та тестувати пристрої, керувати доступами користувачів, моніторити та обробляти події та тривоги необмеженої кількості систем Ajax.
Ajax PRO Desktop можна використовувати паралельно із PRO-застосунками для смартфонів. Монтажні та сервісні компанії можуть використовувати застосунок для налаштування та підключення систем безпеки, а охоронні та моніторингові — щоб розгорнути пульт централізованого спостереження (ПЦС).
Типи і можливості PRO-застосунків
Два типи PRO-застосунків Ajax: для комп’ютерів (ПК) та для смартфонів.
PRO-застосунок для ПК — це Ajax PRO Desktop. Доступний для Windows та macOS. У застосунку для ПК можна створювати компанії, керувати їх налаштуваннями, додавати співробітників та регулювати їхні права. Ajax PRO Desktop потрібен для моніторингу та дистанційного налаштування систем Ajax.
PRO-застосунок для смартфонів — це Ajax PRO: Tool for Engineers. Доступний для смартфонів на iOS та Android. Мобільний застосунок зручний у використанні для інженерів монтажу. Дозволяє створювати простори в персональному PRO-акаунті чи обліковому записі компанії, додавати автономні пристрої (наприклад, камери Ajax, NVR або розумні замки Yale) та хаби й керувати налаштуваннями доступних систем.
| Ajax PRO Desktop (застосунок для ПК) |
Ajax PRO: Tool for Engineers (застосунок для смартфонів) |
|
| Під’єднати пристрої та налаштувати систему | + | + |
| Підключити простір до компанії | + | + |
|
Створити компанію |
+ | — |
| Редагувати інформацію про компанію | + | — |
|
Додавати співробітників |
+ | — |
|
Змінити права співробітників |
+ | — |
|
Моніторинг подій та тривог |
+ | — |
Загальна інформація
Одна підключена до простору компанія — це один користувач незалежно від того, скільки співробітників (PRO-акаунтів) прив’язано до цієї компанії. До простору можна підключити будь-яку кількість компаній у межах ліміту користувачів. У простір без хаба можна додати до 200 користувачів, а ліміт користувачів у просторі з хабом залежить від моделі хаба.
Якщо користувач вийшов із застосунку, то для повторного входу слід використовувати логін та пароль PRO-акаунта. Якщо для PRO-акаунта увімкнено двофакторну автентифікацію, необхідно пройти її для входу у Ajax PRO Desktop.
Встановлення застосунку Ajax PRO Desktop
- Завантажте файл інсталяції застосунку.
- Відкрийте завантажений файл.
- Встановіть Ajax PRO Desktop.
Створення PRO-акаунта та вхід до застосунку
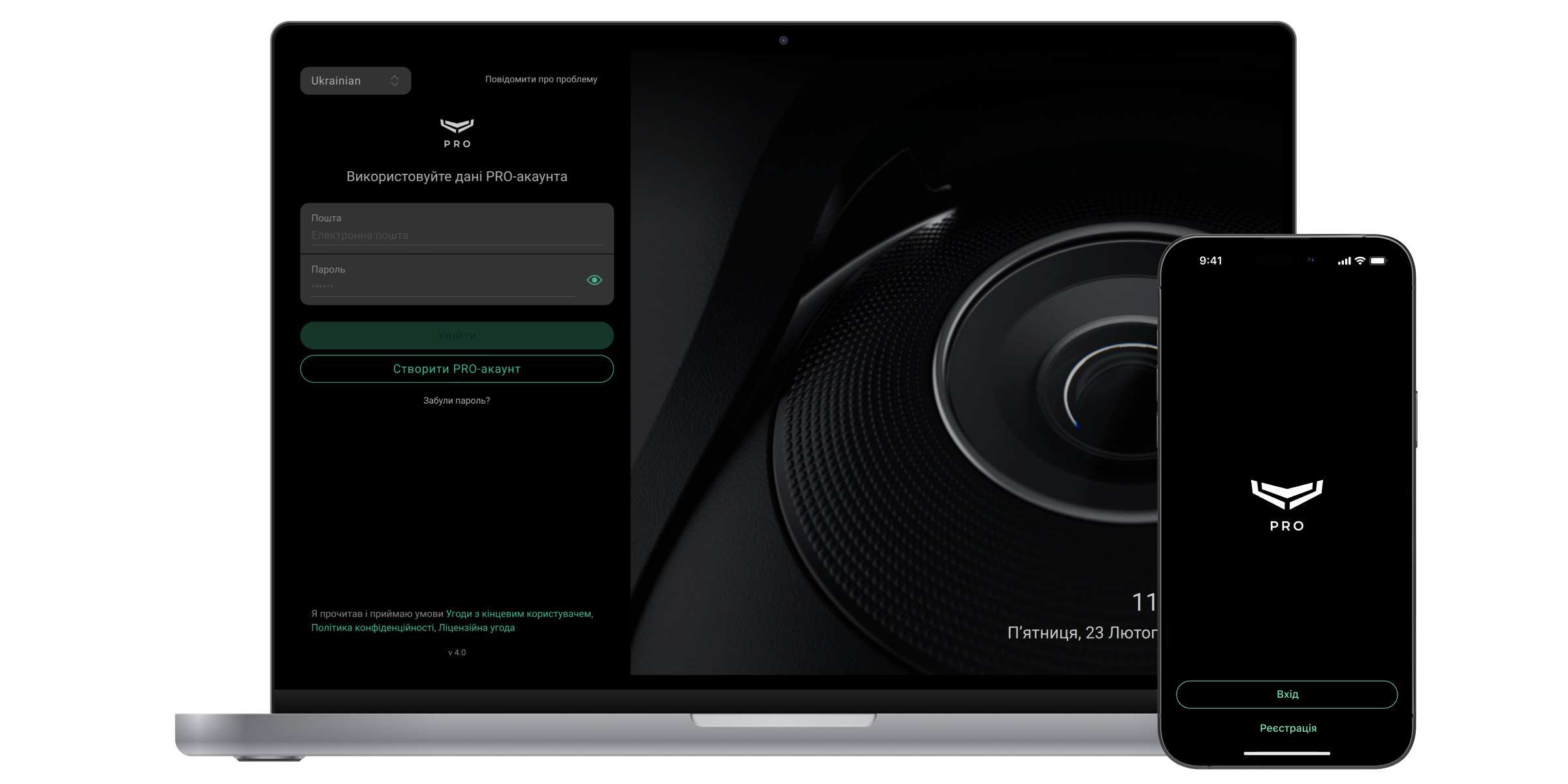
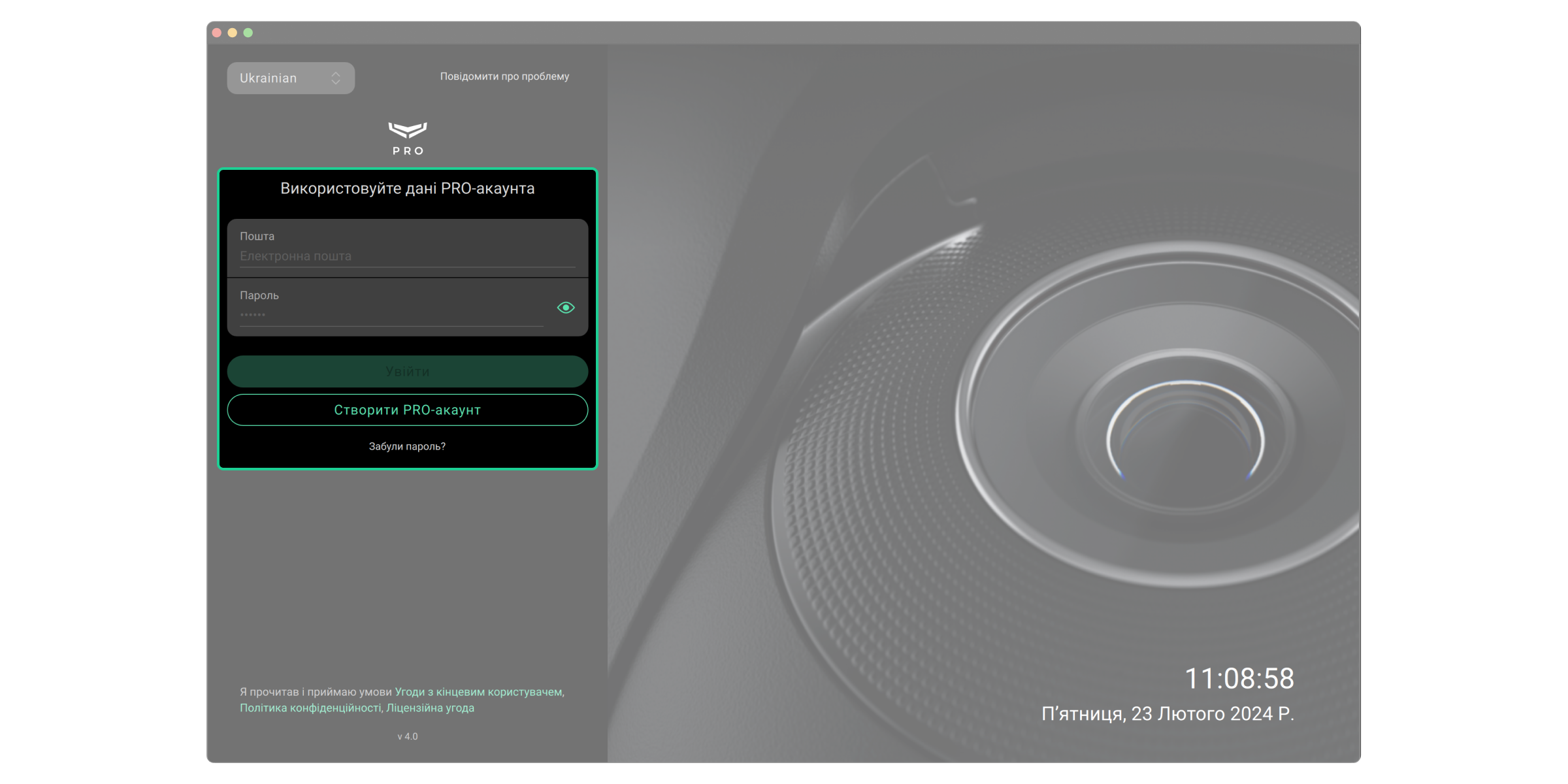
Для входу до Ajax PRO Desktop потрібен PRO-акаунт. Акаунт має бути зареєстрований у будь-якому з цих двох застосунків: Ajax PRO Desktop або Ajax PRO: Tool for Engineers. Ви не можете увійти до PRO-застосунку з логіном та паролем від застосунку для кінцевих користувачів Ajax Security System. PRO-акаунт відрізняється від акаунта, створеного в застосунку для кінцевих користувачів.
Якщо ви маєте PRO-акаунт: заповніть поля Електронна пошта і Пароль, а потім клацніть Увійти.
Якщо ви не маєте PRO-акаунта: клацніть Створити PRO-аккаунт у Ajax PRO Desktop або Ajax PRO: Tool for Engineers та дотримуйтеся інструкцій застосунку. Під час створення PRO-акаунта ви можете використовувати ті самі email та номер телефону, що й в акаунті Ajax Security System. Це будуть різні облікові записи.
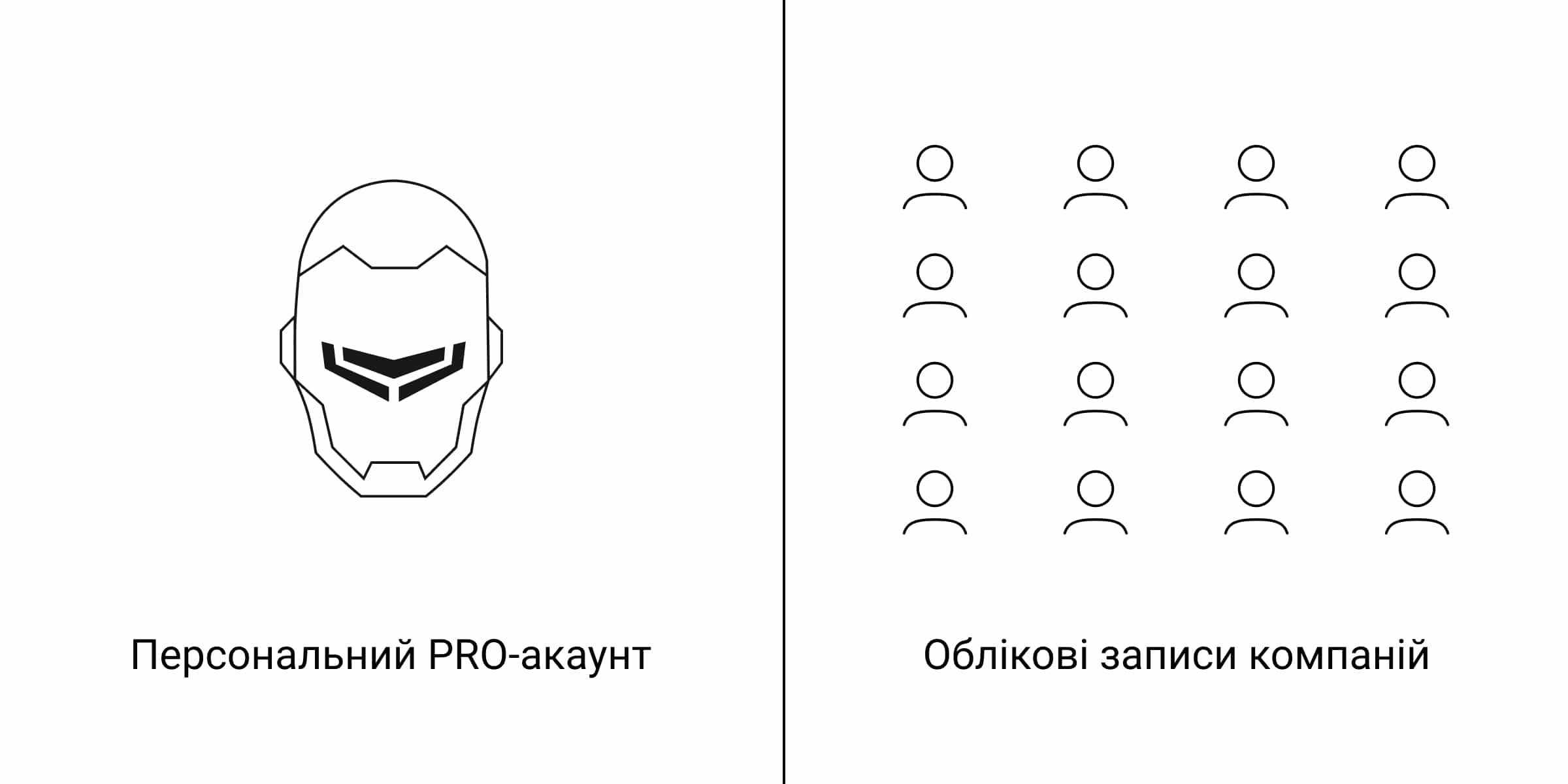
Види облікових записів
У PRO-застосунках Ajax доступні два види облікових записів: персональний PRO-акаунт і обліковий запис компанії.
Персональний PRO-акаунт потрібен для підключення до компаній, а також налаштування та керування під’єднаниними системами Ajax.
Облікові записи компаній необхідні для ведення охоронного бізнесу: моніторингу тривог та подій, обслуговування, налаштування та встановлення систем Ajax.
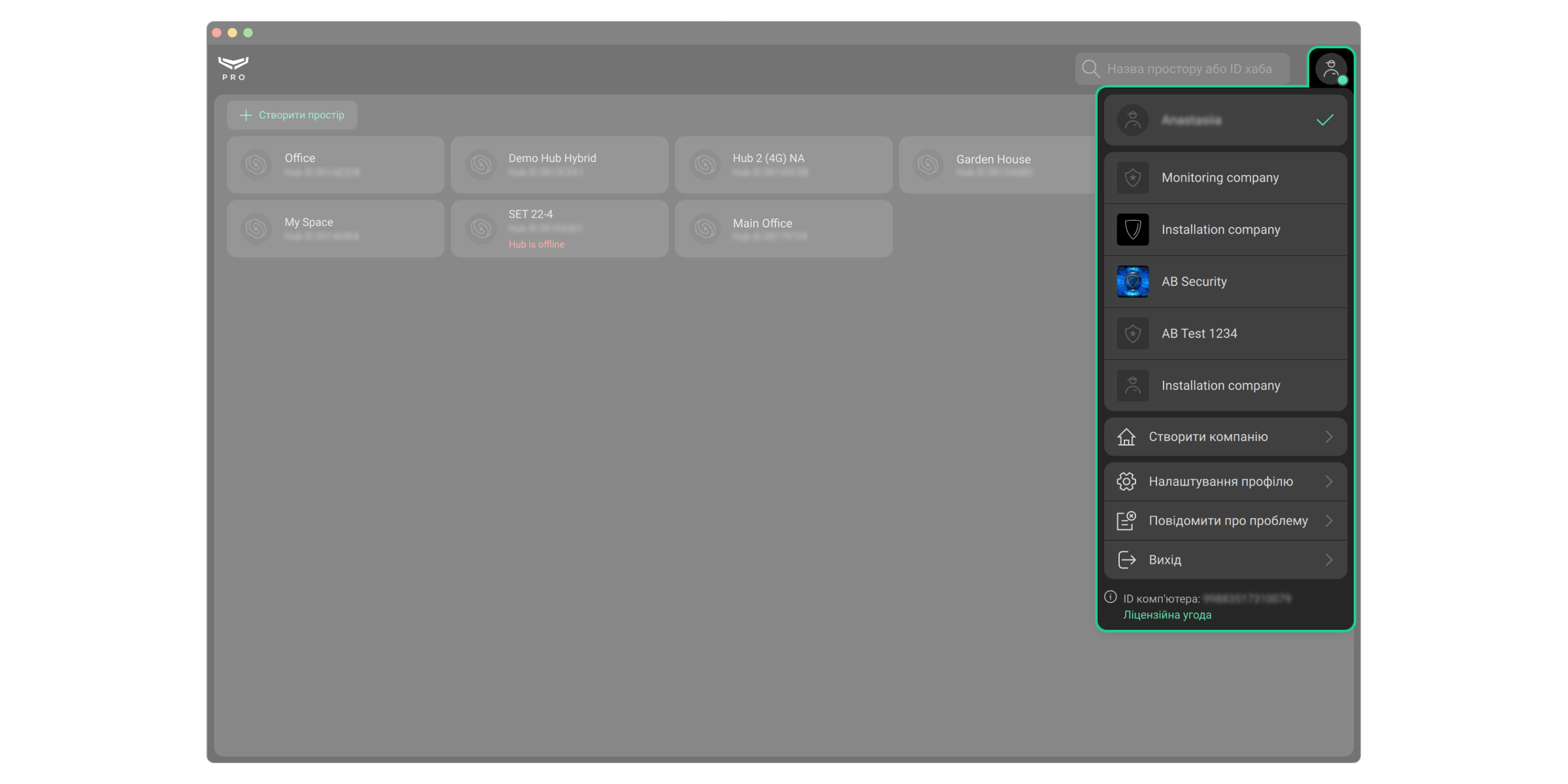
Перемикання між персональним PRO-акаунтом та акаунтом компанії
Після входу у застосунок автоматично відкривається та компанія, з якою PRO-акаунт працював минулого разу. Щоб перейти в персональний PRO-акаунт або акаунт іншої компанії:
- Клацніть на меню з логотипом охоронної компанії або ініціалами.
- Виберіть персональний PRO-акаунт або акаунт компанії.
Безпека акаунта
Для захисту PRO-акаунта від злому налаштуйте двофакторну автентифікацію та відстежуйте сесії на інших пристроях. Використовуйте обидва інструменти захисту, щоб знизити ймовірність доступу сторонніх до вашого PRO-акаунта.
Змініть пароль та активуйте двофакторну автентифікацію, якщо виявили сторонні сесії облікового запису.
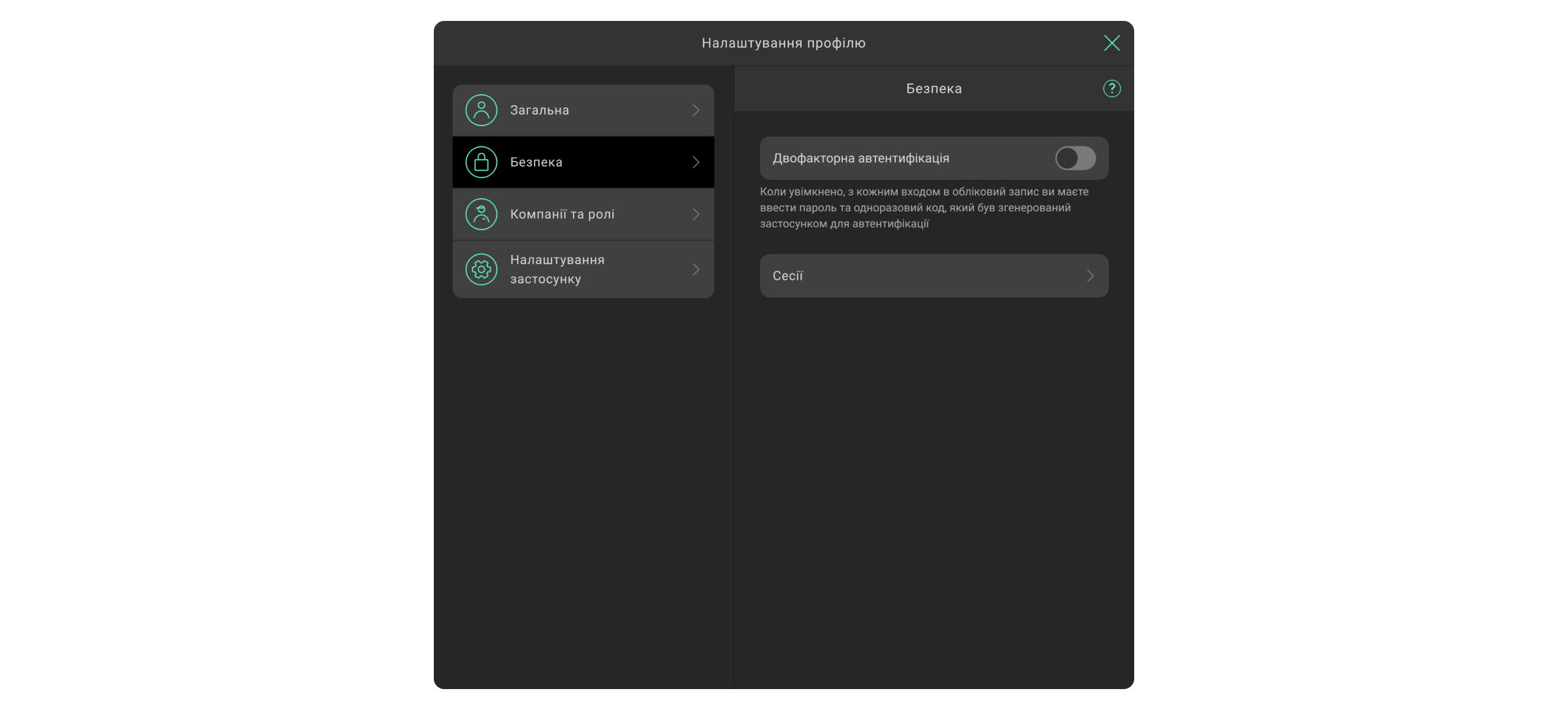
Як увімкнути двофакторну автентифікацію
- Натисніть на аватарку (значок) PRO-акаунта.
- Перейдіть до меню Налаштування профілю.
- Виберіть вкладку Безпека.
- Увімкніть опцію Двофакторна автентифікація.
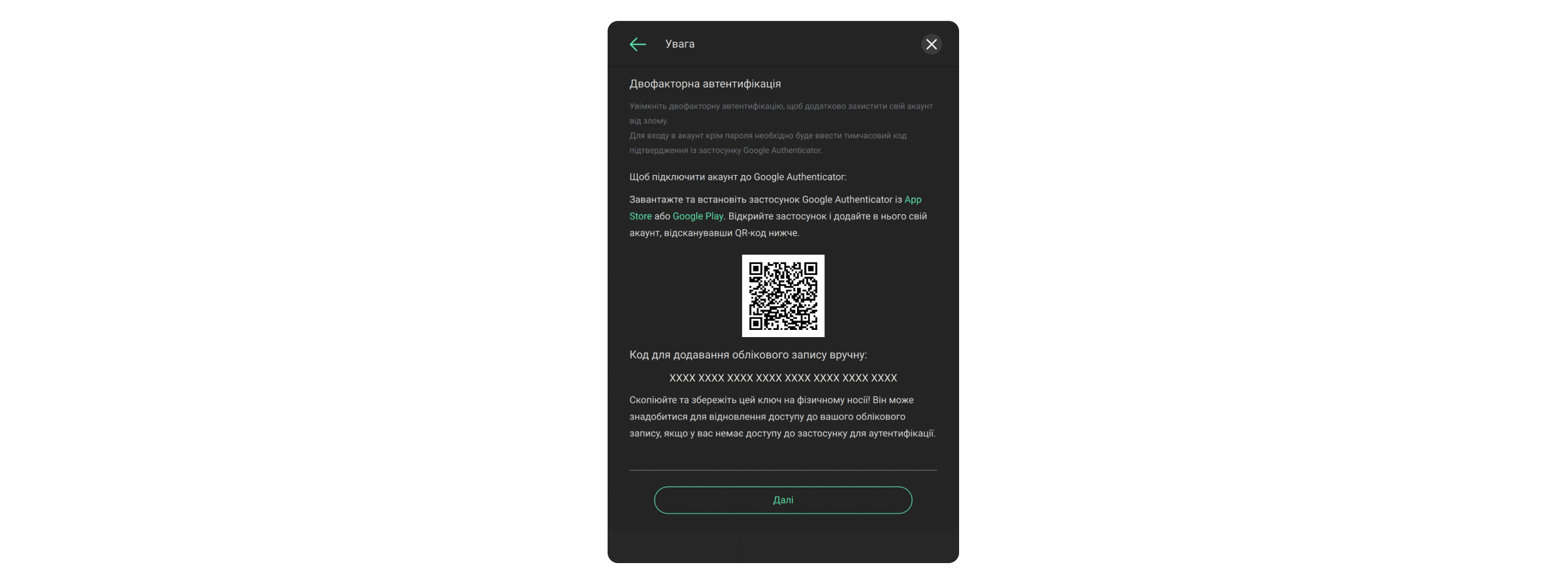
- Підключіть автентифікатор, дотримуючись інструкцій на екрані. Наприклад, застосунок Google Authenticator.
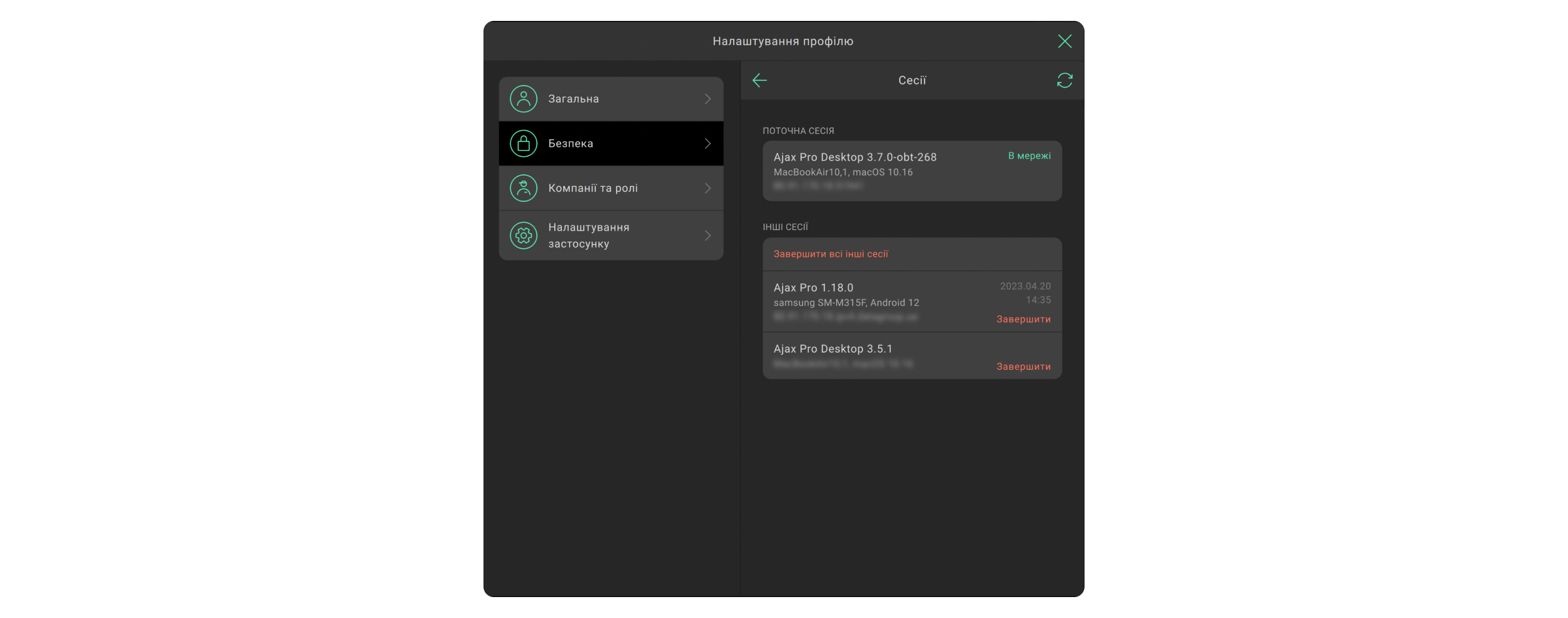
Як перервати сесію акаунта
- Натисніть на аватарку (значок) акаунта.
- Перейдіть до меню Налаштування профілю.
- Виберіть вкладку Безпека.
- Натисніть на Сесії.
Сесія пристрою, з якого ви увійшли у застосунок, має назву Поточна сесія. Нижче доступні Інші сесії пристроїв, з яких виконано вхід до PRO-акаунта. Ви можете завершити сесію, для цього клацніть Завершити або Завершити всі інші сесії, крім поточної.
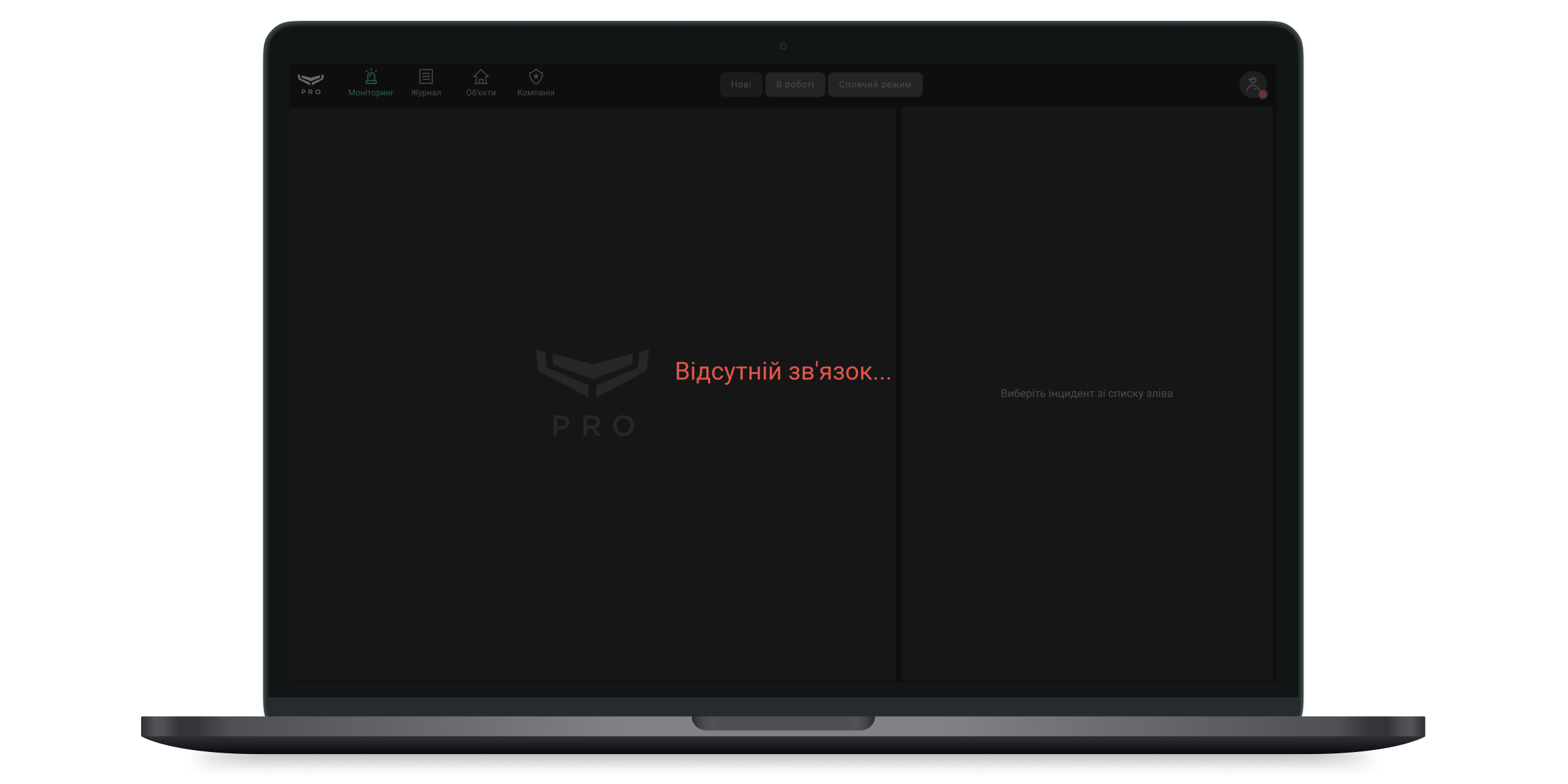
Стан з’єднання з Ajax Cloud
Індикатор у правому верхньому куті екрана Ajax PRO Desktop показує статус з’єднання з сервером Ajax Cloud. Якщо інтернет-з’єднання активне, індикатор горить зеленим. Якщо з’єднання відсутнє — червоним, а на екрані відображається сповіщення Відсутній звʼязок.
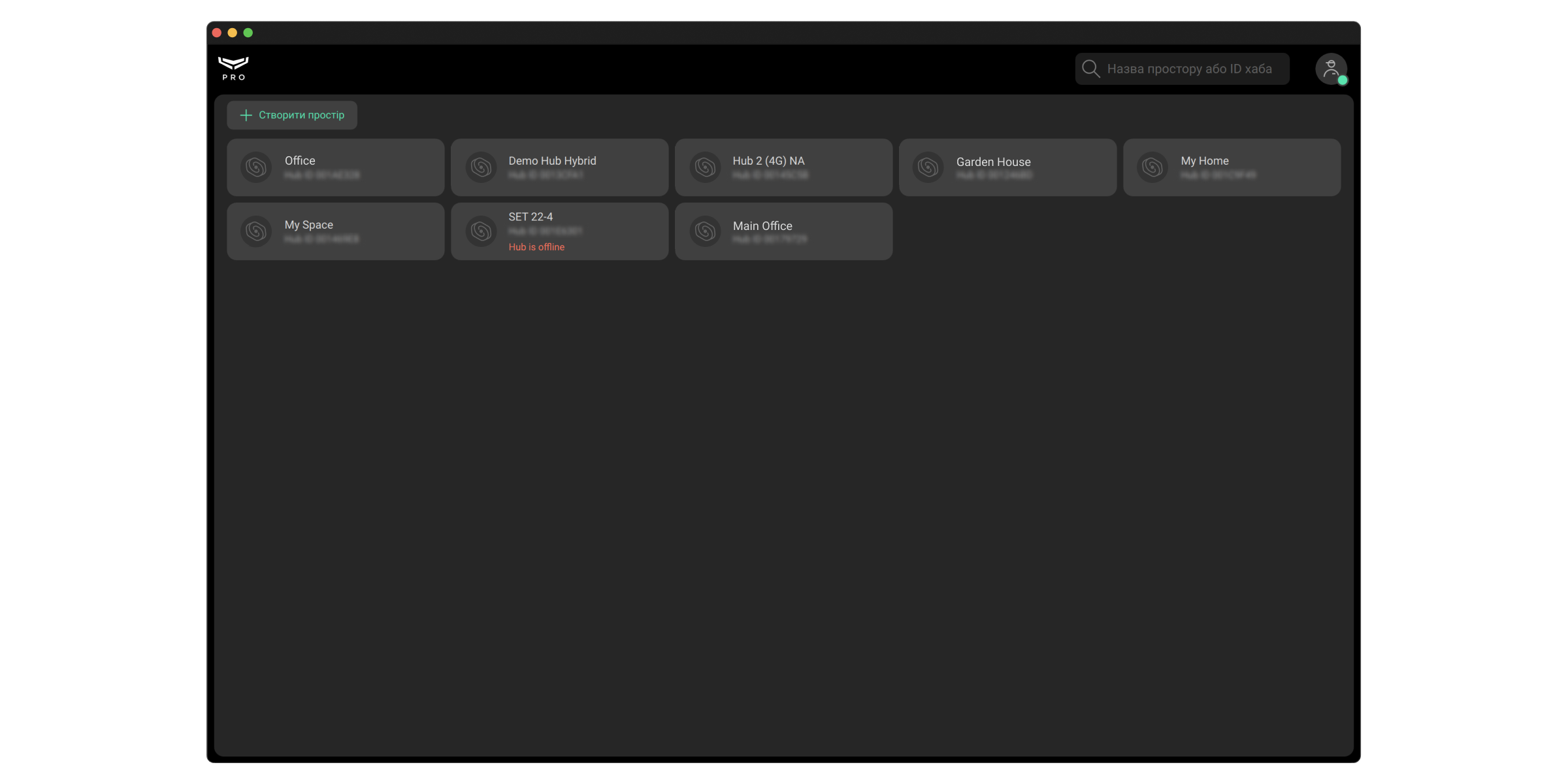
Робота з персональним PRO-акаунтом
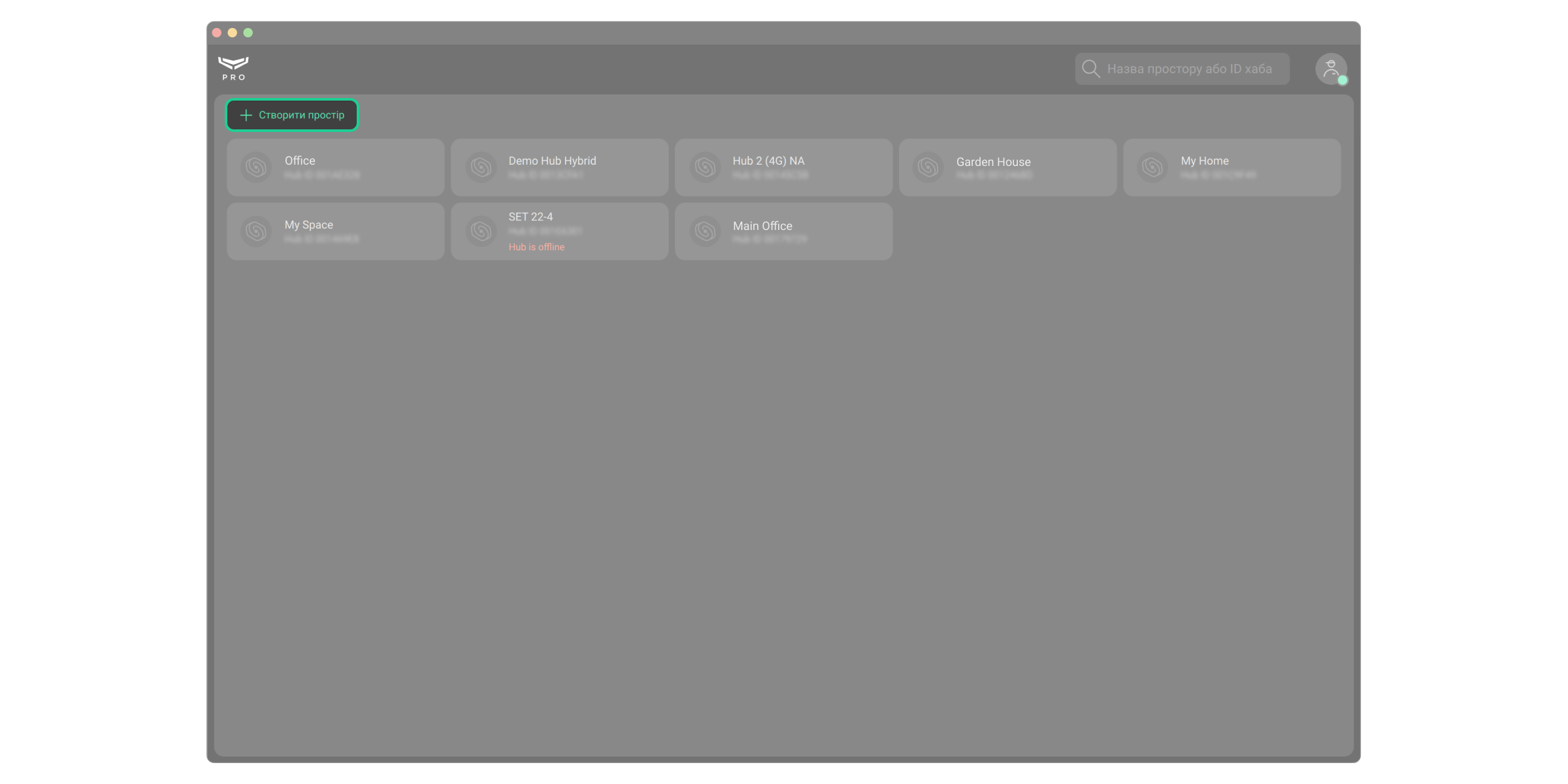
Після входу у застосунок відкривається перелік прив’язаних до PRO-акаунта просторів. Хаби, з якими немає зв’язку, позначені червоним підписом Не в мережі. Лічильник несправностей (червоний значок із цифрою) показує сумарну кількість несправностей конкретної системи безпеки. Інформація про кількість несправностей і хаби, що не в мережі (якщо в просторі є хаб), оновлюється автоматично.
Простір — це віртуальна сутність, де зібрані різні автономні пристрої, що розташовані на одному фізичному об’єкті. У простір можна додати хаб з датчиками, лише NVR з камерами або розумні замки Yale чи скомбінувати всі ці елементи в одній системі.
Функціональність простір доступна для хабів із версією прошивки, починаючи від OS Malevich 2.6, і застосунків таких версій і вище:
- Ajax Security System 3.0 для iOS;
- Ajax Security System 3.0 для Android;
- Ajax PRO: Tool for Engineers 2.0 для iOS;
- Ajax PRO: Tool for Engineers 2.0 для Android;
- Ajax PRO Desktop 4.0 для macOS;
- Ajax PRO Desktop 4.0 для Windows.
Пошук потрібного простору. У застосунку доступний пошук просторів за їхнім ім’ям або ідентифікатором хаба (якщо в просторі є хаб). Простори відображаються одночасно з введенням тексту.
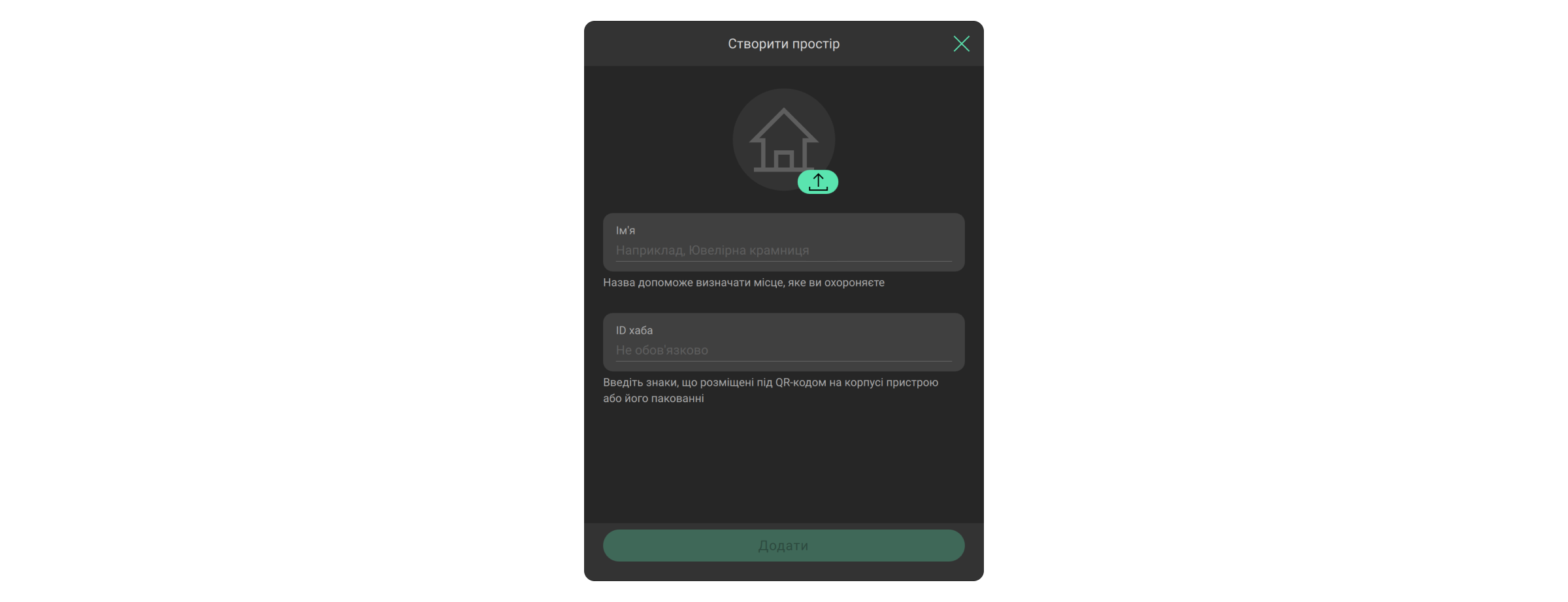
Кнопка Створити простір дає змогу прив’язати новий простір до PRO-акаунта.
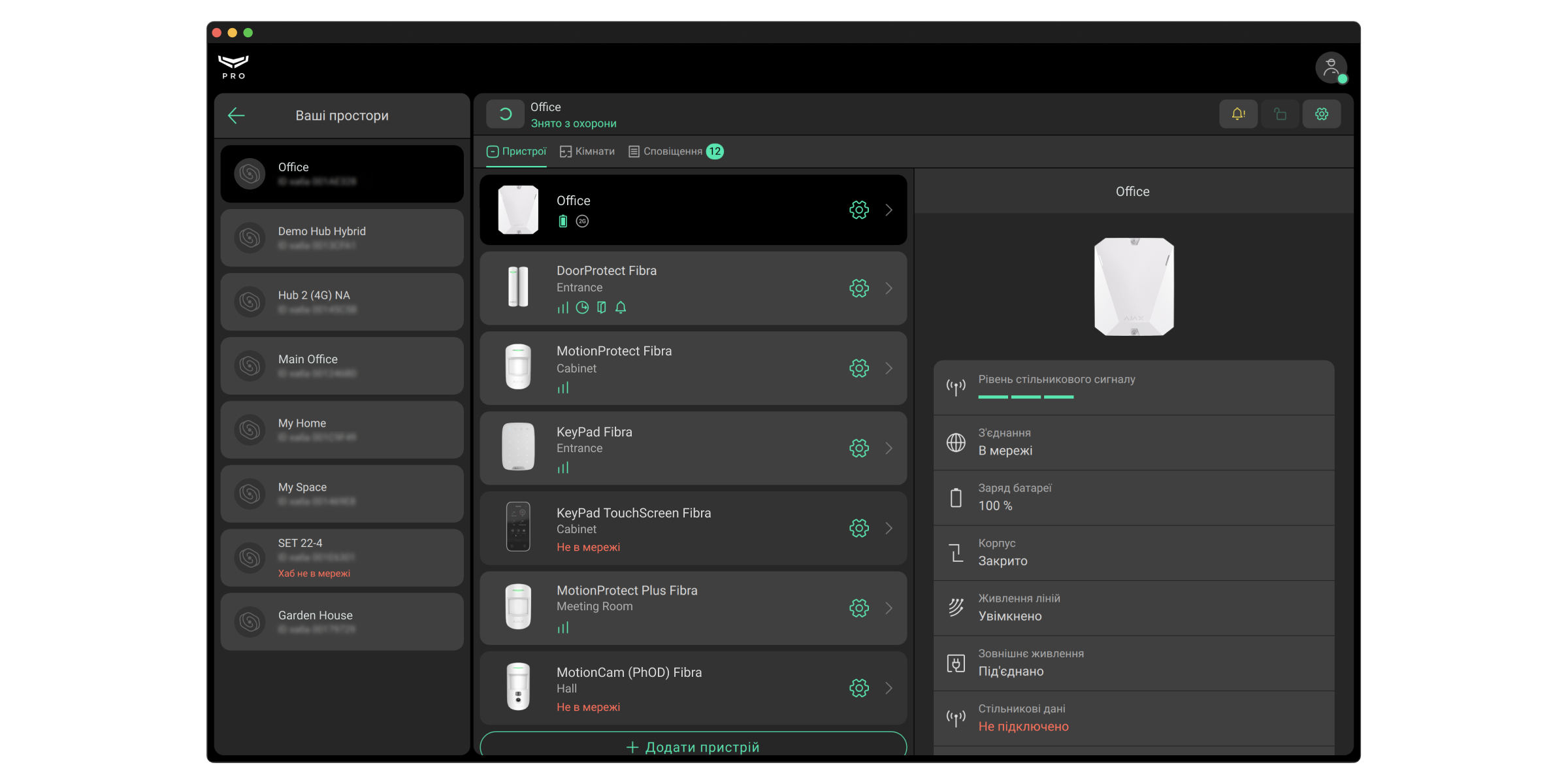
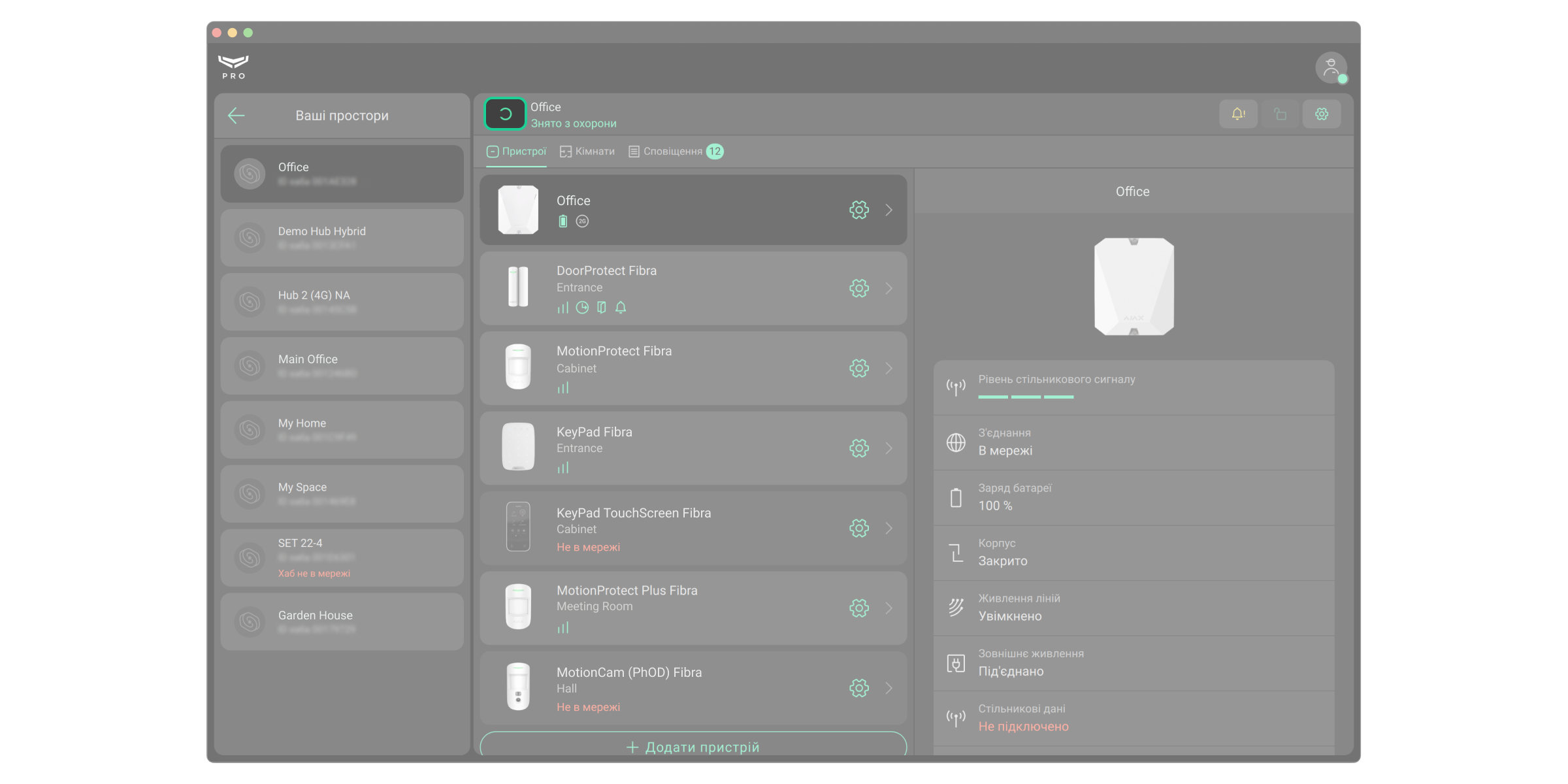
Меню системи безпеки
Меню містить кімнати, пристрої, стрічку сповіщень і кнопки керування охороною об’єкта. Кнопка Ваші простори повертає до списку прив’язаних просторів.
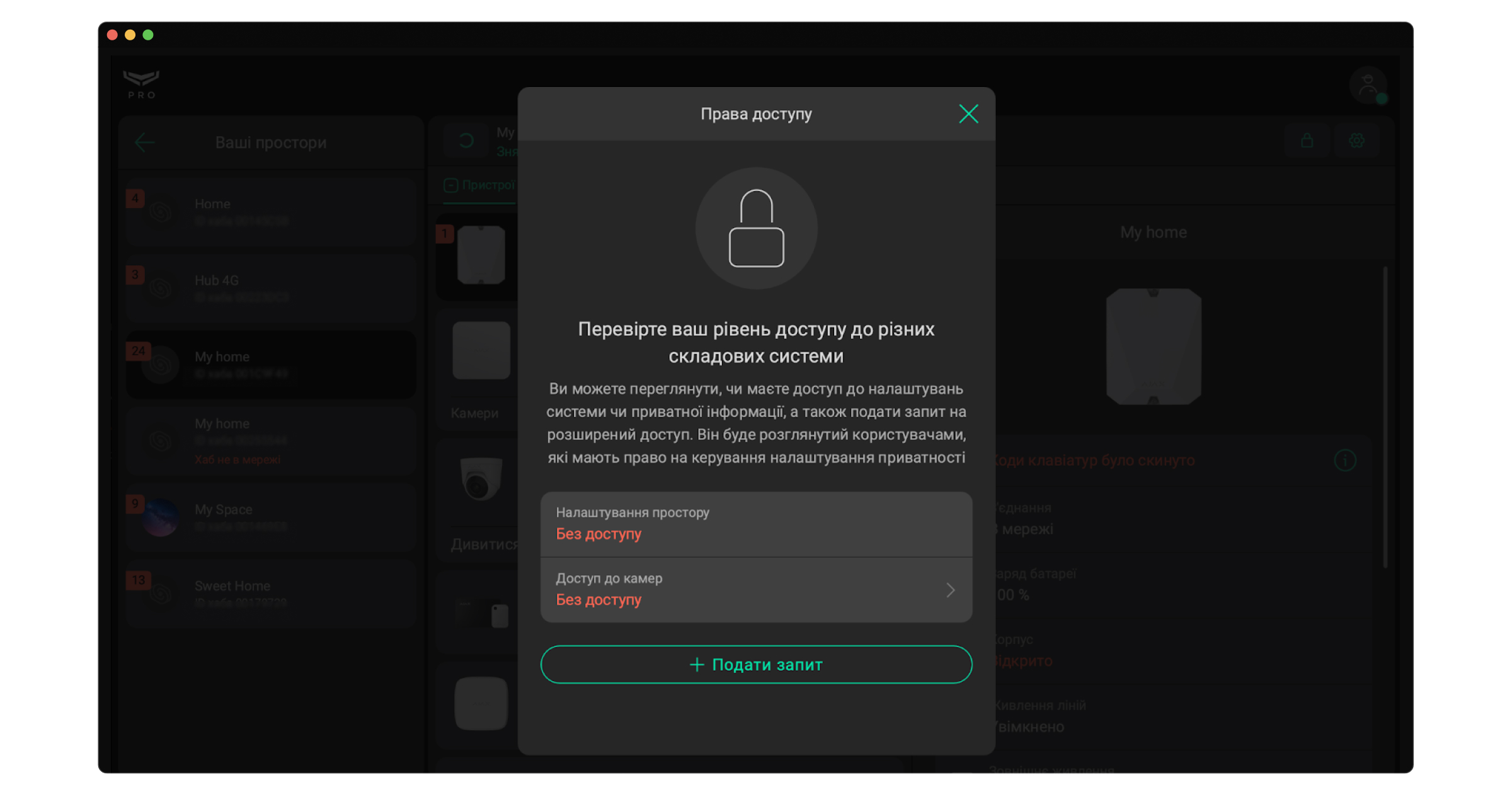
PRO-акаунт може мати тимчасовий або постійний доступ до налаштувань системи та перегляду відео з камер. Щоб перевірити рівень доступу до різних складових системи, натисніть або
, у правому верхньому куті. У зазначеному на скріншоті полі зображується час, на який PRO-акаунту надано доступ до налаштувань простору та кількість камер до яких надано доступ. Клацніть на поле та виберіть потрібну опцію, щоб зробити запит на тимчасовий або постійний доступ. Запит може підтвердити адміністратор простору.
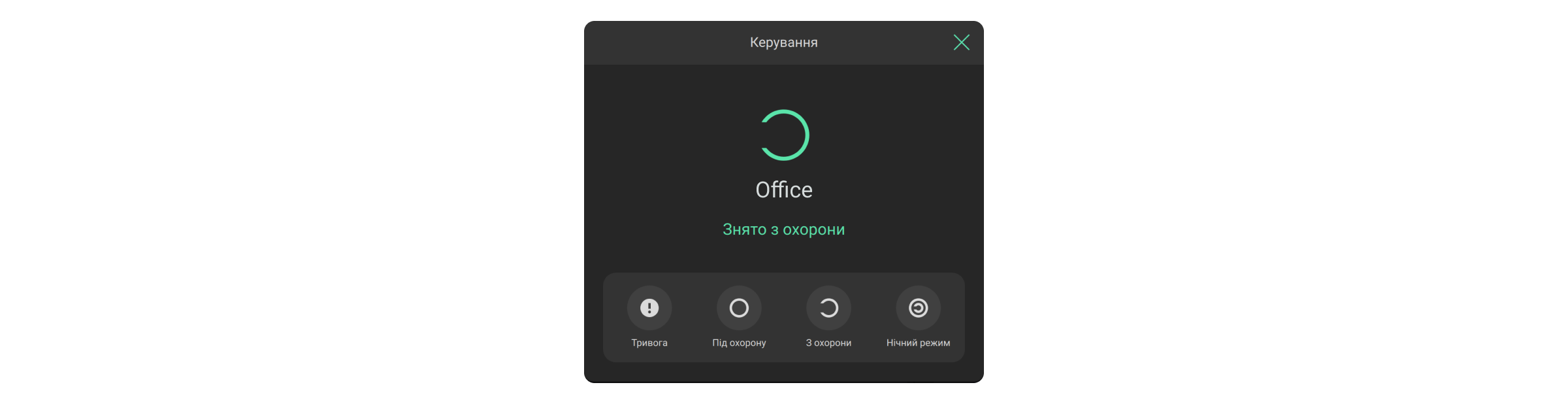
PRO-акаунт може керувати режимами охорони об’єкта, якщо йому надано таке право адміністратором простору. У зазначеному на скріншоті полі зображується стан охорони конкретної системи Ajax. Можна клацнути на поле, щоб змінити режим охорони або натиснути Тривожну кнопку, якщо PRO-акаунт має на це право.
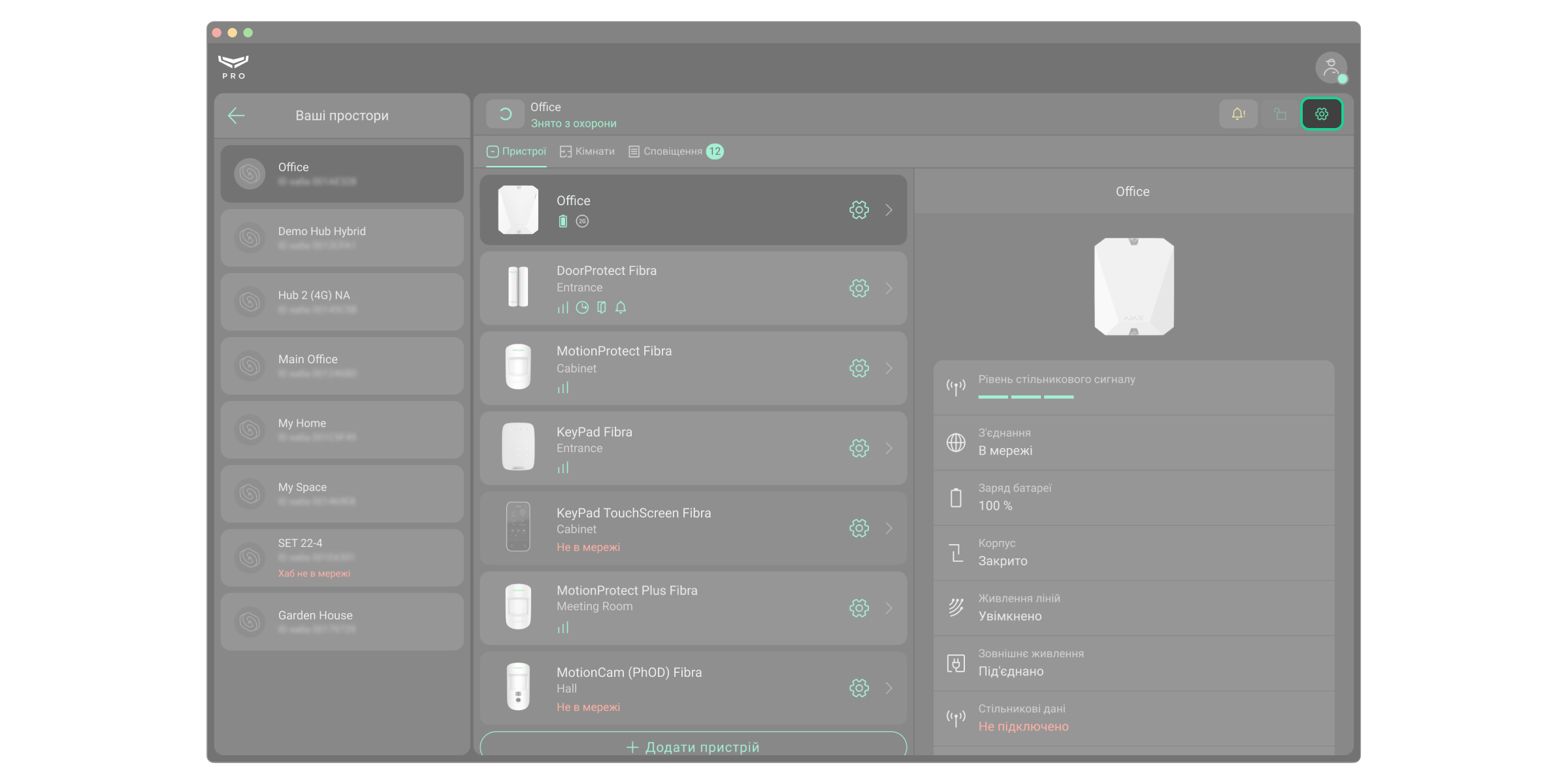
Налаштування системи безпеки
Зміна налаштувань простору
- Виберіть простір у списку та перейдіть до меню Налаштування
.
- Внесіть зміни.
- Закрийте налаштування.
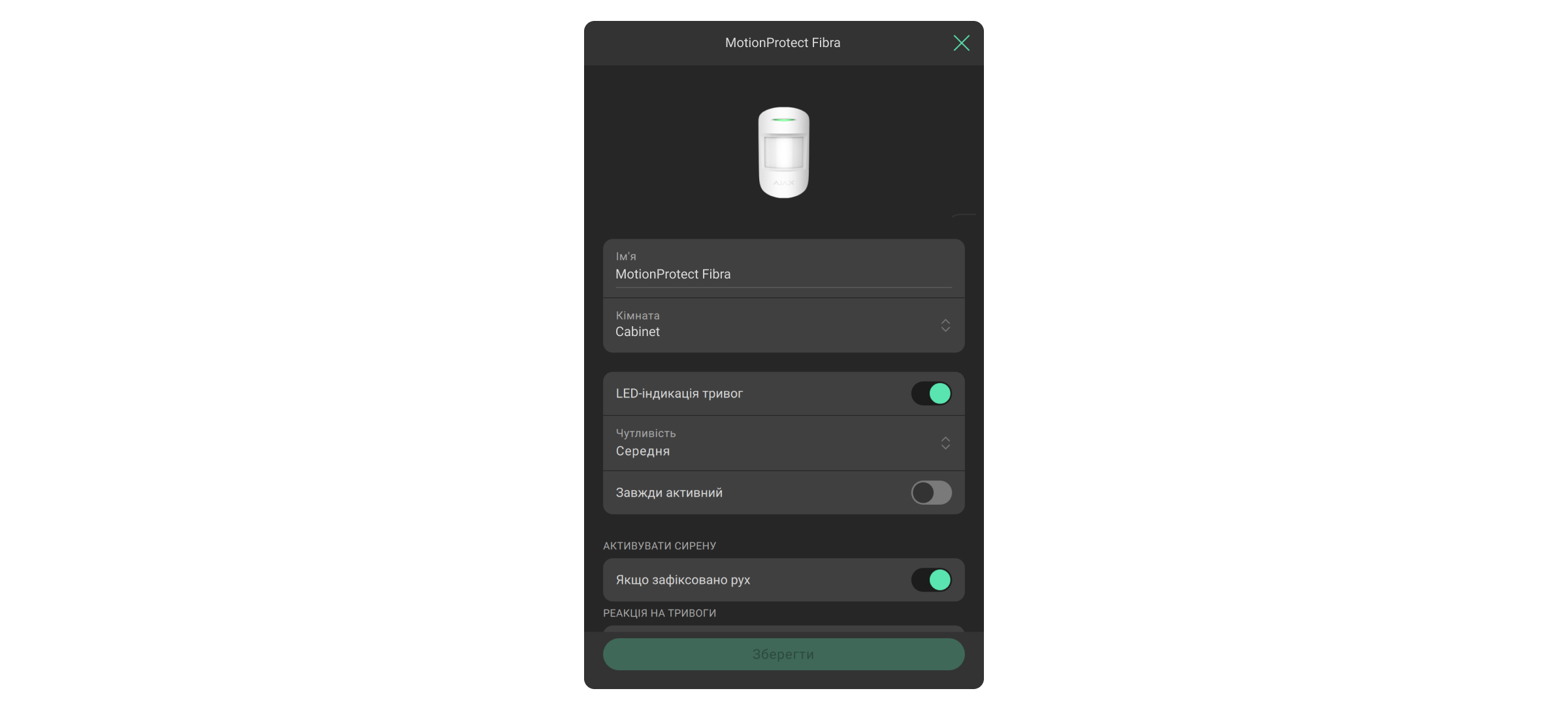
Зміна налаштувань хаба або пристроїв
- Перейдіть у меню Пристрої
.
- Виберіть пристрій у списку.
- Перейдіть у його Налаштування
.
- Внесіть зміни.
Усі налаштування пристрою описані в інструкції з використання цього пристрою.
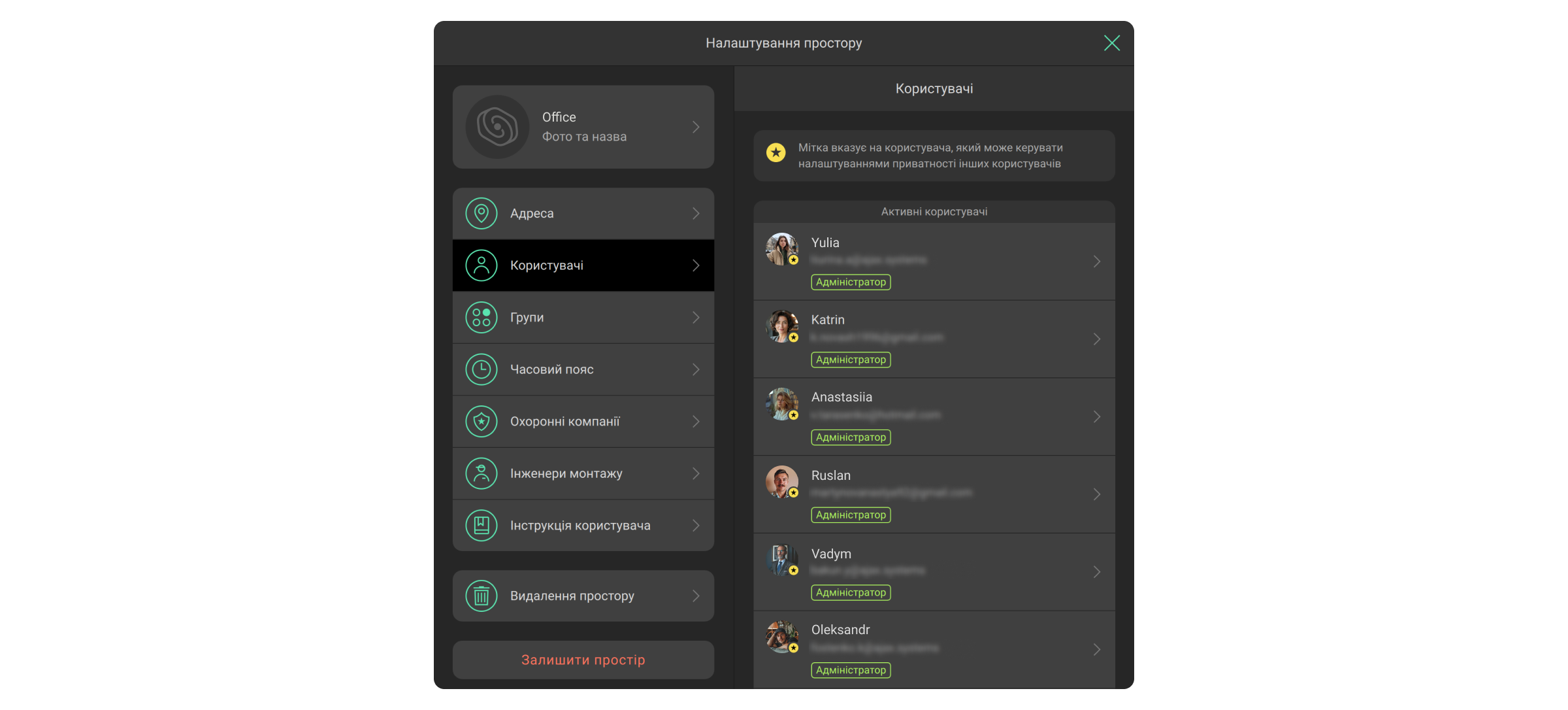
Керування користувачами
- Перейдіть у Налаштування
простору.
- Виберіть меню Користувачі.
- Внесіть зміни: додайте користувачів, змініть їхні права або видаліть.
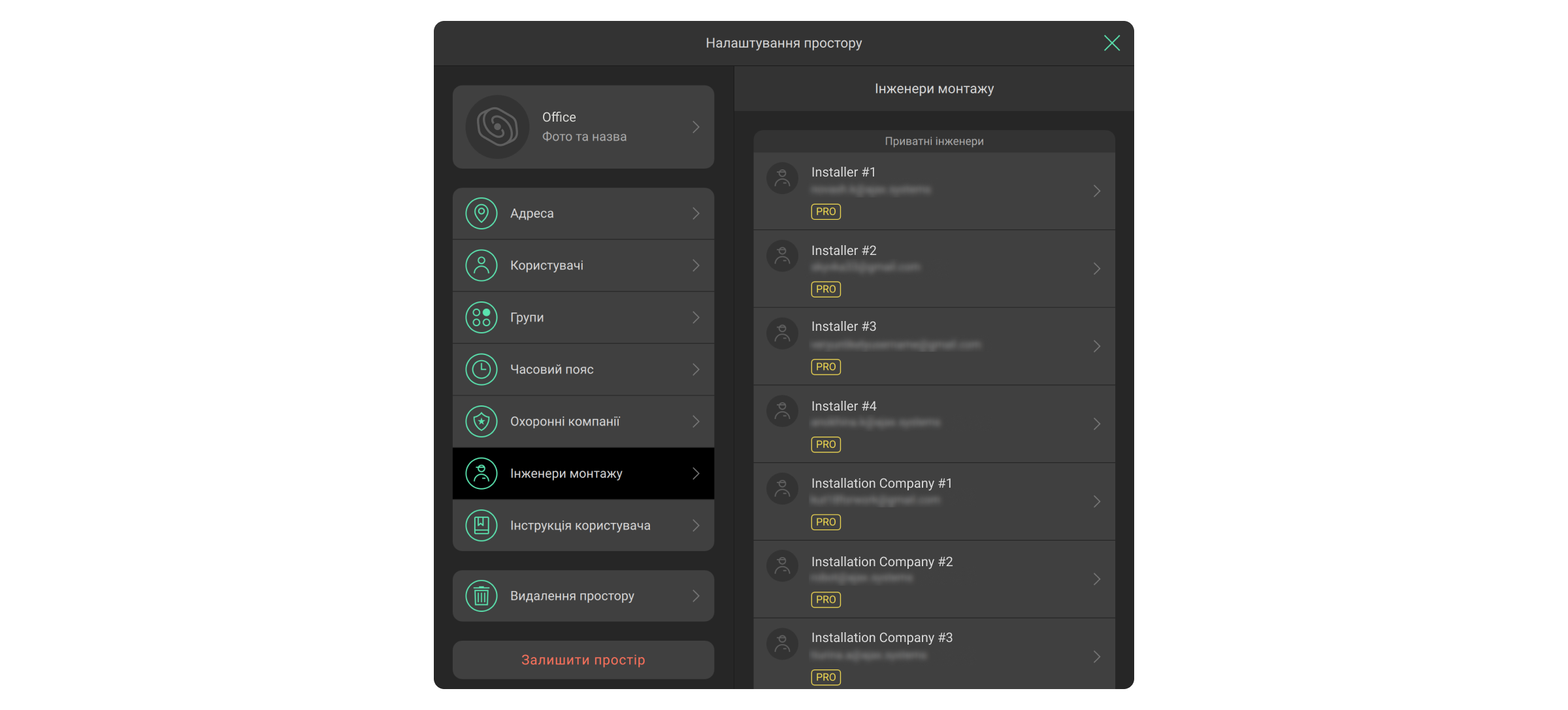
Керування PRO-акаунтами
- Перейдіть у Налаштування
простору.
- Виберіть меню Інженери монтажу.
- Внесіть зміни: додайте PRO-акаунт, змініть його права або видаліть.
Робота з обліковим записом компанії
Обліковий запис компанії об’єднує під одним профілем всі об’єкти охорони, акаунти співробітників та екіпажі груп швидкого реагування (ГШР).
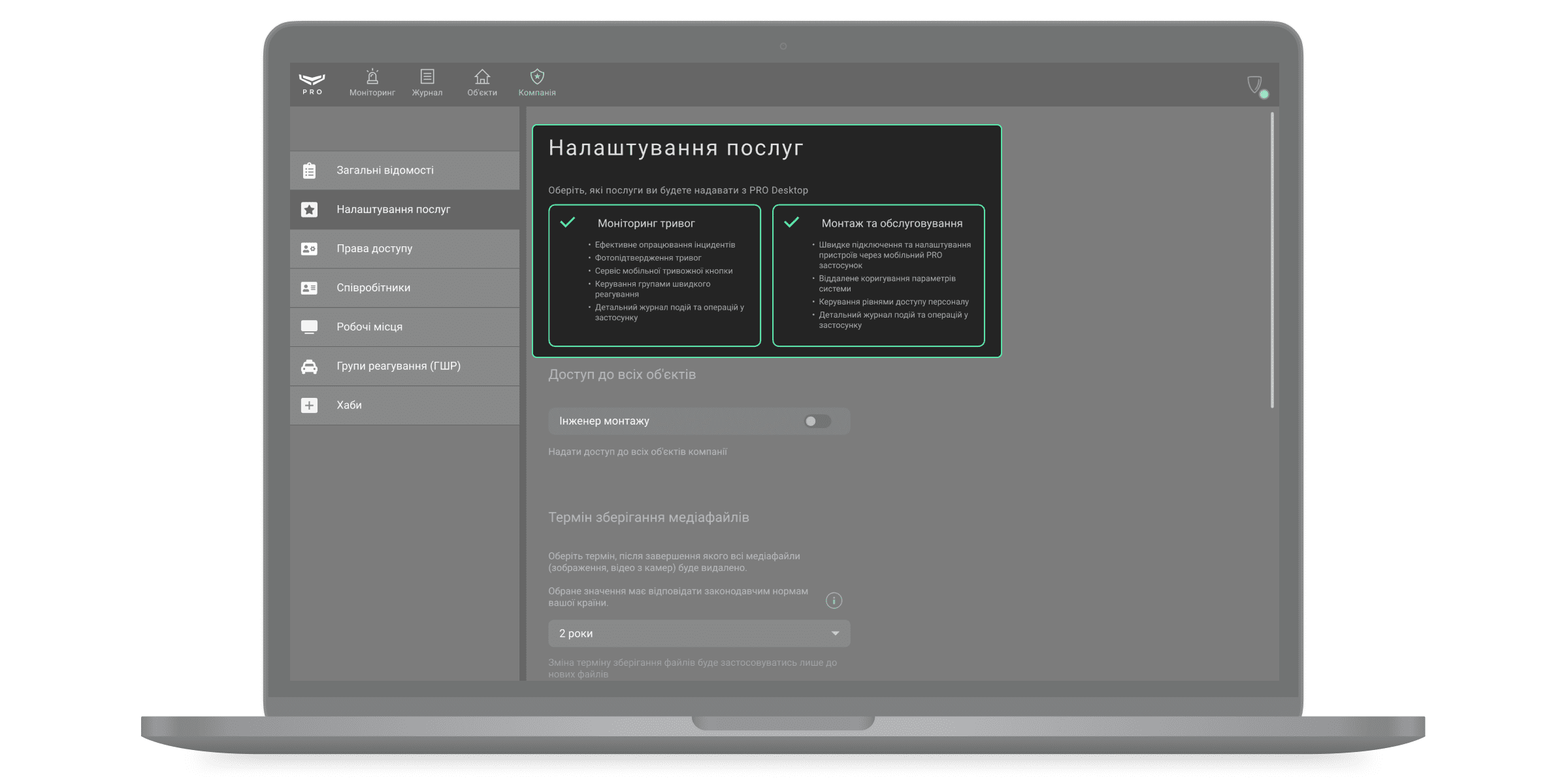
Типи послуг компанії
Ajax PRO Desktop – це комплексний інструмент для роботи охоронного, монтажного та сервісного бізнесу. У застосунку є набір функцій як для Моніторингу тривог, так і для Монтажу та обслуговування.
Набір функцій для кожного типу вибирається окремо. Застосунок також дозволяє вибрати одразу два типи послуг: Моніторинг тривог та Монтаж та обслуговування. Це передбачено для компаній, які одночасно встановлюють системи безпеки та реагують на їхні тривоги та події.
Власник компанії вказує типи послуг під час реєстрації компанії та може змінити їх у будь-який момент. Інтерфейс та функції застосунку підлаштовуються під вибраний тип послуг.
Створення компанії
PRO-акаунт, що створив компанію у застосунку, стає власником компанії. Такий PRO-акаунт має доступ до всіх модулів Ajax PRO Desktop, може додавати та видаляти співробітників, а також змінювати інформацію про компанію. Один PRO-акаунт може створити необмежену кількість компаній.
Роль власника компанії може бути надана лише одному PRO-акаунту. Компанію повинен створювати власник чи уповноважений співробітник компанії. Видалення компанії або зміна власника не передбачено.
Щоб створити компанію:
- Відкрийте Ajax PRO Desktop.
- Увійдіть у PRO-акаунт.
- Перейдіть у персональний PRO-акаунт, якщо відкритий обліковий запис компанії.
- Перейдіть у модуль Компанія.
- Клацніть Створити компанію.
- Введіть назву компанії та країну надання послуг.
- Вкажіть тип послуг, які надає компанія: моніторинг тривог, монтаж та обслуговування або відразу обидва типи послуг.
- Заповніть інформацію про компанію та дотримуйтеся інструкцій застосунку.
У формі реєстрації вкажіть доступну та дійсну адресу електронної пошти. Для завершення створення компанії на пошту власника прийде код валідації. Цей код необхідно ввести на останньому етапі реєстрації. Після валідації компанія створюється автоматично. Чекати на додаткове підтвердження не потрібно.
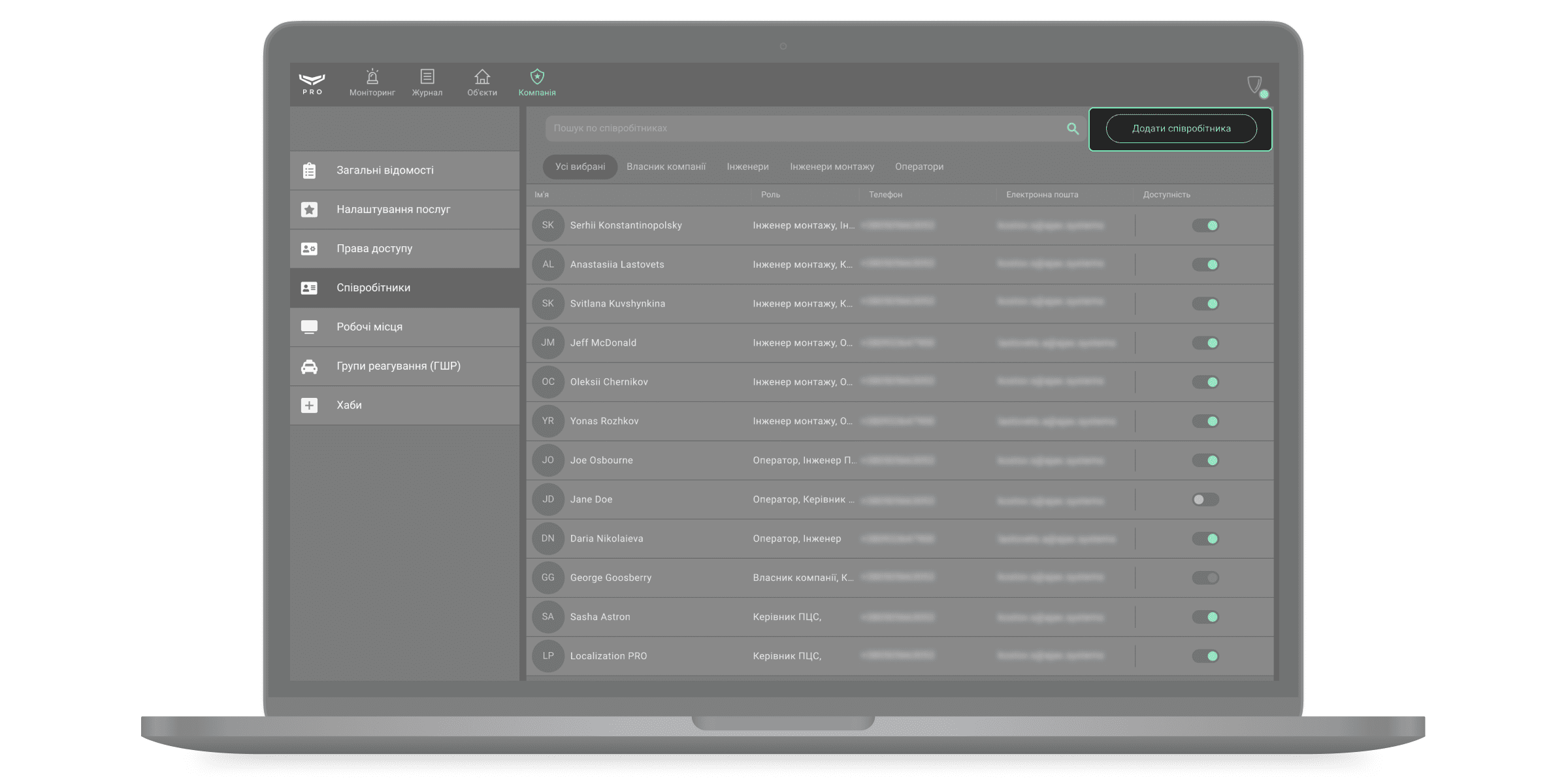
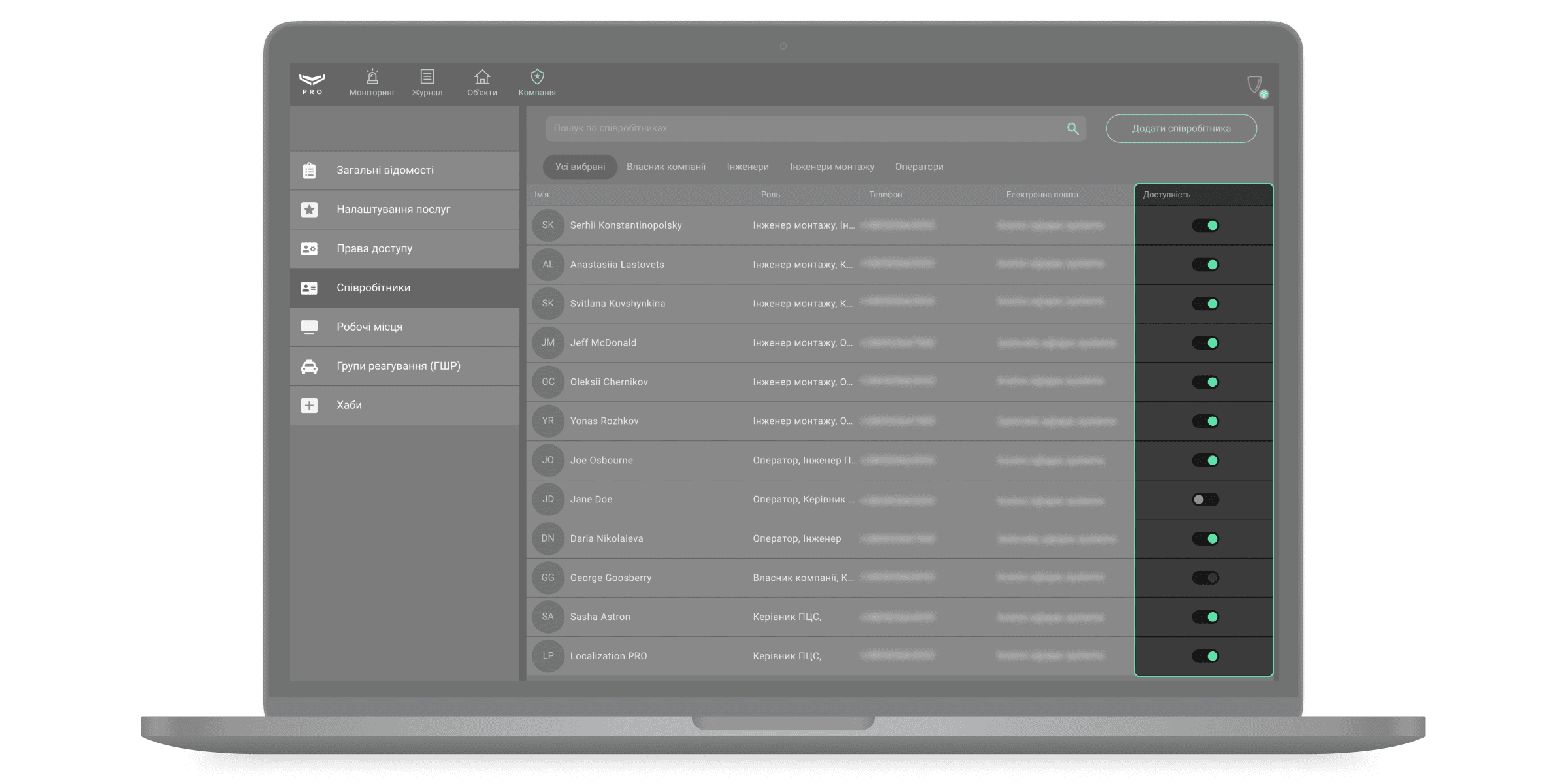
Співробітники
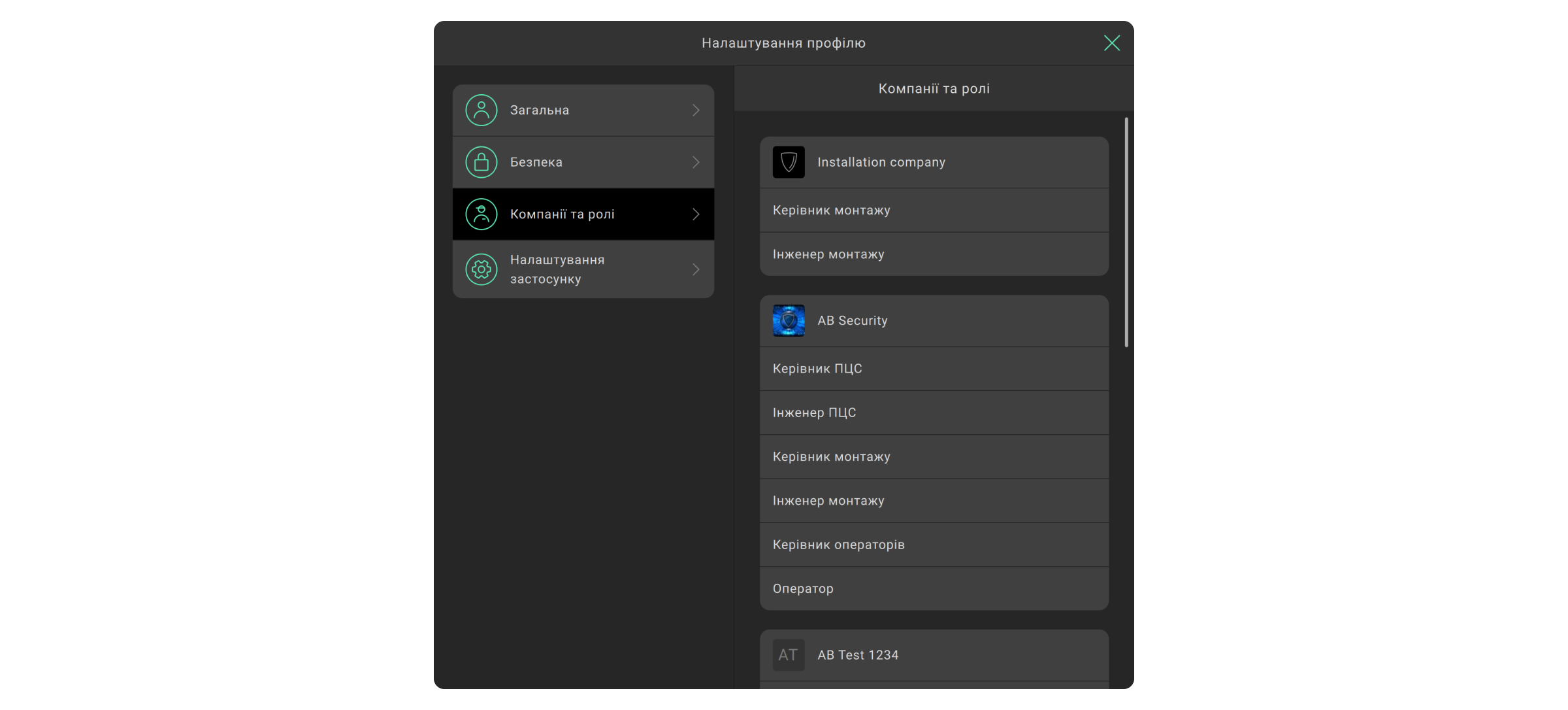
Додати співробітників або змінити ролі вже підключених PRO-акаунтів можна в меню Співробітники (модуль Компанія → меню Співробітники). Додати можна лише співробітника, який вже має PRO-акаунт. Акаунт має бути зареєстрований у будь-якому з цих двох застосунків: Ajax PRO Desktop або Ajax PRO: Tool for Engineers.
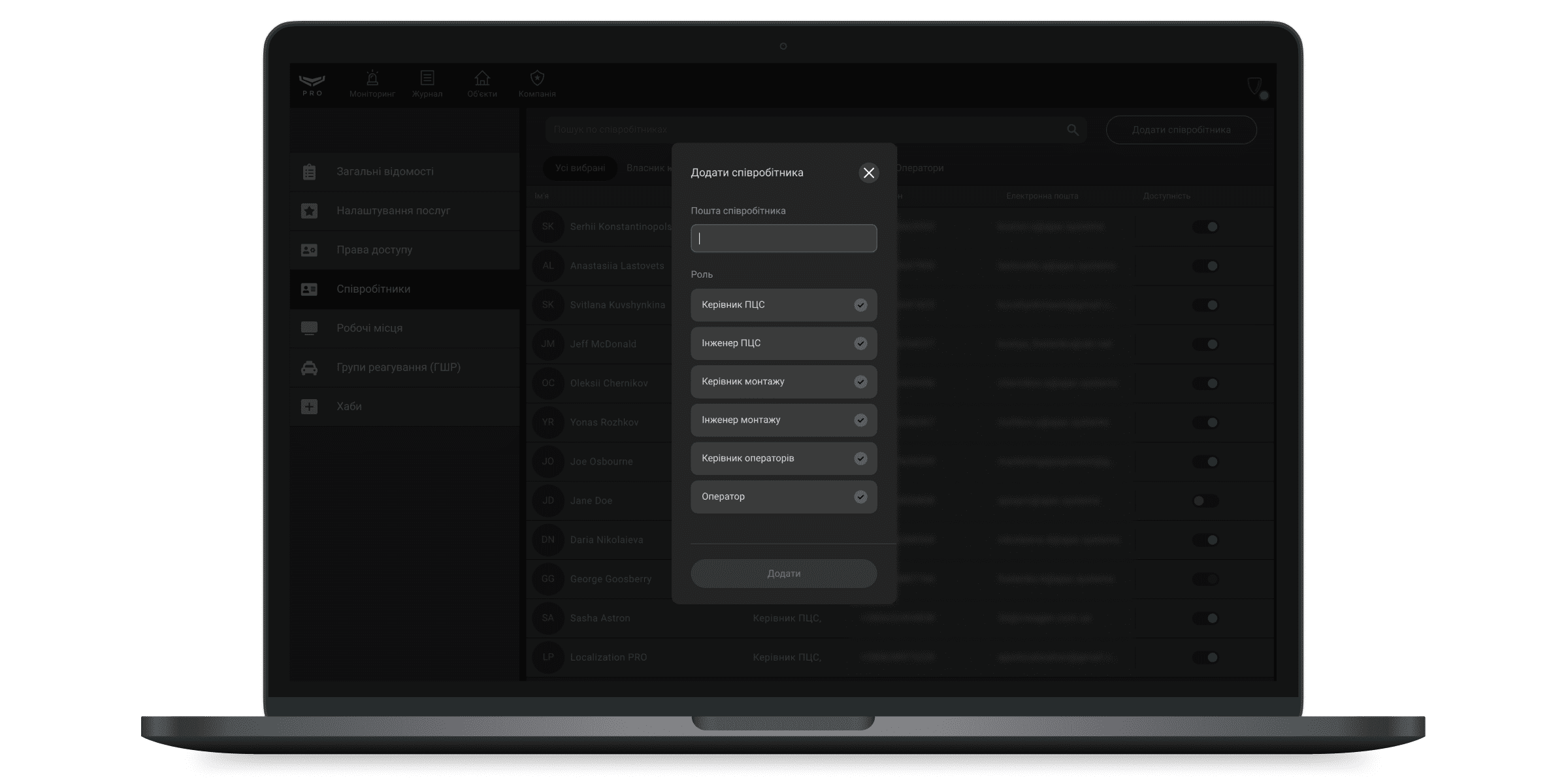
Ролі співробітників
Якщо вибрано тип послуг Моніторинг тривог:
- Власник компанії
- Керівник ПЦС
- Інженер ПЦС
- Керівник операторів
- Оператор
- Старший менеджер сервісів Ajax
- Менеджер сервісів Ajax
Якщо вибрано тип послуг Монтаж та обслуговування:
- Власник компанії
- Керівник монтажу
- Інженер монтажу
Якщо вибрано обидва типи послуг: доступні всі ролі співробітників.
Права та доступи співробітників
Як додати співробітника, змінити його дані або відключити його
Щоб додати співробітника, у нього має бути зареєстрований PRO-акаунт.
Щоб додати співробітника, у Ajax PRO Desktop:
- Перейдіть у модуль Компанія.
- Перейдіть до меню Співробітники.
- Натисніть Додати співробітника.
- Введіть email-адресу, на яку зареєстровано PRO-акаунт співробітника.
- Визначте роль співробітника.
- Натисніть Додати.
Після додавання власник PRO-акаунта отримає email зі сповіщенням. Додавання співробітника буде зафіксовано у журналі подій Ajax PRO Desktop.
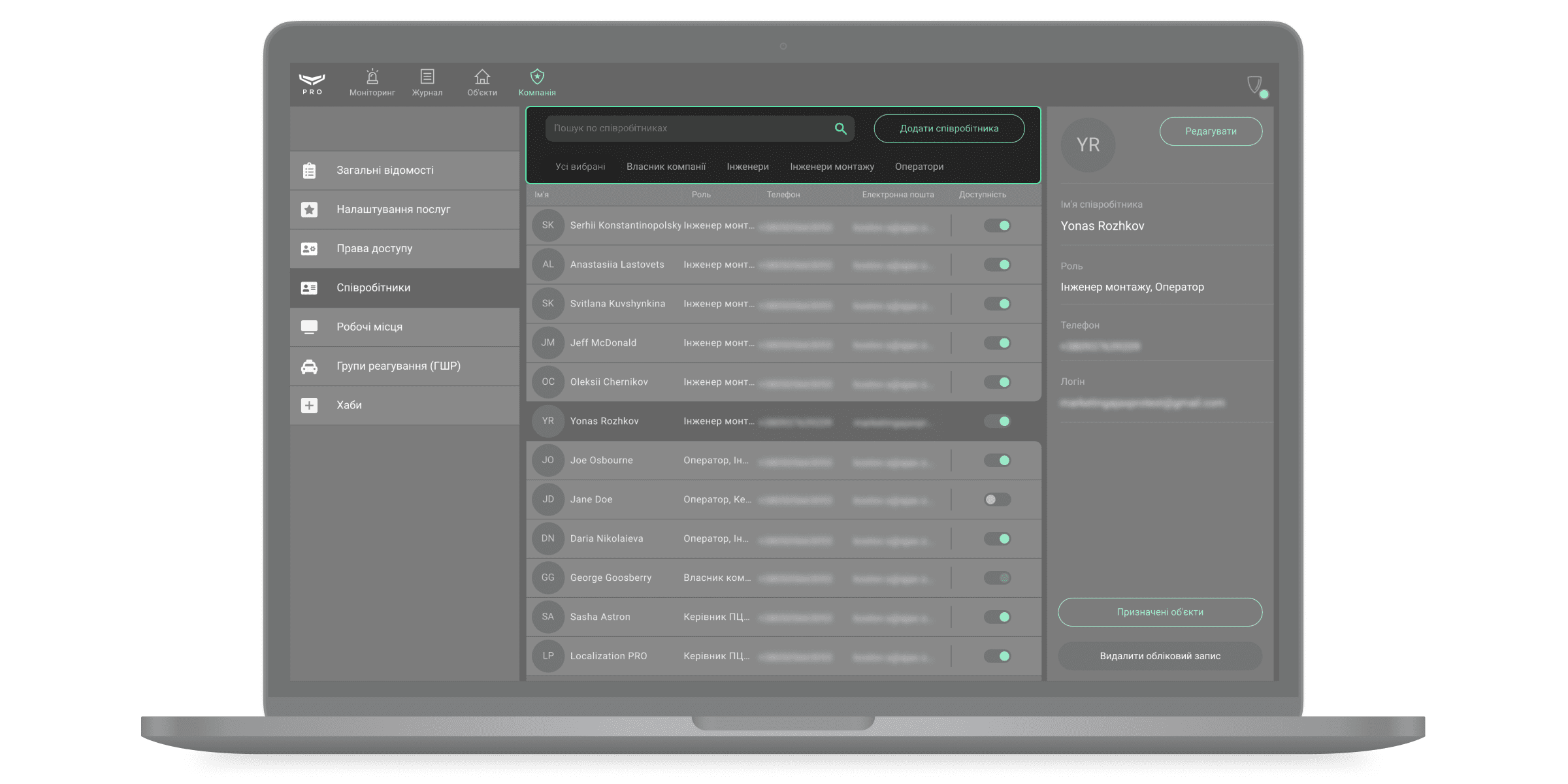
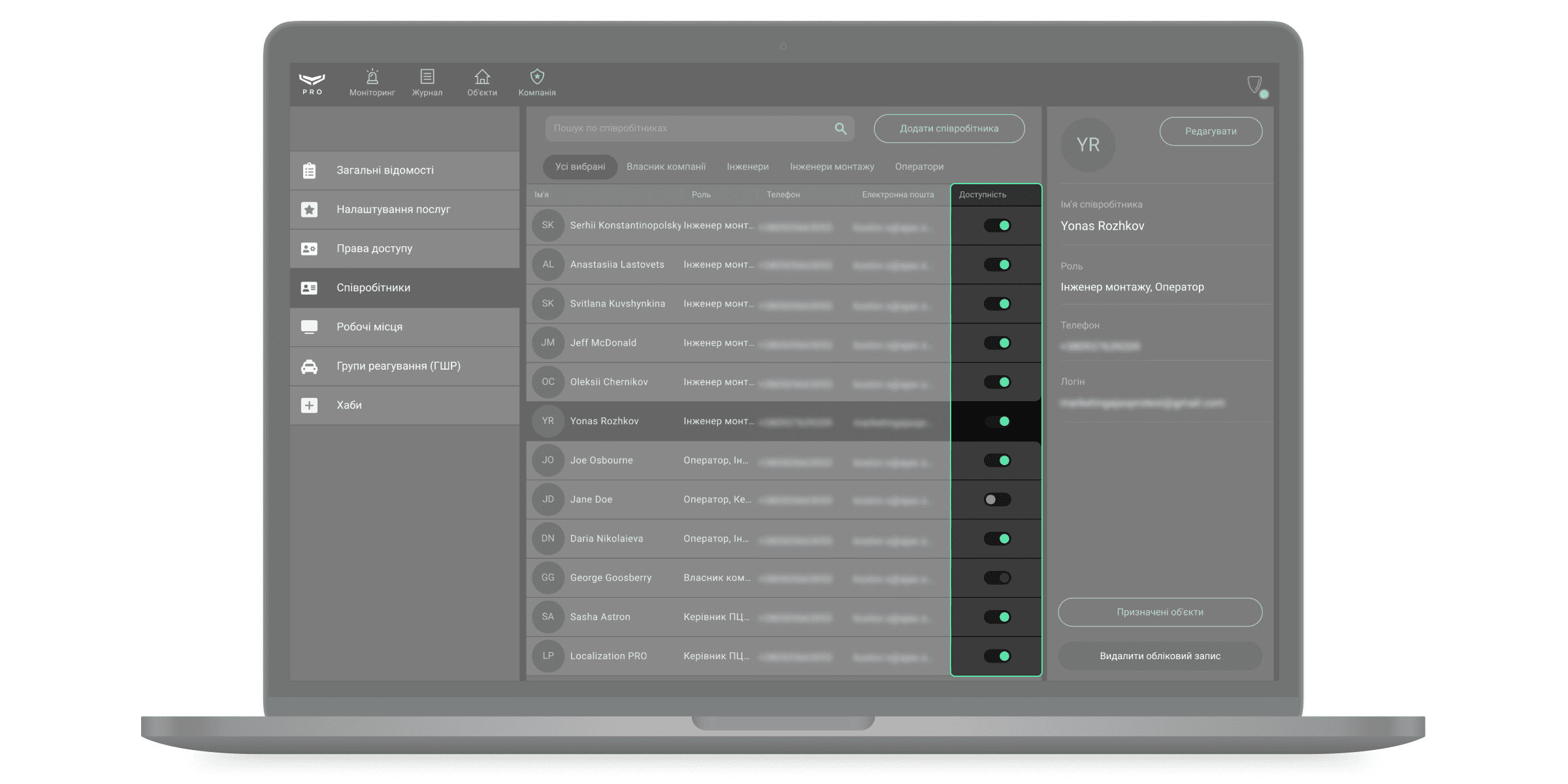
Щоб відредагувати дані або видалити PRO-акаунт співробітника, виберіть його зі списку. Праворуч з’явиться вікно з деталями та кнопками Редагувати та Видалити обліковий запис.
Щоб знайти співробітника, скористайтеся фільтрами або пошуком за ім’ям, телефоном та електронною поштою.
Ajax PRO Desktop дозволяє тимчасово відключити PRO-акаунт співробітника, не видаляючи його з системи — на випадок відпустки або лікарняного. Для цього переведіть перемикач навпроти імені співробітника у неактивний стан. Тимчасово відключений співробітник не має доступу до модулів компанії Ajax PRO Desktop.
Налаштування приватності
Знімання та перегляд фото за запитом, перегляд трансляції з камер наживо або їх архіву доступні для профілю компанії в застосунку Ajax PRO Desktop, якщо компанії надані відповідні права доступу.
Щоб призначити доступ певному типу співробітників компанії, Керівник компанії або Керівник ПЦС змінює стан опції Перегляд фото за тривогою та фото за сценаріями тривоги в налаштуваннях прав доступу компанії.
Доступ охоронної компанії до фото за запитом і перегляду відео з камер спостереження наживо чи з архіву налаштовується адміністратором у застосунку Ajax. Також є можливість надати тимчасовий доступ співробітникам компанії до відеопристроїв лише після тривоги.
Знімки або відео дають змогу підтвердити тривогу на обʼєкті, що охороняється. Користувач встановлює, за якої умови співробітники компанії в Ajax PRO Desktop можуть робити фото за запитом або переглядати відео: у будь-який момент, коли доступні пристрої перебувають під охороною або лише протягом певного часу після тривоги.
За запитом, адміністратор може налаштувати тимчасовий доступ до відеопотоку для інженера монтажу. Це дає змогу налаштувати систему Ajax без загроз приватності. Надіслати запит на тимчасовий доступ до відео інженер монтажу може за допомогою застосунків Ajax PRO Desktop та Ajax PRO: Tool for Engineers.
Модулі, меню та можливості Ajax PRO Desktop
Ajax PRO Desktop дозволяє:
- Керувати PRO-акаунтами співробітників — модуль Компанія, меню Співробітники, меню Групи реагування (ГШР).
- Адмініструвати необмежену кількість систем Ajax — модуль Об’єкти.
- Вести клієнтську базу об’єктів — модуль Об’єкти та меню Хаби в модулі Компанія.
- Отримувати, розподіляти між операторами й обробляти тривоги систем Ajax — модуль Моніторинг.
- Закріплювати робочі місця за операторами — модуль Компанія, меню Робочі місця.
- Формувати звіти доступності хабів та операторів (ПЦС) — модуль Журнал.
- Координувати роботу груп швидкого реагування (ГШР) — модуль Моніторинг.
- Вести журнал подій та тривог систем безпеки — модуль Журнал.
Компанія
Доступ до модуля: Власник компанії, Інженер ПЦС, Керівник ПЦС, Керівник операторів, Оператор, Інженер монтажу, Керівник монтажу.
Модуль Компанія містить меню та налаштування для таких завдань:
- Загальні відомості — переглянути інформацію про компанію. Редагувати може лише власник компанії.
- Налаштування послуг — вибрати тип послуг компанії, термін зберігання медіафайлів, рівень доступу до об’єктів і хабів та інші налаштування.
- Підключення до ПЦС — керувати приймачами, що є проміжними ланками між ПЦС та хмарним сервером (доступне для Керівника ПЦС та Інженера ПЦС).
- Права доступу — надати дозвіл робити та переглядати фото за запитом, формувати звіти про роботу систем, що обслуговуються.
- Співробітники — керувати обліковими записами співробітників.
- Робочі місця — облік комп’ютерів (ПК), на яких працюють оператори. Допомагає розраховувати доступність ПЦС та моніторити вхід операторів до PRO-акаунта зі сторонніх пристроїв.
- Групи реагування (ГШР) — адмініструвати групи швидкого реагування.
- Хаби — керувати хабами компанії. Меню містить об’єкти в Ajax Translator (якщо такі підключені), запити на моніторинг, запити на зняття з моніторингу.
- Шаблони налаштувань — створювати та редагувати шаблони для швидкого застосування кількох налаштувань одночасно.
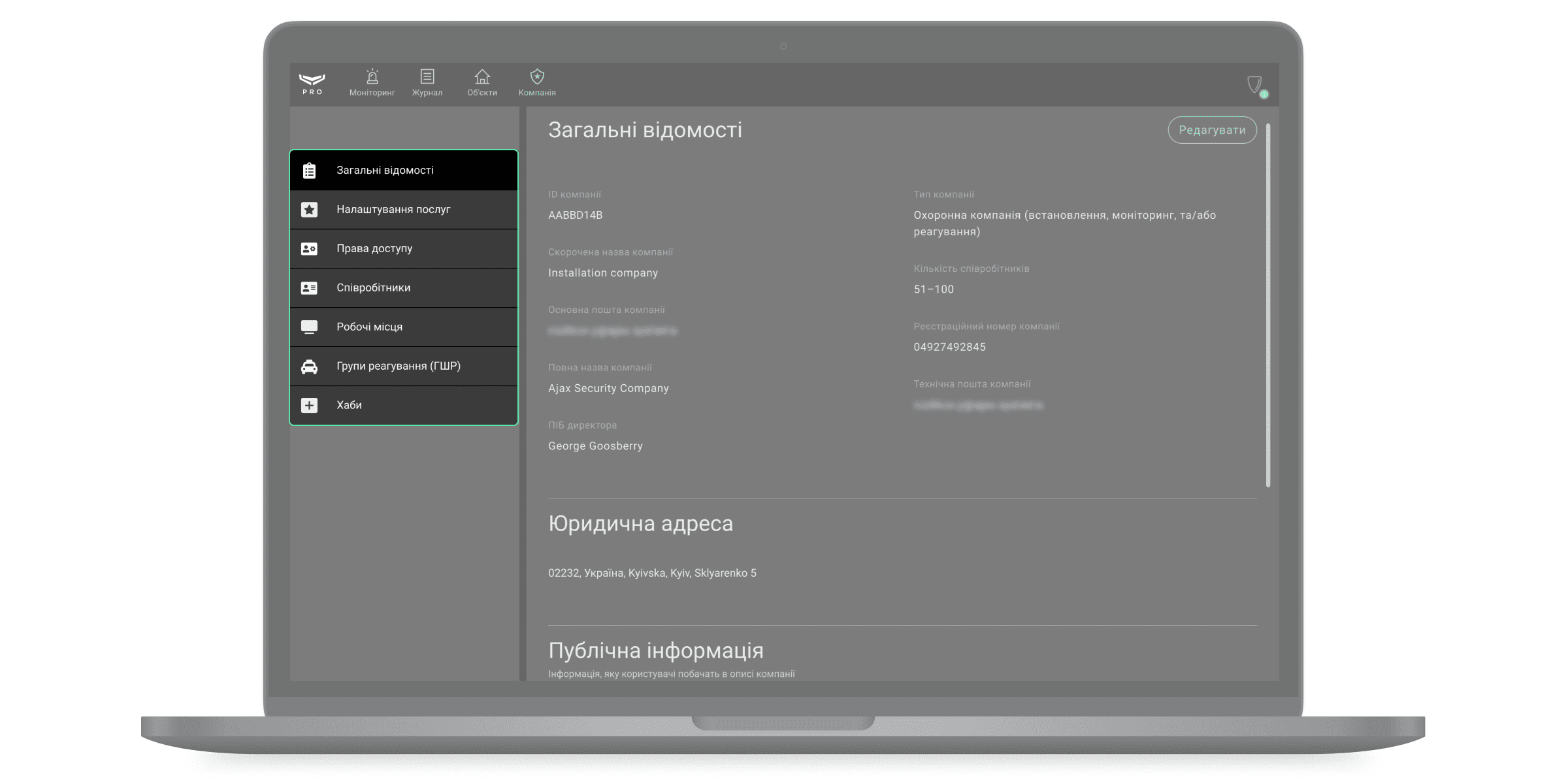
Загальні відомості
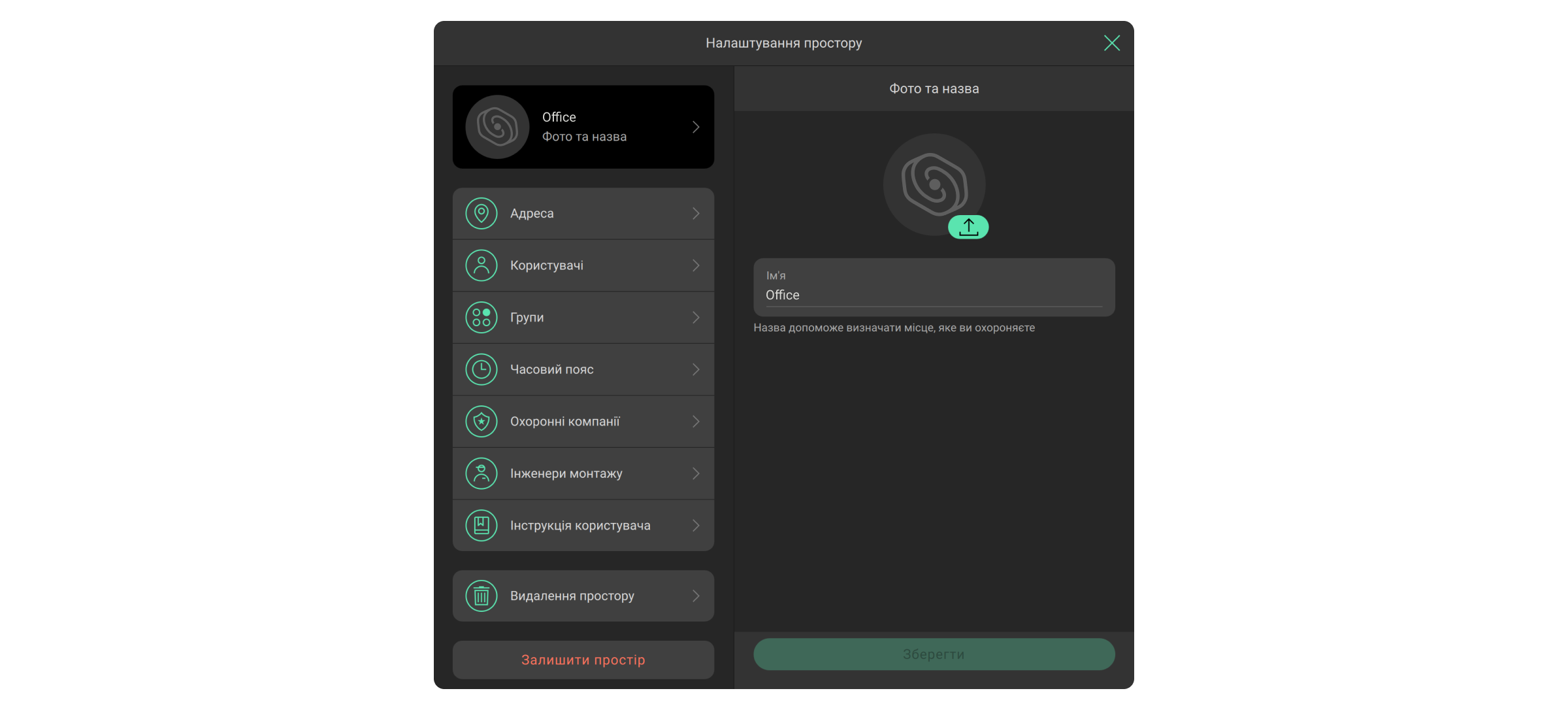
Меню містить інформацію про компанію. Змінити відомості про компанію може власник компанії, для цього слід натиснути кнопку Редагувати. Застосунок дозволяє змінити всі дані про компанію, крім її назви та власника. Щоб змінити назву компанії — зверніться до служби технічної підтримки Ajax. Щоб застосувати внесені зміни, клацніть Зберегти зміни, або скасуйте їх кнопкою Скасувати.
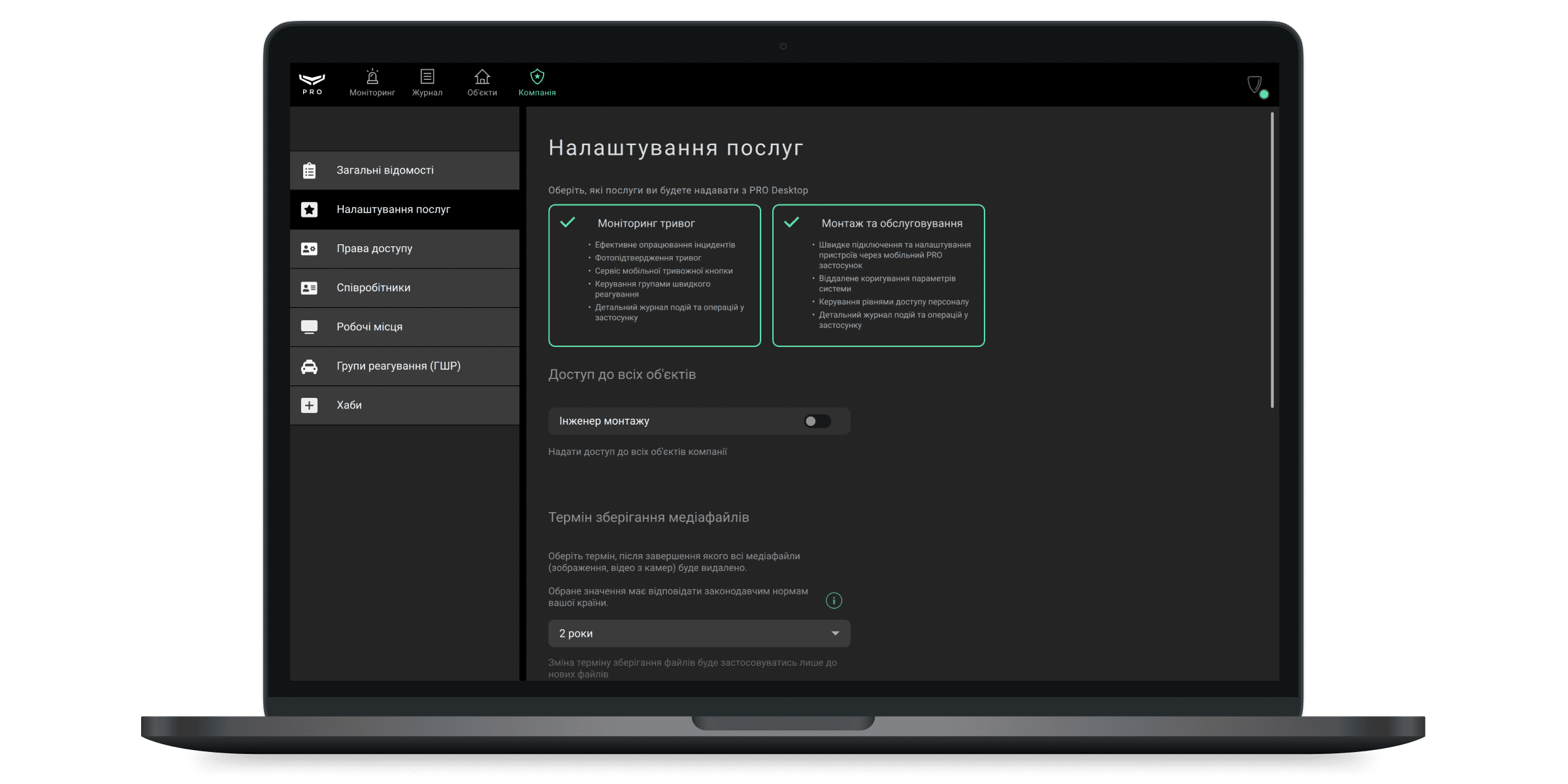
Налаштування послуг
У меню можна встановити тип послуг, які надає компанія, та керувати іншими налаштуваннями системи (доступ до об’єктів, термін зберігання медіафайлів, звіти про роботу системи). Власник компанії вибирає тип послуг компанії під час реєстрації у застосунку та може змінити тип послуг у будь-який момент.
Доступ співробітників до об’єктів
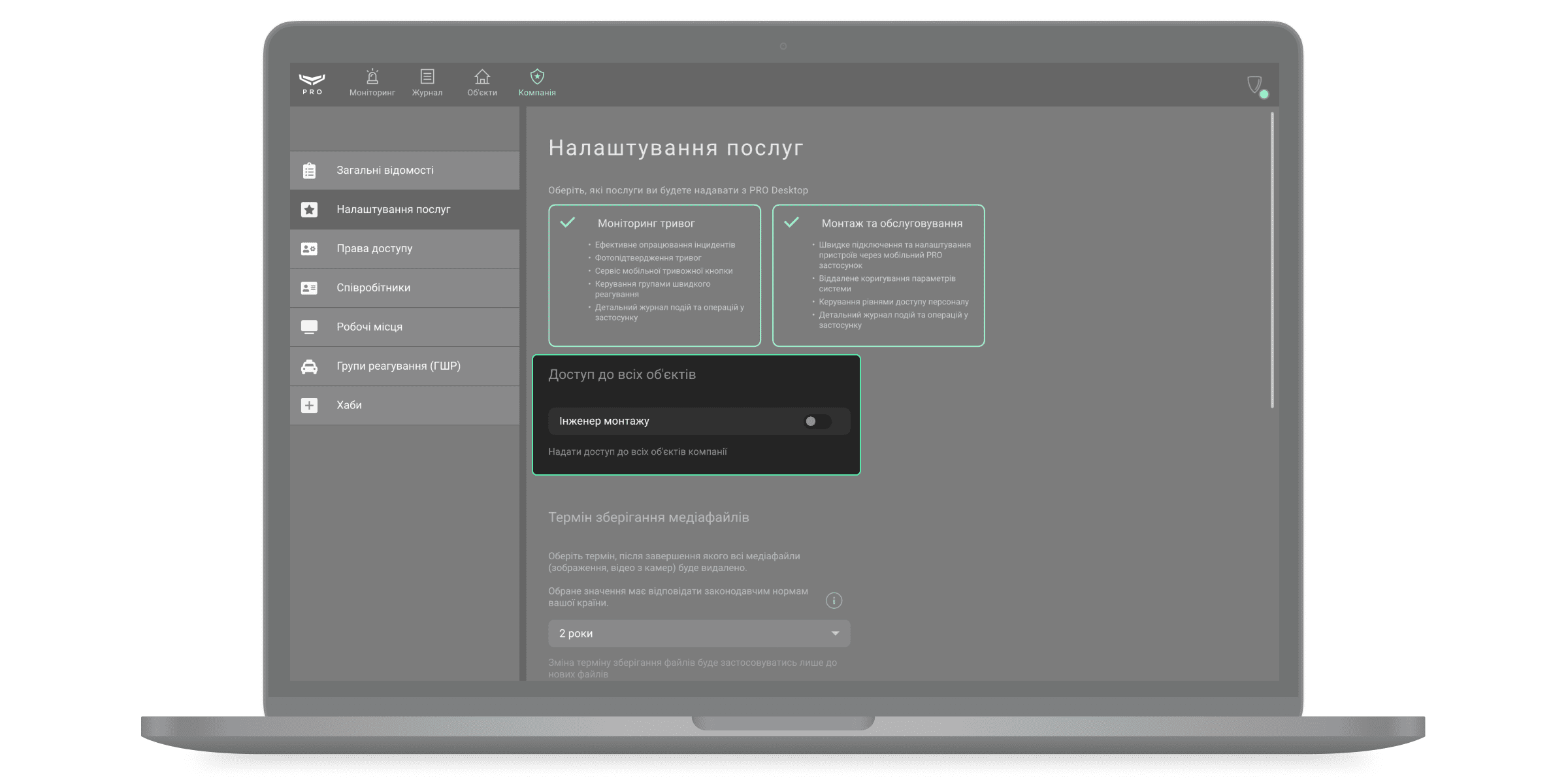
За початкових налаштувань, співробітник з роллю Інженер монтажу має доступ до тих об’єктів, які визначає йому Керівник монтажу. Щоб інженер монтажу міг налаштовувати всі підключені до компанії об’єкти, потрібно увімкнути опцію Доступ до всіх об’єктів.
Для цього, у Ajax PRO Desktop:
- Перейдіть у модуль Компанія.
- Відкрийте меню Налаштування послуг.
- У полі Доступ до всіх об’єктів увімкніть опцію для Інженерів монтажу.
Тепер в інженера монтажу та у компанії однакові права на налаштування всіх об’єктів. Права можуть бути такими:
- Постійний доступ до налаштувань системи.
- Тимчасовий доступ: можна налаштовувати систему протягом заданого часу, від 1 до 8 годин.
- Немає доступу до налаштувань системи.
Вимагати номер об’єкта для запитів на моніторинг
Опція доступна лише для моніторингових компаній і вимкнена за початкових налаштувань. Коли опція ввімкнена, компанія отримає запит на моніторинг, тільки якщо вказано номер обʼєкта. Якщо опція активована, надсилати запит на моніторинг можуть лише PRO або співробітники компаній у застосунку Ajax PRO.
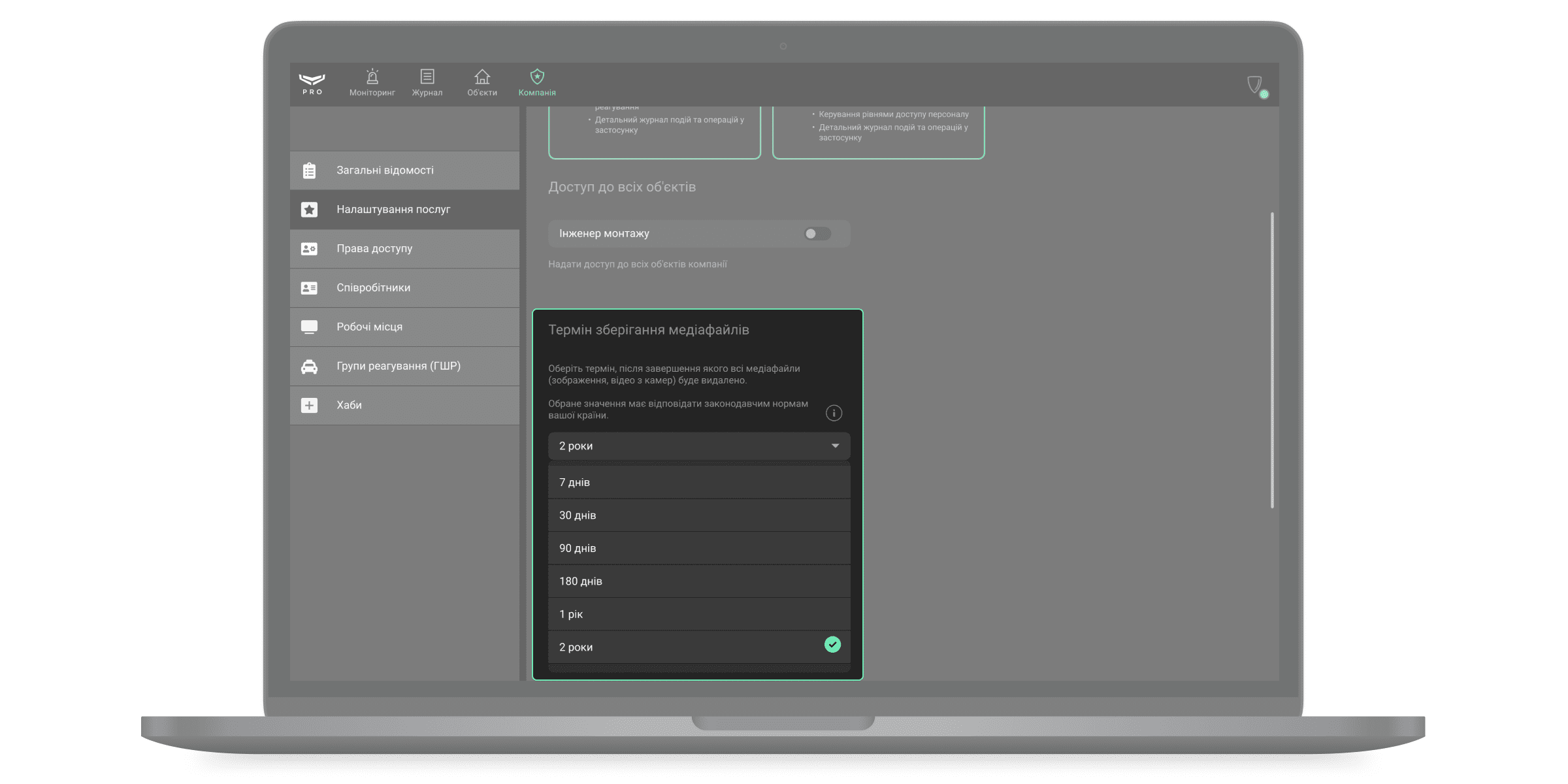
Термін зберігання медіафайлів
Можна налаштувати період, після якого всі медіафайли (зображення, відео з камер) будуть видалені. Новий термін зберігання медіафайлів застосовується лише до файлів, що створено після внесення змін.
Доступний термін зберігання медіафайлів:
- 7 днів.
- 30 днів.
- 90 днів.
- 180 днів.
- 1 рік.
- 2 роки.
Вибраний термін зберігання медіафайлів має відповідати законодавству вашого регіону.
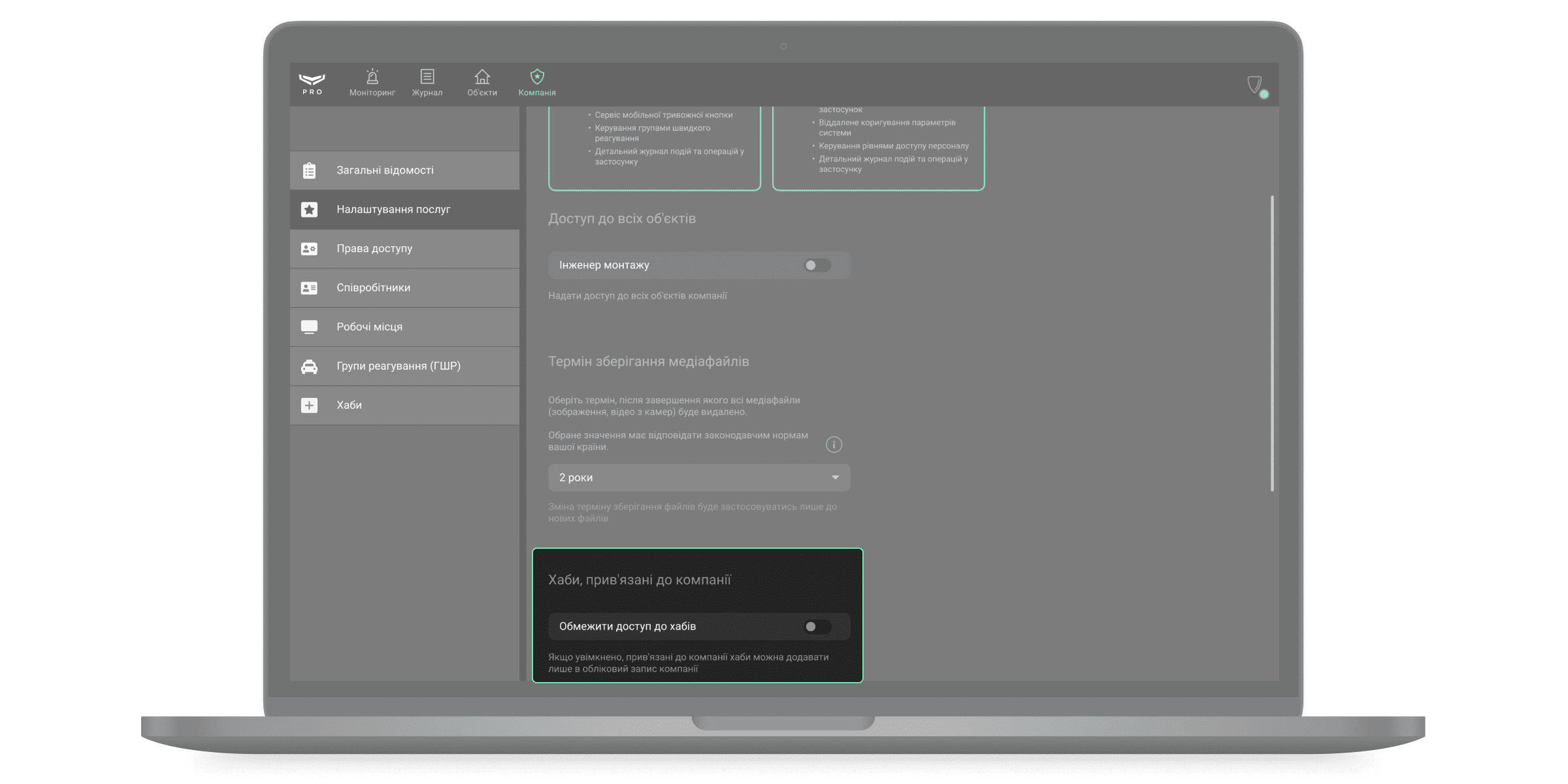
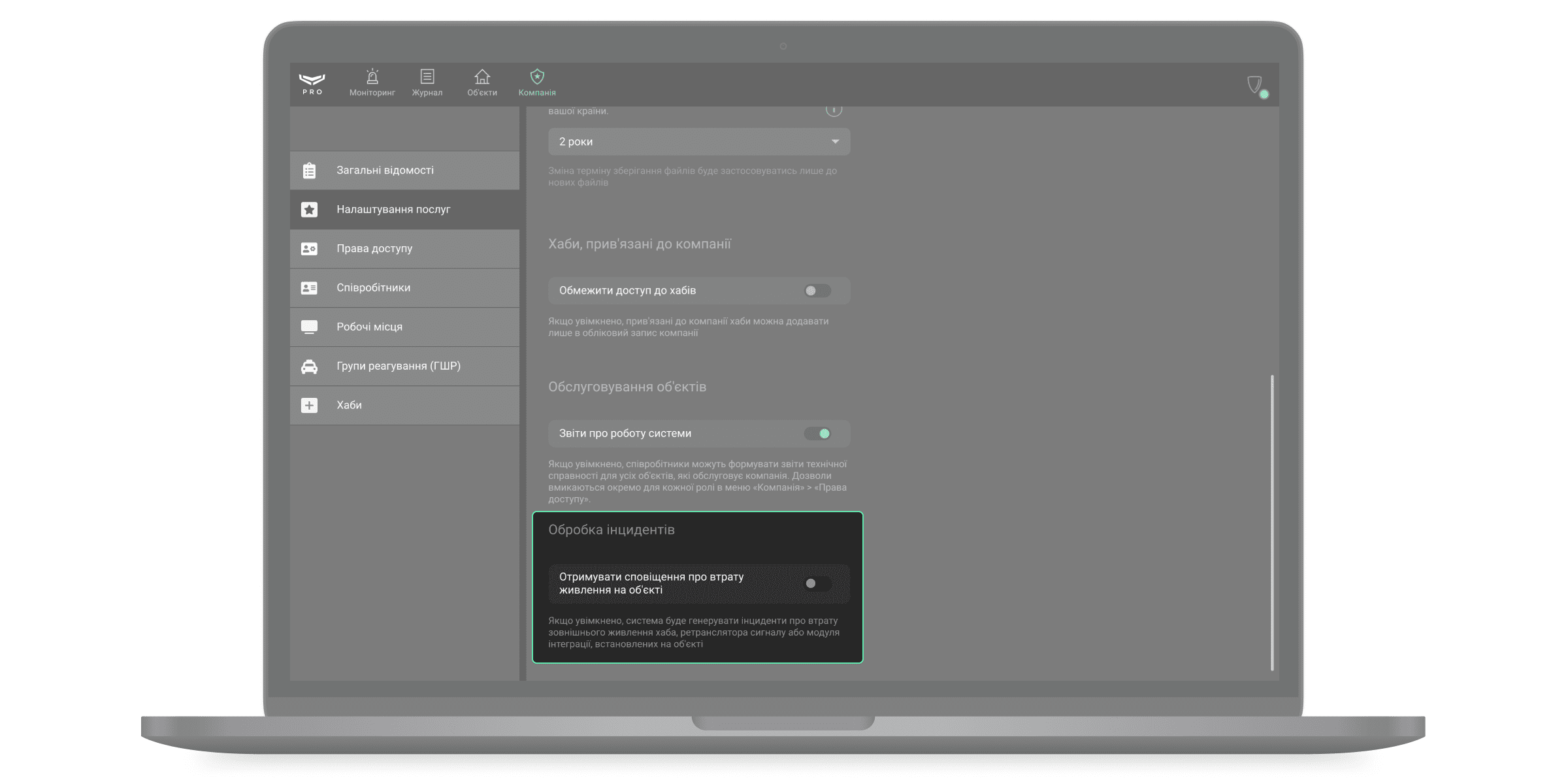
Хаби, прив’язані до компанії
Опцію Обмежити доступ до хабів вимкнено за початкових налаштувань. Коли вона увімкнена, прив’язані до компанії хаби можна додавати тільки в обліковий запис цієї компанії. Додавання до облікових записів інших компаній неможливе. Зверніться до служби технічної підтримки Ajax або вашого менеджера Ajax, щоб дізнатися більше про цю функцію.
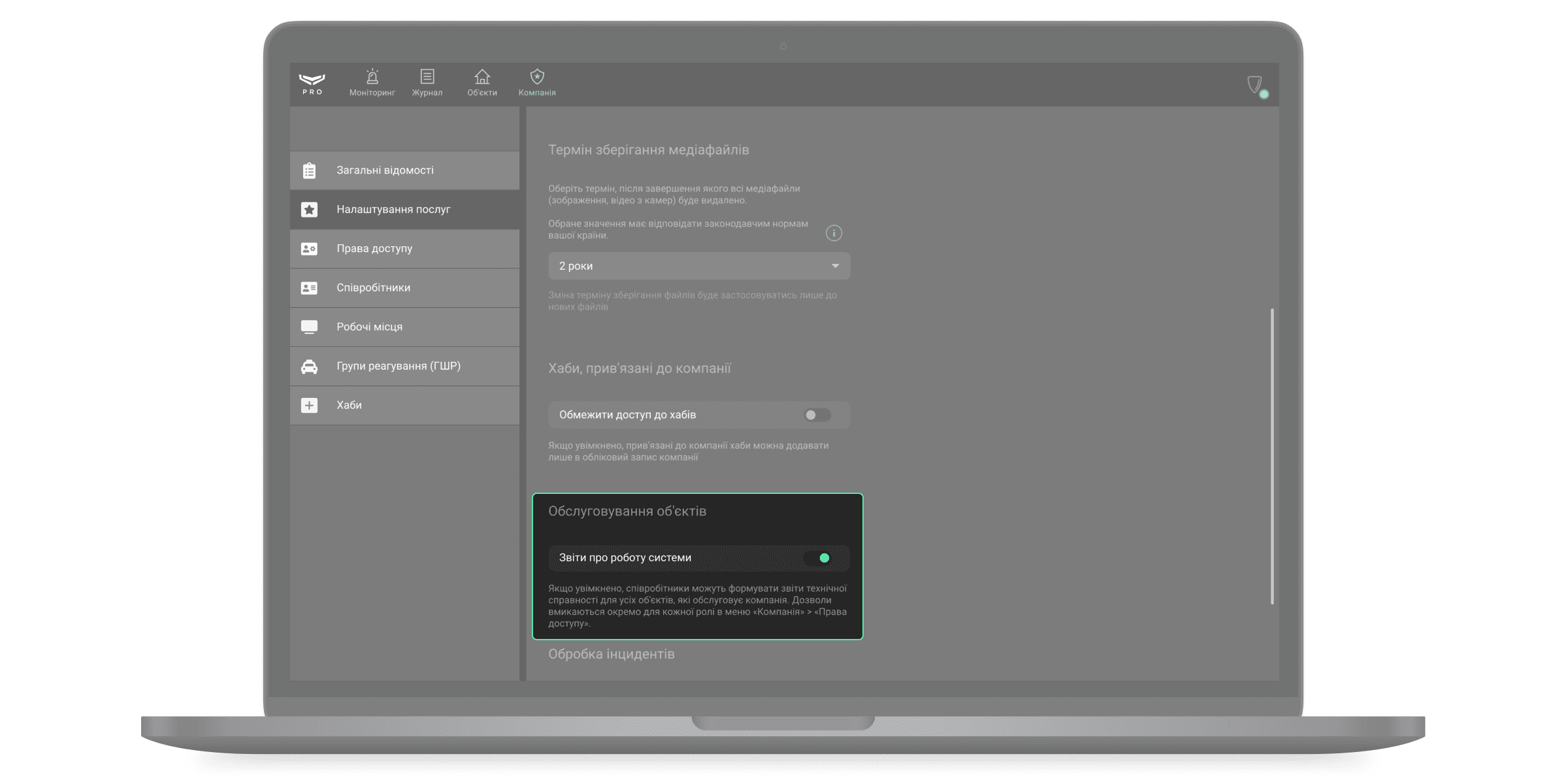
Обслуговування об’єктів
Якщо увімкнено опцію Звіти про роботу системи, співробітники компанії можуть формувати звіти технічної справності охоронних пристроїв та пожежних датчиків системи. Такі звіти можуть генерувати й завантажувати лише ті ролі, яким власник компанії дав відповідне право. Право призначається в меню Права доступу.
За початкових налаштувань звіти про роботу системи вимкнені. Співробітник із роллю Інженер монтажу не може формувати звіти технічної справності тих об’єктів, до яких він не має доступу.
Обробка інцидентів
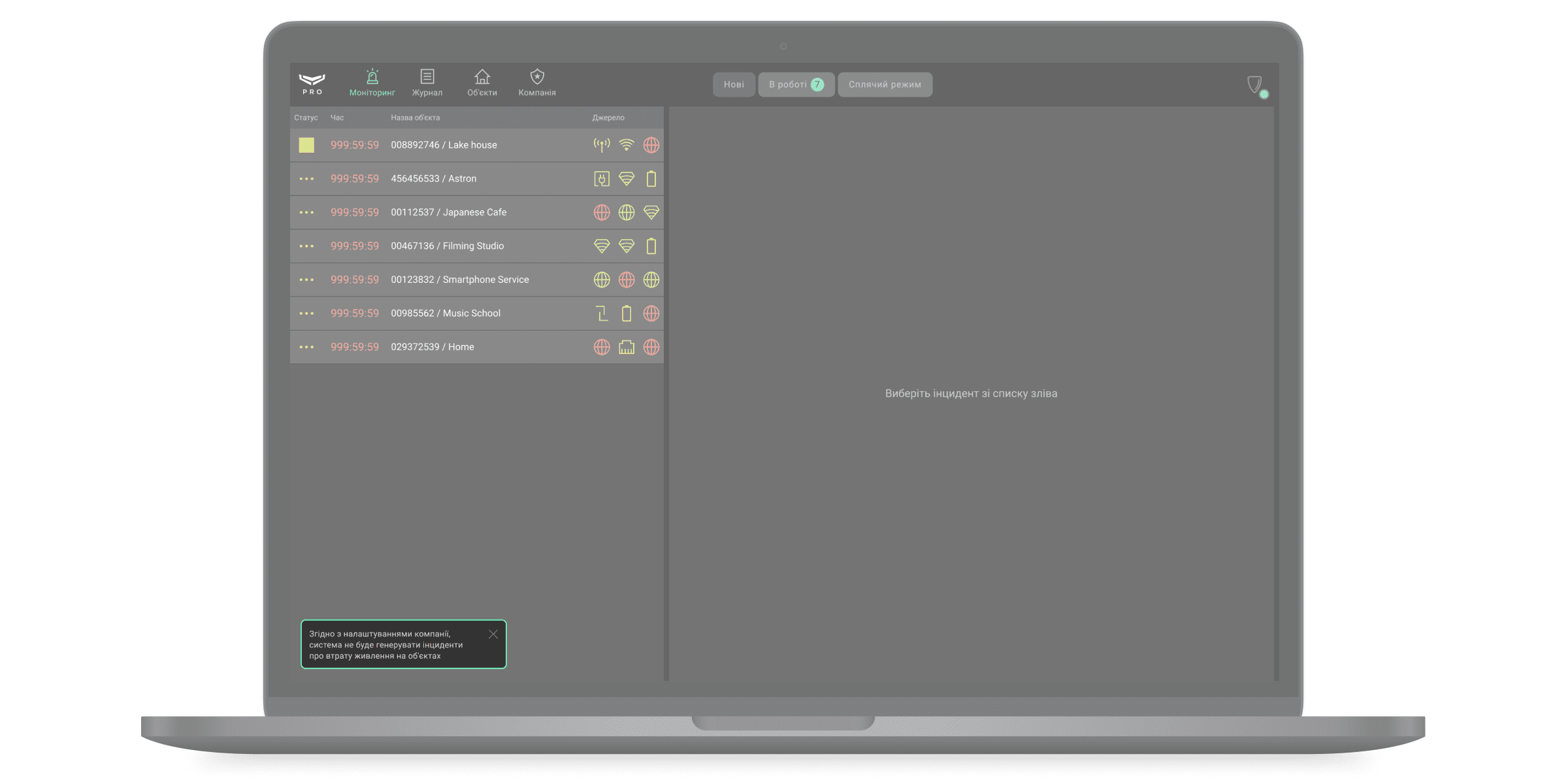
Опція Отримувати сповіщення про втрату живлення на об’єкті увімкнена за початкових налаштувань. Коли опцію вимкнено, система не буде генерувати інциденти про втрату зовнішнього живлення хаба, ретранслятора радіосигналу або модуля інтеграції, встановлених на об’єкті.
Після вимкнення опції у модулі Моніторинг з’явиться повідомлення: ««Згідно з налаштуваннями компанії, система не буде генерувати інциденти про втрату живлення на об’єктах».
Підключення до ПЦС
Моніторинг через Ajax Cloud — функція, що допомагає встановити звʼязок між системою Ajax і стороннім софтом для моніторингу. Ця функція є проміжною ланкою між простором і пультом моніторингу, оскільки перетворює отримані сповіщення на протокол подій, який підтримує софт ПЦС.
Моніторинг через Ajax Cloud дає змогу передавати події на ПЦС безпосередньо з сервера Ajax. Моніторингові компанії і компанії, що встановлюють системи безпеки та реагують на їхні тривоги й події, можуть використовувати Ajax PRO Desktop, щоб налаштовувати й підключати системи безпеки. Охоронні й моніторингові компанії можуть використовувати застосунок, щоб організовувати ПЦС.
Коли ПЦС підключений до системи за допомогою моніторингу через Ajax Cloud, моніторингові компанії можуть відкривати та переглядати відео з відеопристроїв Ajax. Відео записується безпосередньо в Ajax PRO Desktop, щойно вбудований датчик руху камери або функція розпізнавання об’єктів за допомогою ШІ активує тривогу.
Коли спрацьовує відеопристрій Ajax, ПЦС отримує URL-адресу, яка відкриває нове вікно браузера. За цим посиланням оператор потрапляє на віджет відеостіни Ajax PRO Desktop, який відображає два відеопотоки: відео наживо і фрагмент відео в записі.
Ajax Translator PRO — це плагін для підключення систем Ajax до стороннього софту для моніторингу. Він автоматично конвертує події Ajax у протоколи, сумісні з пультом центрального спостереження, забезпечуючи стабільну взаємодію систем Ajax із ПЦС.
Ajax Translator PRO — це вдосконалена версія застосунку Ajax Translator, який має обмежену продуктивність і функціональність. Система Ajax дає змогу користувачам самостійно експортувати обʼєкти, привʼязані до Ajax Translator. Цей застосунок генерує CSV-файл, що містить ідентифікатор хаба та номер облікового запису активних привʼязок. Файл можна завантажити в Ajax PRO Desktop до вибраного приймача Translator або Cloud signaling.
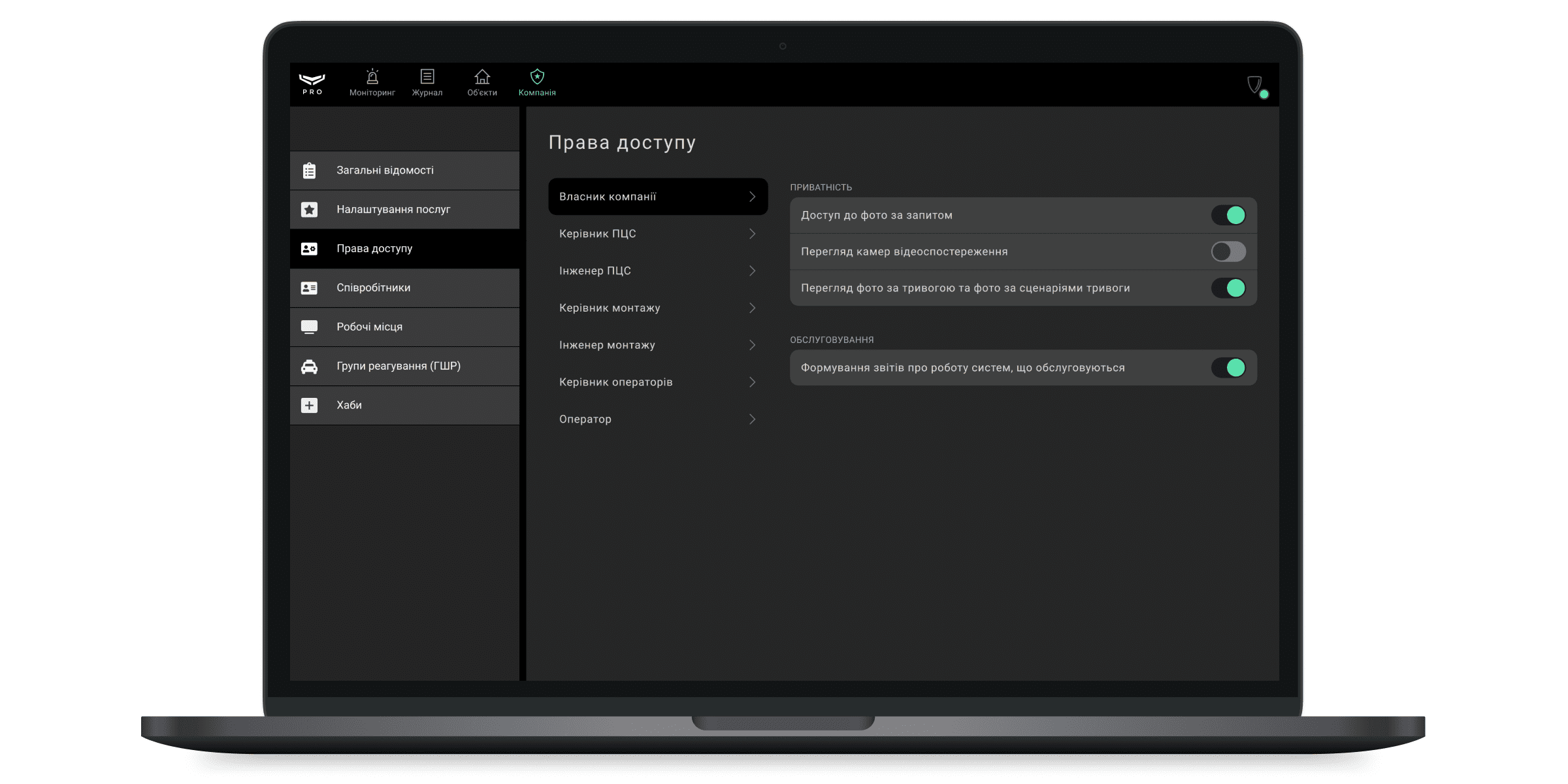
Права доступу
У меню Права доступу власник компанії, керівник ПЦС та керівник монтажу можуть регулювати права доступу для ролей співробітників. Якщо керівник призначив доступ певному типу співробітників, усі співробітники з цією роллю матимуть відповідне право.
В цьому меню можна увімкнути або вимкнути такі права:
| Власник компанії | Керівник ПЦС | Керівник монтажу | |
| Знімати та переглядати фото за запитом та у сценаріях за розкладом | + | + | – |
| Переглядати фото за тривогою та фото за сценаріями тривоги | + | + | – |
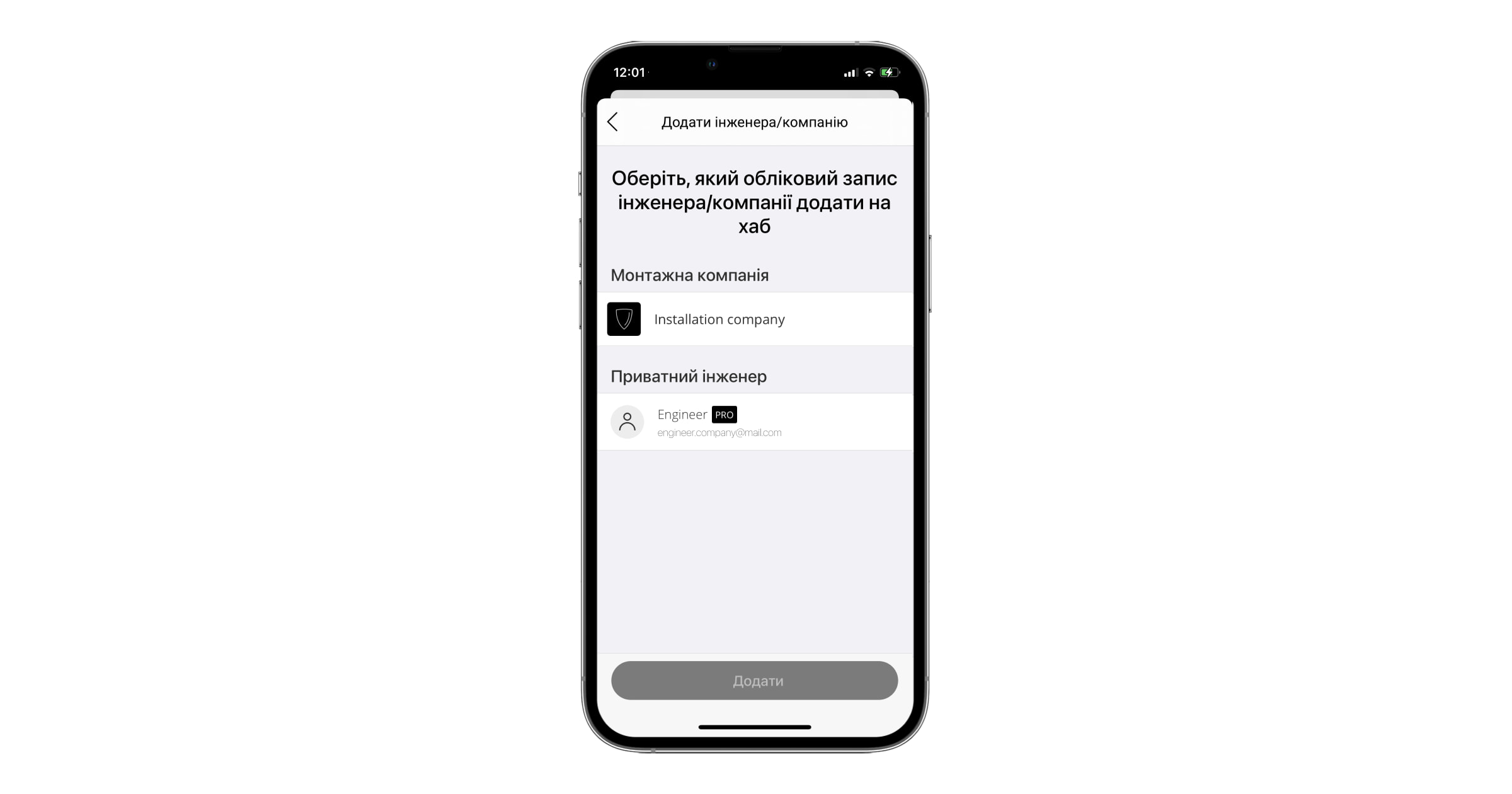
| Додавати інженера/компанії або охоронну компанію | + | – | + |
| Призначати адміністраторів | + | – | + |
| Надавати адміністратору доступ до налаштуваннь системи | + | – | + |
| Змінювати режим охорони обʼєкта | + | + | + |
| Переглядати трансляції наживо зі сторонніх камер відеоспостереження | + | + | – |
| Переглядати трансляції наживо з камер Ajax зі звуком та без звуку | + | + | – |
| Переглядати архів камер Ajax | + | + | – |
| Використовувати PTZ (панорамування, нахил, зум) | + | + | – |
| Приймати та робити виклики через голосовий модуль | + | + | – |
| Замикати та відмикати замок | + | – | – |
| Формувати звіти про роботу систем, що обслуговуються | + | – | – |
| Вивантажувати записи журналу подій та дані обʼєкта | + | – | – |
Якщо керівник надав право на створення звітів про роботу систем для певної ролі, всі співробітники з цією роллю можуть створювати звіти, завантажувати їх, а також матимуть доступ до архіву звітів.
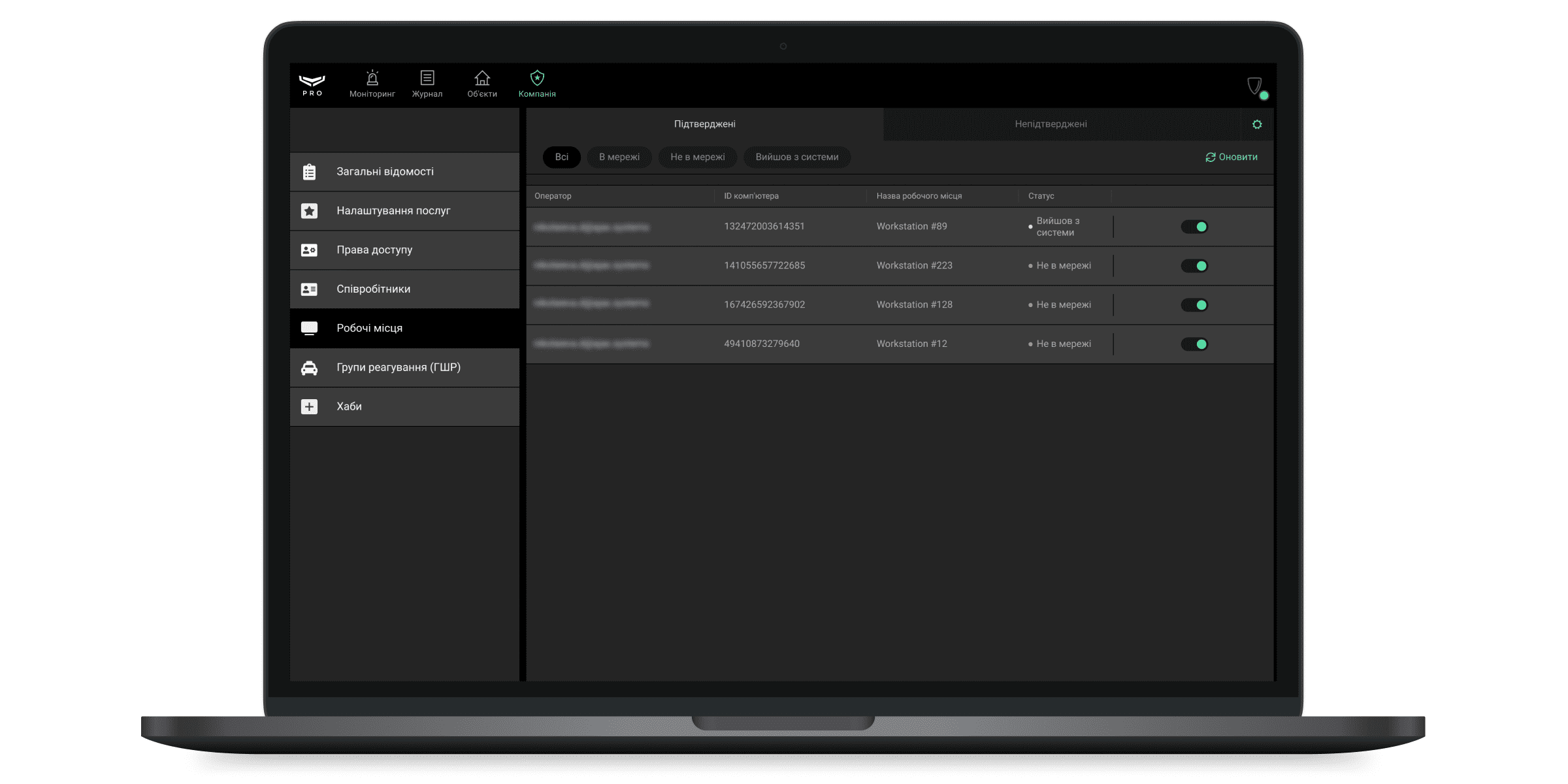
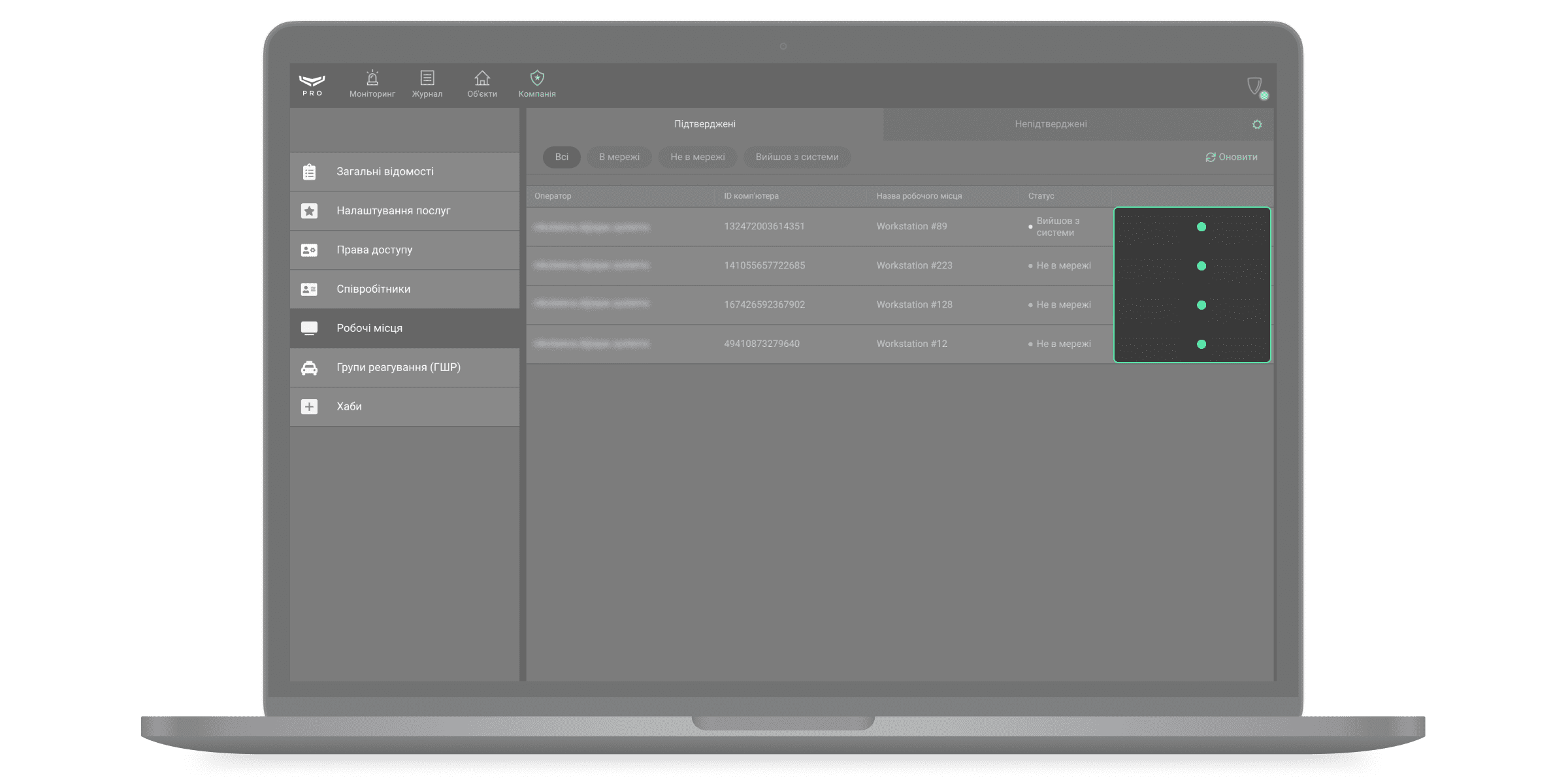
Робочі місця
У меню Робочі місця можна надати кожному комп’ютеру унікальний ідентифікатор (ID комп’ютера) і прив’язати до нього обліковий запис співробітника. Ця інформація використовується для формування звіту про доступність ПЦС.
Щоб закріпити робоче місце за оператором, потрібно підтвердити його вхід до облікового запису. Зробити це можна, якщо натиснути «+» у рядку з електронною поштою оператора у вкладці Непідтверджені. При натисканні на рядок, праворуч відкривається розширена інформація про обліковий запис та кнопка Підтвердити.
При підтвердженні робочого місця необхідно надати йому ім’я — для зручності зображення в журналі подій. ID комп’ютера надається автоматично.
Після підтвердження робочого місця, обліковий запис оператора зображується у вкладці Підтверджені разом з даними про комп’ютер. Робоче місце можна тимчасово вимкнути або видалити — для цього виберіть акаунт у списку і клацніть Видалити з підтверджених.
Для зручності навігації за списком робочих місць передбачено фільтри.
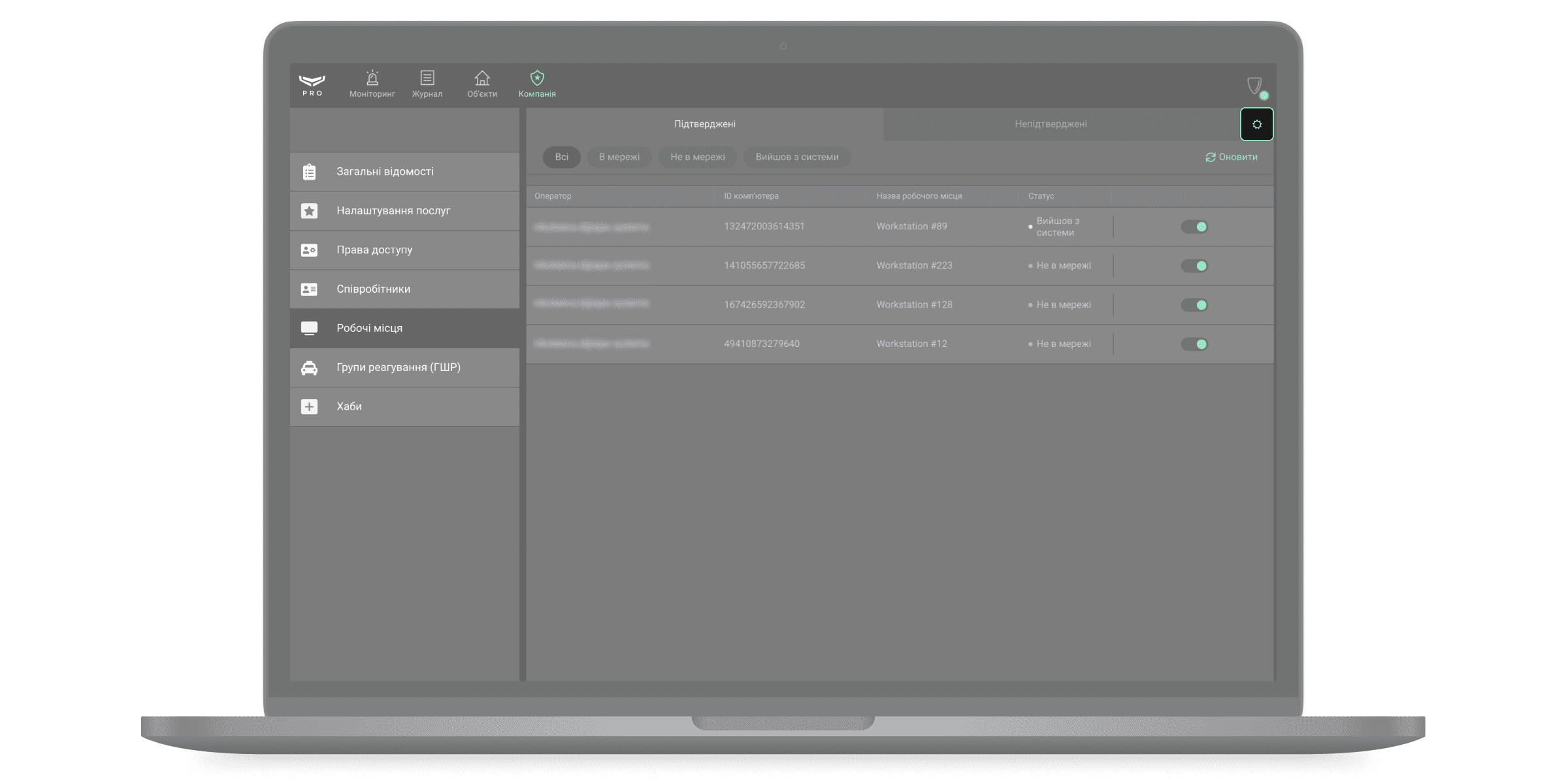
У меню Робочі місця можна налаштувати типи подій, які генерують інциденти. Ajax PRO Desktop повідомляє про інциденти у вкладці Моніторинг. Щоб вибрати події, які генерують інциденти — клацніть на іконку шестерні у вкладці Непідтверджені.
Відкриється вікно, у ньому виберіть типи подій:
- Оператор не в мережі — відсутнє інтернет-з’єднання з комп’ютером оператора.
- Вхід із непідтвердженого комп’ютера — вхід до облікового запису з ПК, який не був підтверджений керівником операторів.
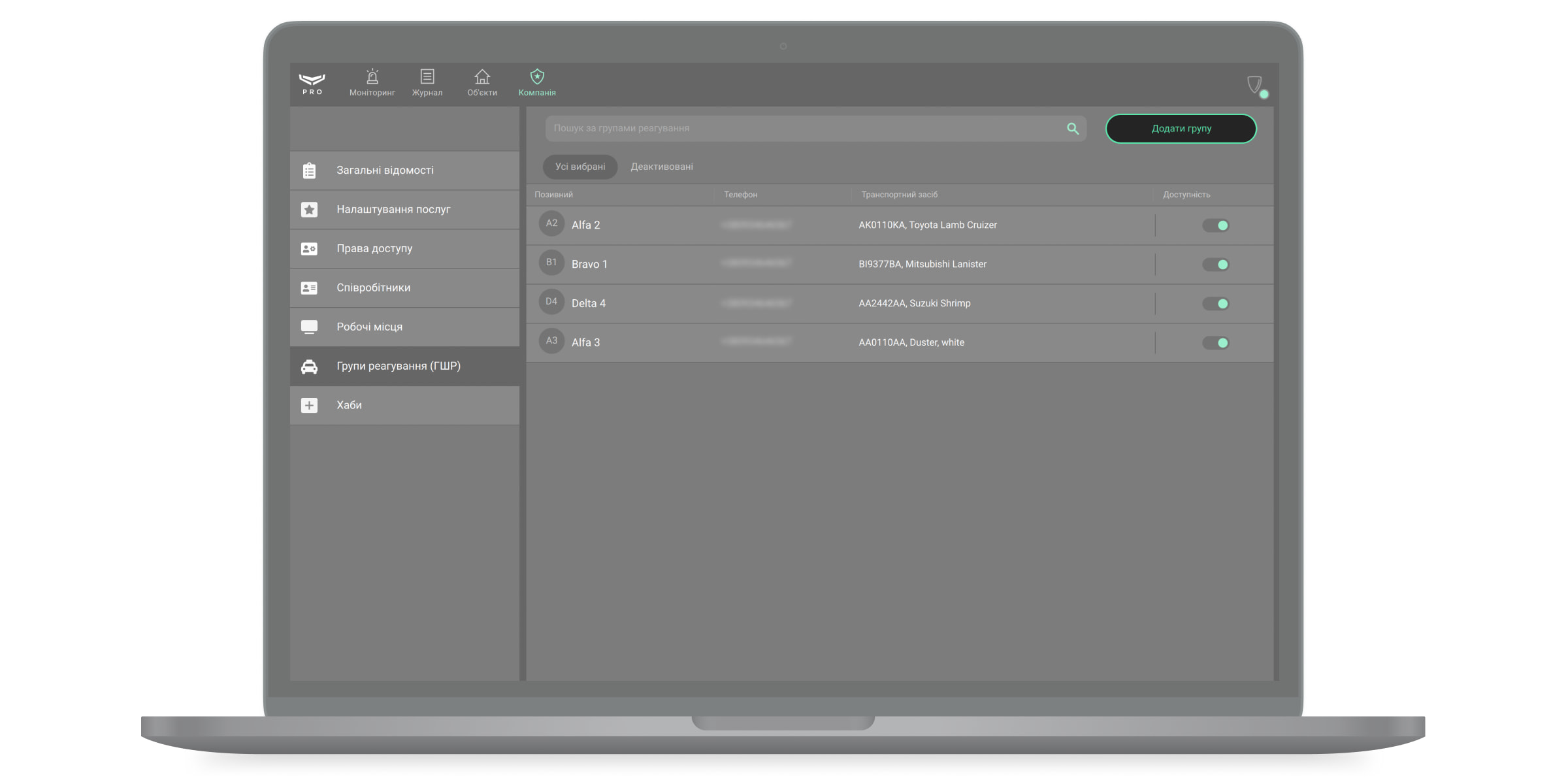
Як керувати групами реагування у меню ГШР
Щоб додати нову групу швидкого реагування, у меню ГШР клацніть кнопку Додати групу.
Відкриється вікно з формою для заповнення даних групи. Ця інформація зображуватиметься у модулі Моніторинг під час обробки тривоги, а також у модулі Об’єкти, коли ГШР закріплюється за об’єктом. Для однієї групи можна додати 2 номери телефону. Обов’язкові для заповнення поля позначені зірочкою.
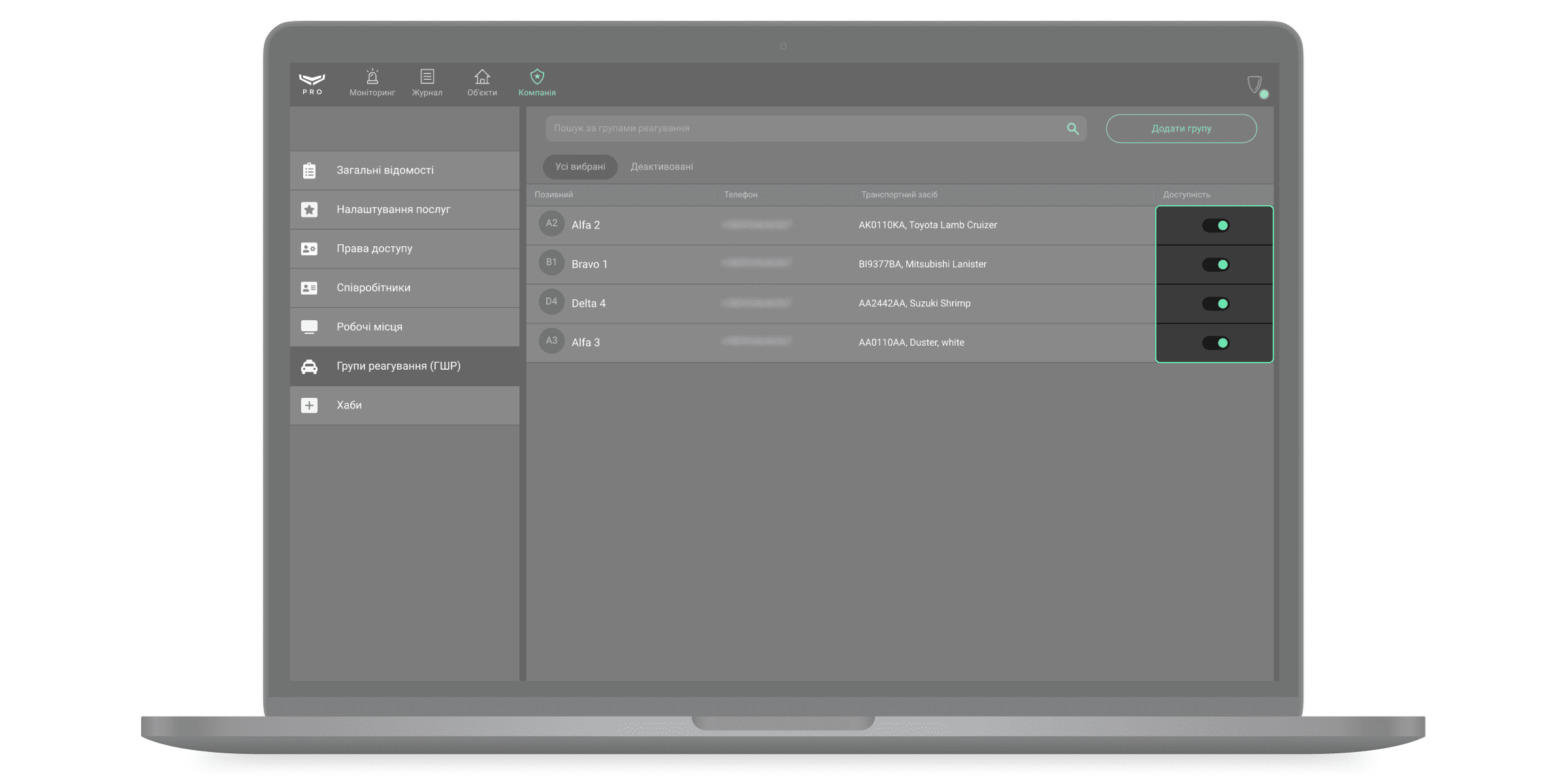
Відключити ГШР можна тимчасово, не видаляючи її з системи. Для цього у рядку з потрібною групою клацніть на перемикач. Ліве положення — екіпаж неактивний, праве — активний.
Для кожного обʼєкта можна налаштувати коди для ГШР, які активуються лише після тривоги та дійсні обмежений час. За допомогою цього коду екіпаж ГШР може змінити режим охорони з будь-якої клавіатури Ajax на обʼєкті.
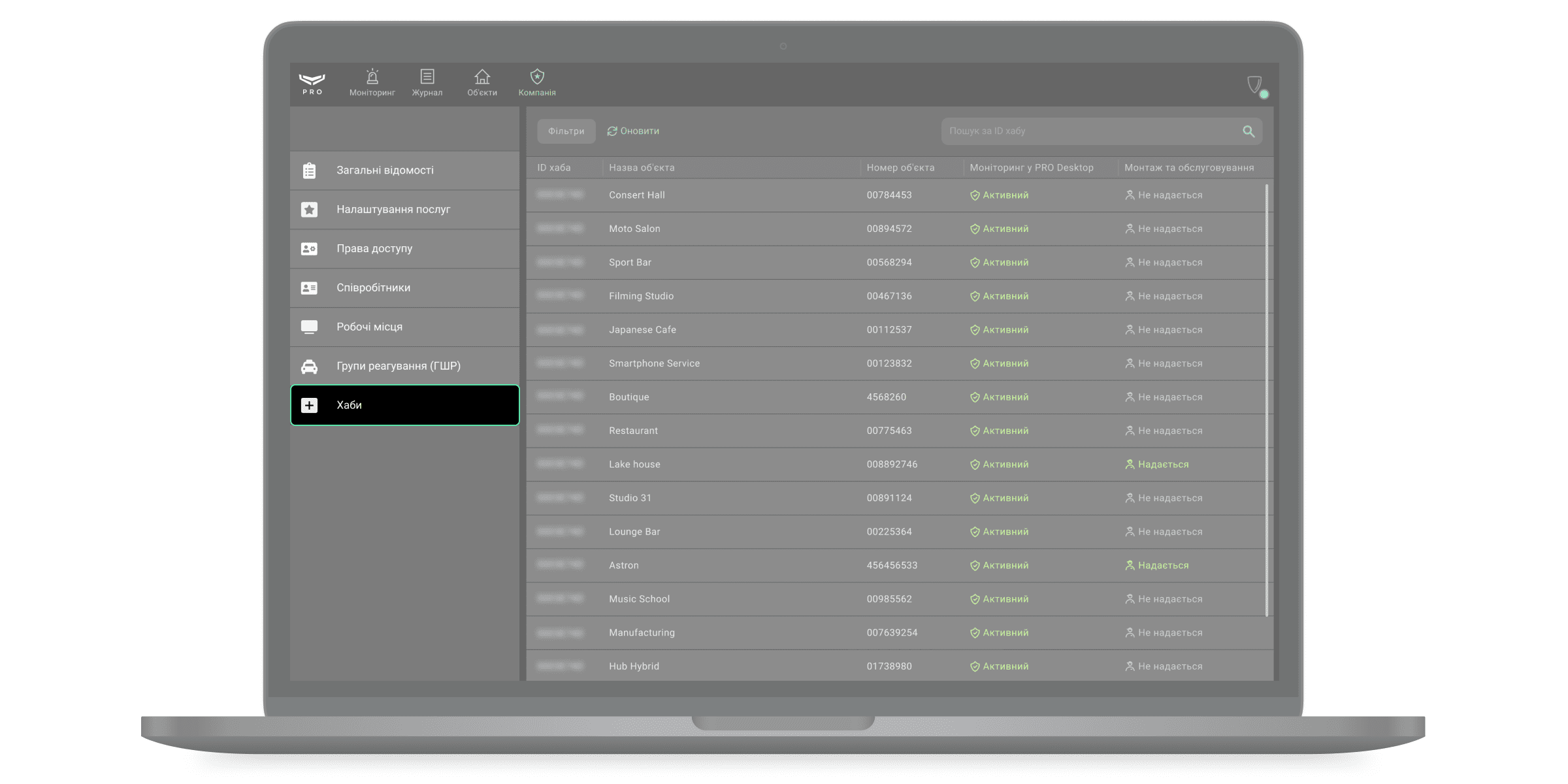
Хаби
Меню Хаби призначене для адміністрування хабів, прив’язаних до компанії. Тут можна приймати запити на моніторинг/зняття з моніторингу, додавання/видалення об’єктів, а також перенесення об’єктів з Ajax Translator до Ajax PRO Desktop (якщо обліковий запис Ajax Translator прив’язаний до акаунта компанії). У меню зображується список хабів, у якому зазначено ідентифікатор хаба, статуси об’єкта, номер і назву об’єкта у Ajax PRO Desktop.
Статус хаба також зображується у цьому вікні. Моніторинг у PRO Desktop відповідає за послуги моніторингу, а Монтаж та обслуговування – за послуги з монтажу та налаштування систем Ajax.
| Моніторинг у PRO Desktop | Значення |
| Активний | Об’єкт підключено до моніторингу. |
| Очікує видалення | Об’єкт знятий з моніторингу та знаходиться у вкладці Знято з моніторингу в модулі Об’єкти. |
| Не підключено | Запит на моніторинг не надсилався. |
| Монтаж та обслуговування | Значення |
| Надається | Запит на монтажні послуги було надіслано. |
| Не надається | Послуги з монтажу та обслуговування не надаються. Інженери монтажу та Керівники монтажу не мають доступу до налаштувань системи. |
Після вибору хаба відкривається вікно з деталями та кнопками створення/видалення об’єкта, переходу до картки об’єкта, а також видалення хаба з облікового запису компанії. Видалення з облікового запису означає, що об’єкт буде видалений як у Ajax PRO Desktop, так і в Ajax Translator (якщо обліковий запис Ajax Translator прив’язаний до акаунта в Ajax PRO Desktop).
Шаблони налаштувань
Система Ajax дає змогу PRO створити шаблони, щоб швидко застосувати кілька налаштувань одночасно. З версією прошивки Ajax PRO Desktop 4.17 та вище можна створити шаблон налаштувань телефонії. Це дає змогу налаштувати хаб Ajax, щоб під’єднати його до пульта централізованого спостереження (ПЦС) за протоколом SIP.
PRO може створити не більше 5 шаблонів.
Застосувати шаблон налаштувань може PRO в налаштуваннях хаба.
Система єдиного входу (SSO)
Меню Система єдиного входу (SSO) дає змогу налаштовувати доступ співробітників до PRO-застосунків Ajax за допомогою постачальників ідентифікації (англ. identity provider, IdP), щоб співробітники могли пройти автентифікацію через IdP, використовуючи корпоративні облікові дані. Налаштування SSO доступні в застосунку Ajax PRO Desktop версії 5.30 або новішої. Тільки власник компанії має право налаштовувати SSO.
SSO використовує протокол SAML (Security Assertion Markup Language) для автентифікації в PRO-застосунках Ajax. Крім того, використання сертифікатів безпеки є обовʼязковим для SSO в PRO-застосунках Ajax.
Кнопка Єдиний вхід (SSO) завжди доступна на початковій сторінці, незалежно від того, чи налаштовано SSO для компанії.
Об’єкти
Ролі співробітників з доступом до модуля: Інженер ПЦС, Керівник ПЦС, Керівник операторів, Оператор, Інженер монтажу, Керівник монтажу.
Модуль Об’єкти призначений для адміністрування об’єктів у Ajax PRO Desktop. Щоб перейти до модуля — виберіть Об’єкти у списку модулів у лівому верхньому куті екрана.
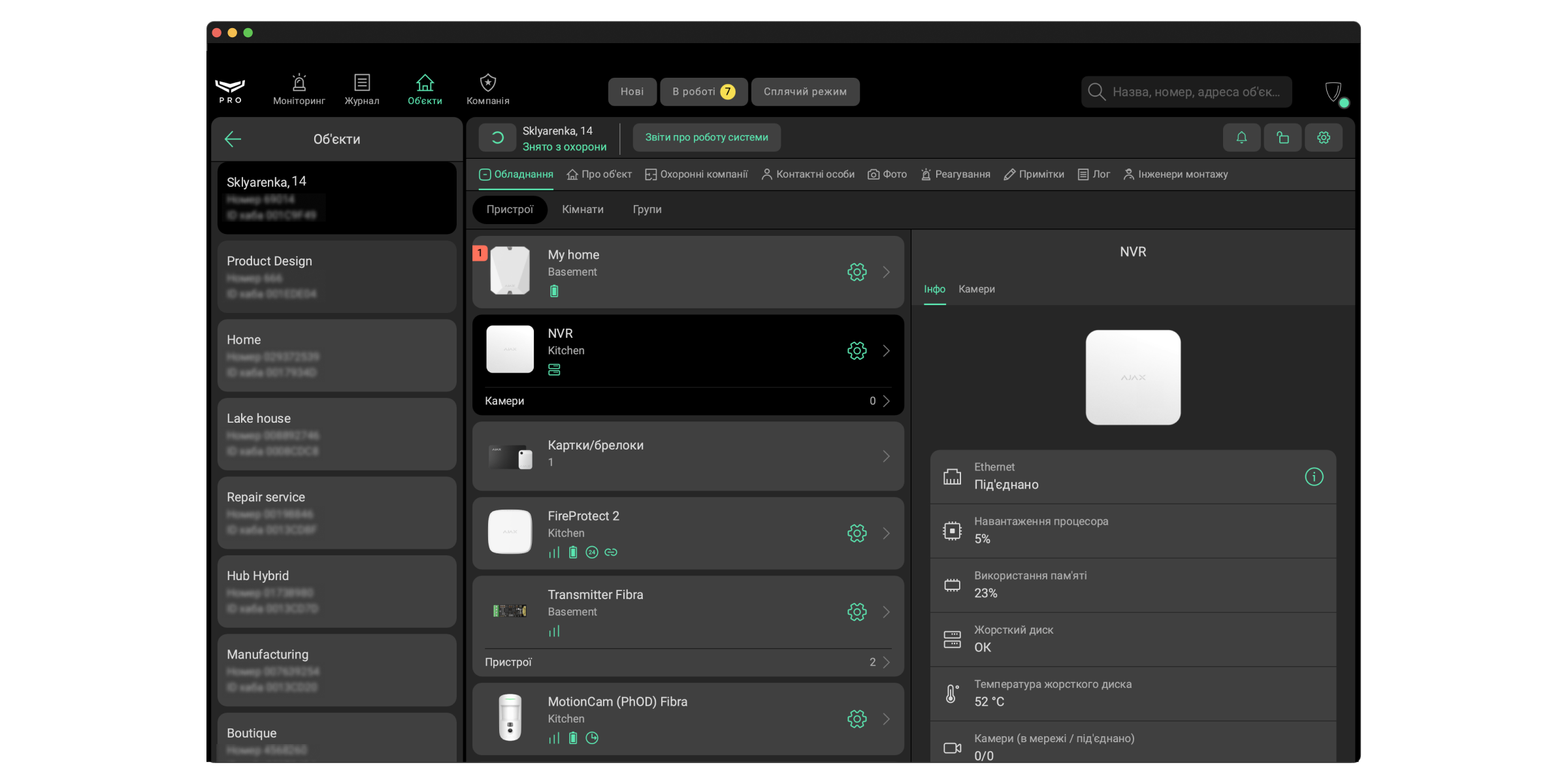
Об’єкт у Ajax PRO Desktop — це простір. Усі під’єднані до простору пристрої автоматично прив’язуються до об’єкта й зображуються у вкладці Обладнання.
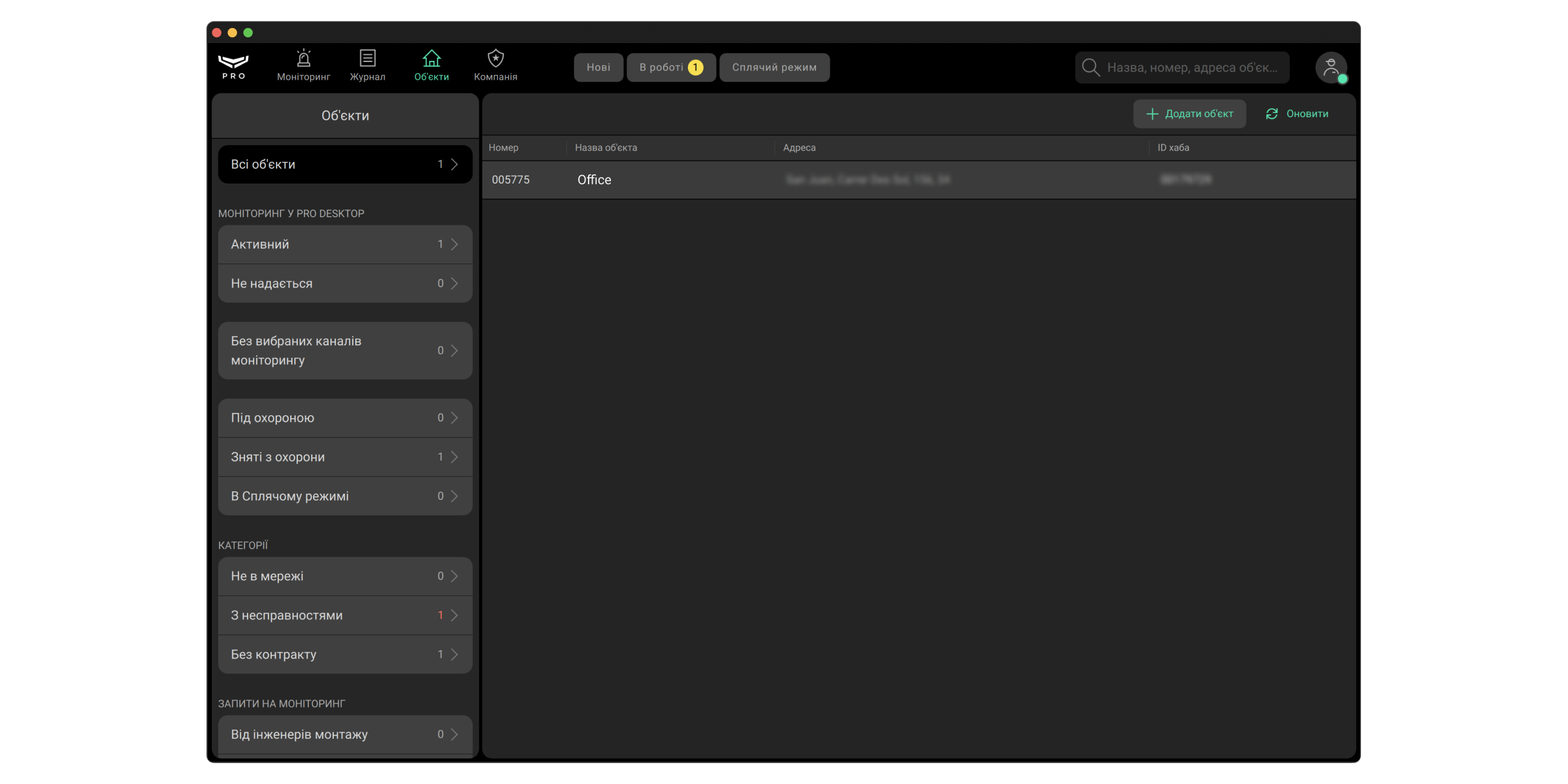
Екран модуля складається з двох частин: списку об’єктів та меню сортування. У списку об’єктів зазначено їхні номери у Ajax PRO Desktop, назви, адреси, а також ідентифікатори хабів (ID).
В меню сортування об’єктів доступні такі вкладки:
- Моніторинг через Ajax Cloud:
- <Імʼя приймача> — перелік обʼєктів, що перебувають на моніторингу <Імʼя приймача>.
- Не підключено — перелік обʼєктів, що не перебувають на моніторингу приймачів.
- Моніторинг у Ajax PRO Desktop:
- Активний — усі об’єкти Ajax PRO Desktop, крім видалених об’єктів у вкладці Знято з моніторингу.
- Не надається — перелік обʼєктів, що не перебувають на моніторингу в Ajax PRO Desktop.
- Без вибраних каналів моніторингу — перелік обʼєктів, які не перебувають на моніторингу ні через Ajax Cloud, ні в Ajax PRO Desktop.
- Під охороною — об’єкти, чиї системи безпеки зараз у режимі охорони.
- Зняті з-під охорони — об’єкти, режим охорони яких зараз не активний.
- В Сплячому режимі — об’єкти, чиї сповіщення про тривоги ігноруються.
- Не в мережі — об’єкти, де з’єднання з хабом відсутнє.
- З несправностями — об’єкти, де система безпеки повідомляє про несправність: розряджену батарею датчика, невдалі спроби встановити об’єкт під охорону тощо.
- Без договору — об’єкти, у яких не заповнено інформацію про договір з компанією. Інформацію про договір можна додати в будь-який момент.
- З встановленням та обслуговуванням — об’єкти, що знаходяться на обслуговуванні Інженерів монтажу та Керівників монтажу.
- Запити на моніторинг (від інженерів монтажу) — об’єкти, від яких було надіслано запит на підключення до ПЦС через PRO-застосунки Ajax.
- Запити на моніторинг (від користувачів) — об’єкти, від яких було надіслано запит на підключення до ПЦС через застосунок Ajax для кінцевих користувачів Ajax Security System.
- Запити на зняття з моніторингу — перелік об’єктів, від яких було надіслано запит на відключення від ПЦС через будь-який застосунок Ajax.
Скасувати запит на зняття з моніторингу може лише користувач із правами адміністратора або PRO-акаунт із правами на налаштування системи. Зробити це можна в будь-якому застосунку Ajax: вкладка Керування → Налаштування
простору → Охоронні компанії.
- Знято з моніторингу — видалені об’єкти. Об’єкти автоматично видаляються через 7 днів.
У модулі Об’єкти також доступні такі кнопки:
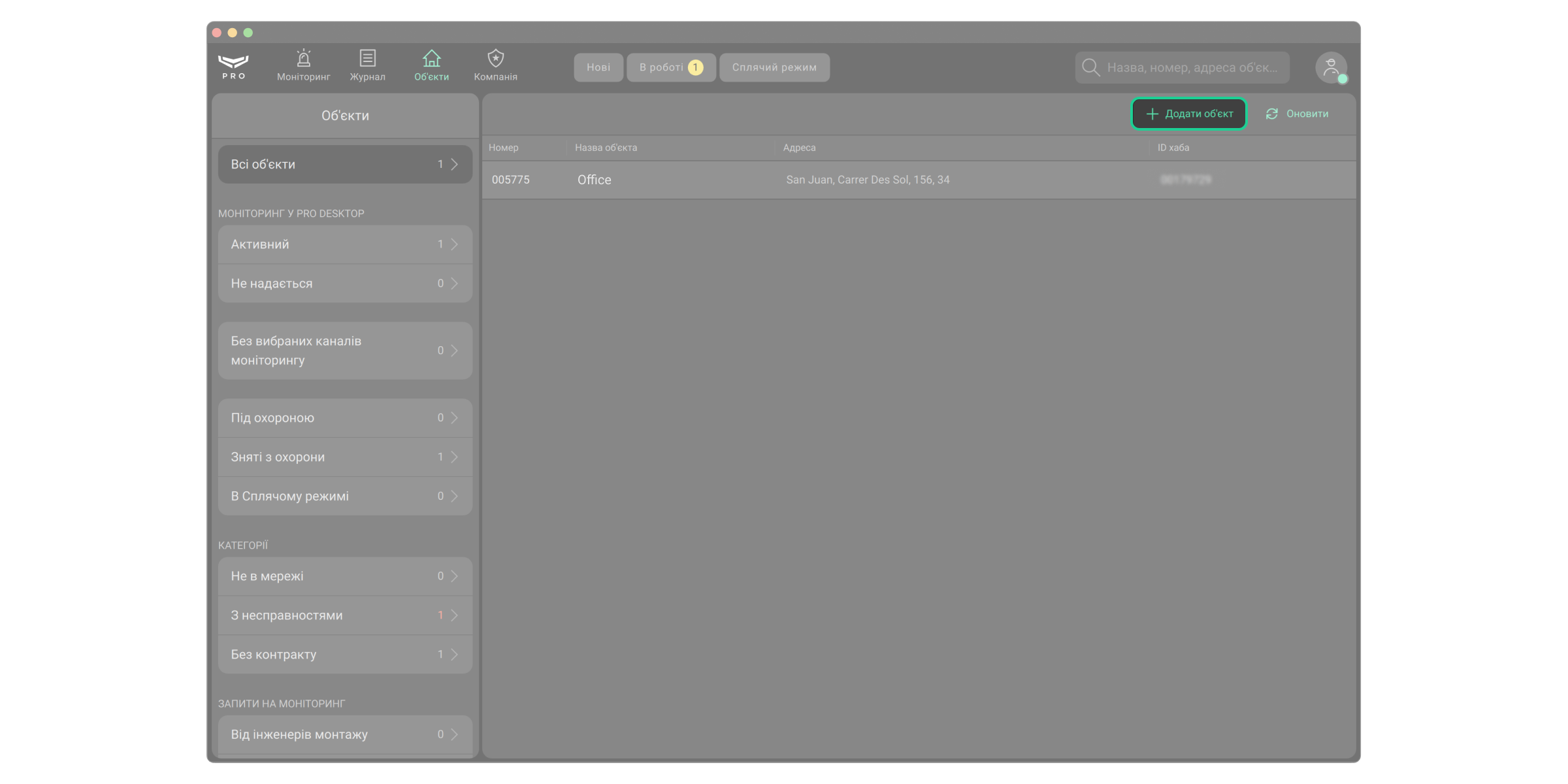
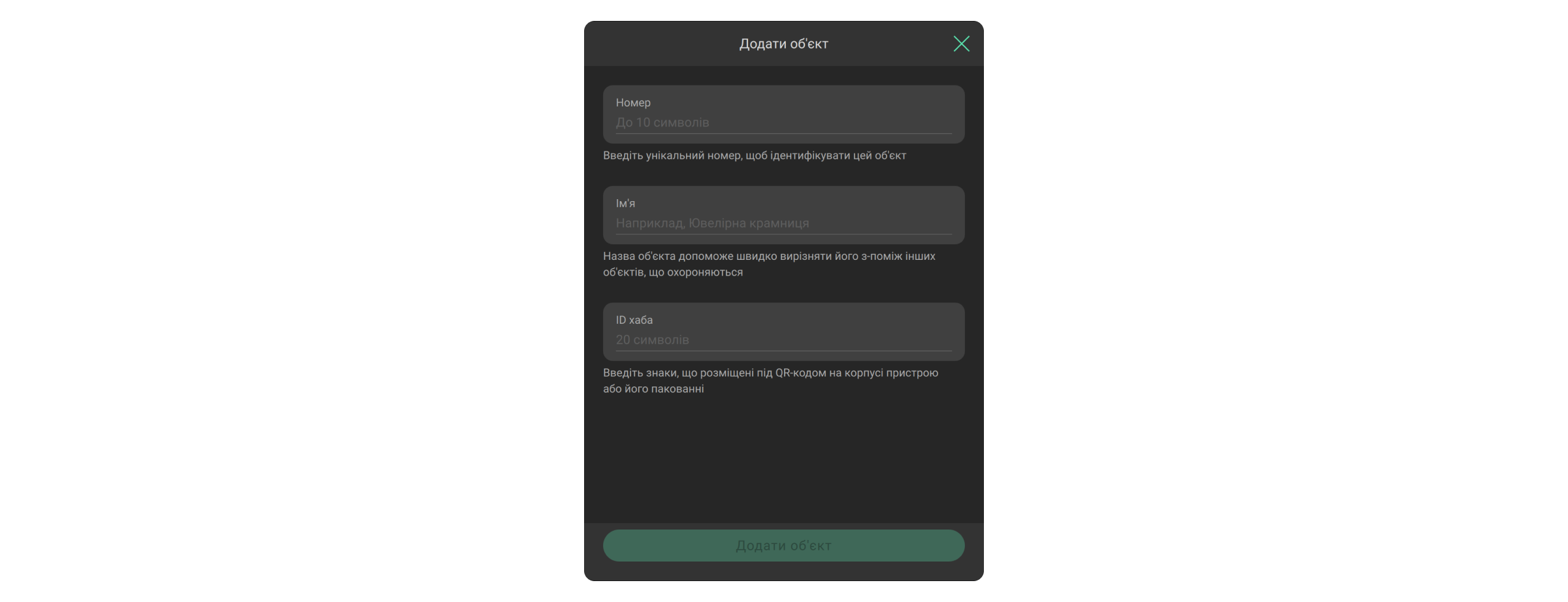
- Додати об’єкт — дає змогу прив’язати об’єкт до компанії за QR-кодом (ідентифікатором) хаба або створити пустий об’єкт.
Спосіб додавання об’єкта за ідентифікатором хаба залежить від ролі співробітника та типу компанії: моніторингова, монтажна чи охоронна (монтаж і моніторинг). Створити пустий обʼєкт може лише співробітник монтажної чи охоронної компанії в ролі Інженер монтажу або Керівник монтажу.
- Звіт про роботу системи — відкриває меню звітів про роботу системи.
- Оновити — оновлює список прив’язаних до компанії хабів.
Додавання об’єкта
Додати новий об’єкт у Ajax PRO Desktop можна декількома способами:
- Використати ідентифікатор хаба (його QR-код).
- Створити пустий обʼєкт і додати до нього пристрої, які можуть працювати без хаба.
- Надіслати запитом через застосунок Ajax.
- Перевести об’єкт із Ajax Translator у Ajax PRO Desktop.
Після підключення хаба вкажіть усю потрібну інформацію в картці об’єкта. Це спростить навігацію та пошук об’єктів у застосунках Ajax.
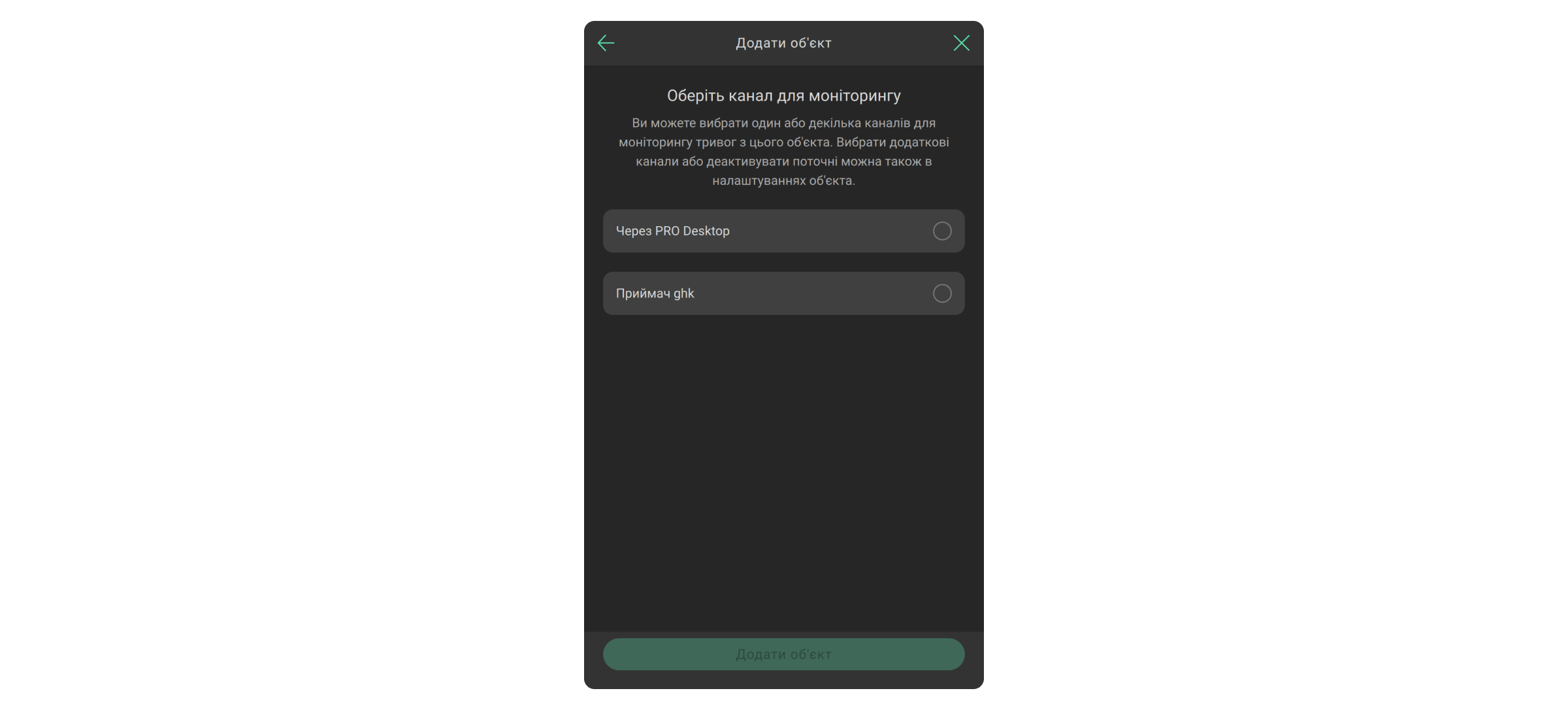
Співробітники компаній, які використовують моніторинг через Ajax Cloud, можуть обрати один або декілька каналів для моніторингу, коли додають обʼєкт за ідентифікатором або за запитом у застосунку. Це стало доступним із версією прошивки Ajax PRO Desktop 4.0 або вище.
Додавання за ідентифікатором
Після додавання об’єкта для нього буде створено картку з усією інформацією, необхідною для обробки тривог: адреса, контакти, схеми приміщень, проїзду, а також відповідальні особи, коментарі тощо. Додати обʼєкт можна лише з облікового запису компанії, а не з персонального Ajax PRO-акаунта. Після додавання обʼєкта в компанії буде постійний доступ до його налаштувань.
Додати об’єкт за ідентифікатором (QR-кодом) можна в разі дотримання умов:
- Хаб онлайн.
- У просторі немає адміністраторів або PRO.
- Хаб не додано до облікового запису монтажної компанії, і він не привʼязаний до іншої моніторингової компанії.
Для додавання обʼєкта за ідентифікатором хаба співробітник компанії має бути в ролі:
- Інженер ПЦС або Керівник ПЦС — для моніторингових та охоронних компаній.
- Інженер монтажу або Керівник монтажу — для монтажних та охоронних компаній.
Щоб додати обʼєкт, у Ajax PRO Desktop:
- Відкрийте модуль Об’єкти.
- Натисніть кнопку Додати об’єкт.
- Вкажіть номер і назву об’єкта, а також 20-значний ідентифікатор хаба (розміщений під QR-кодом на хабі або пакованні, формат xxxxxxxxxxxxxxxxxxxx).
Параметри Номер та ID хаба не обовʼязкові для заповнення Інженером монтажу або Керівником монтажу охоронної чи монтажної компанії. Водночас вони обовʼязкові для заповнення Інженером ПЦС або Керівником ПЦС моніторингової компанії.
- Клацніть Додати об’єкт.
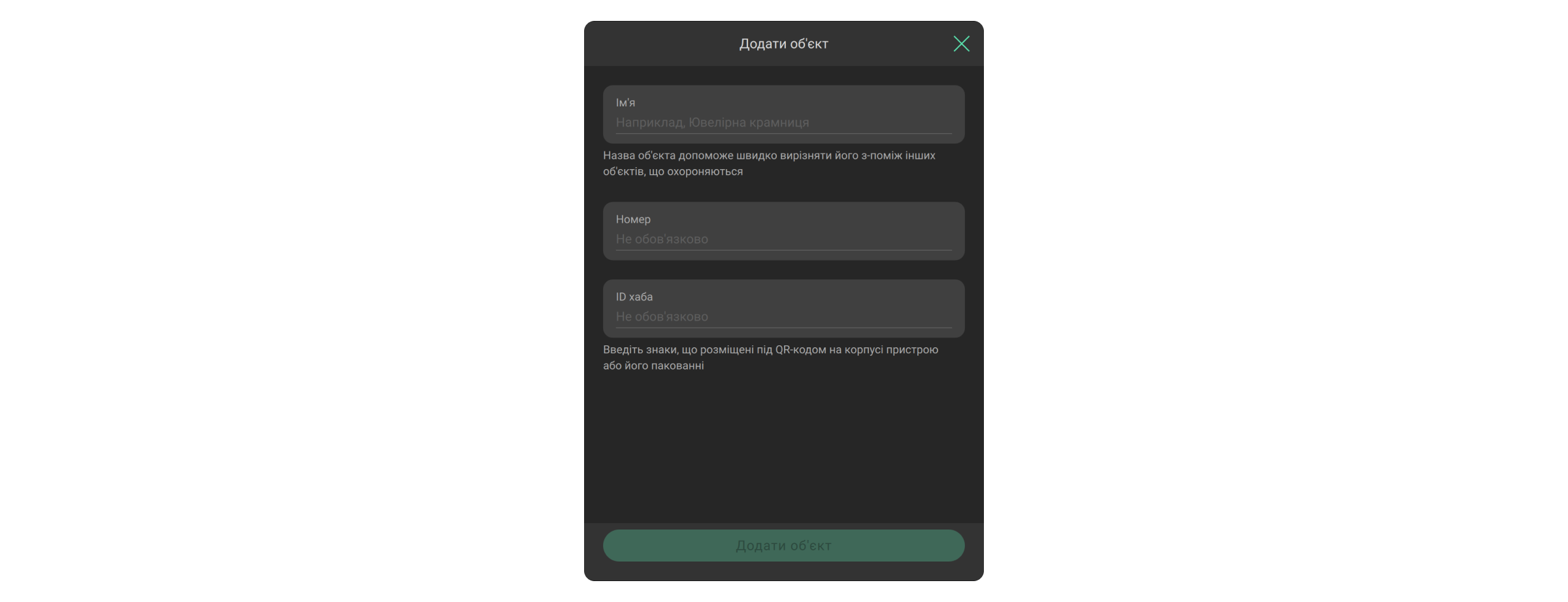
Створення пустого обʼєкта
Створювати пустий обʼєкт може лише Інженер монтажу чи Керівник монтажу сервісної або монтажної компанії.
Щоб створити пустий обʼєкт у Ajax PRO Desktop:
- Відкрийте модуль Обʼєкти.
- Клацніть кнопку Додати обʼєкт.
- Вкажіть назву обʼєкта.
- Клацніть кнопку Додати обʼєкт.
Додавання об’єкта за запитом у застосунку
Запит на додавання надсилається через застосунок Ajax адміністратором простору або PRO-акаунтом з доступом до налаштувань об’єкта. Список запитів на моніторинг та зняття з моніторингу зображується у відповідних вкладках модуля Об’єкти, а також у меню Хаби модуля Компанія.
Спосіб додавання залежить від типу послуг, що надаються:
- Для доступу до моніторингу тривог — кінцевому користувачу або PRO з доступом до налаштувань системи необхідно надсилати запит на моніторинг.
- Для доступу до монтажу та обслуговування — співробітнику компанії необхідно надсилати запит на доступ до налаштувань системи.
- Для доступу обох типів — необхідно надсилати обидва запити.
Щоб надіслати запит на моніторинг тривог, у застосунку Ajax:
- Виберіть простір, якщо у вас їх кілька або ви використовуєте PRO-застосунок Ajax.
- Перейдіть до вкладки Керування та відкрийте налаштування простору.
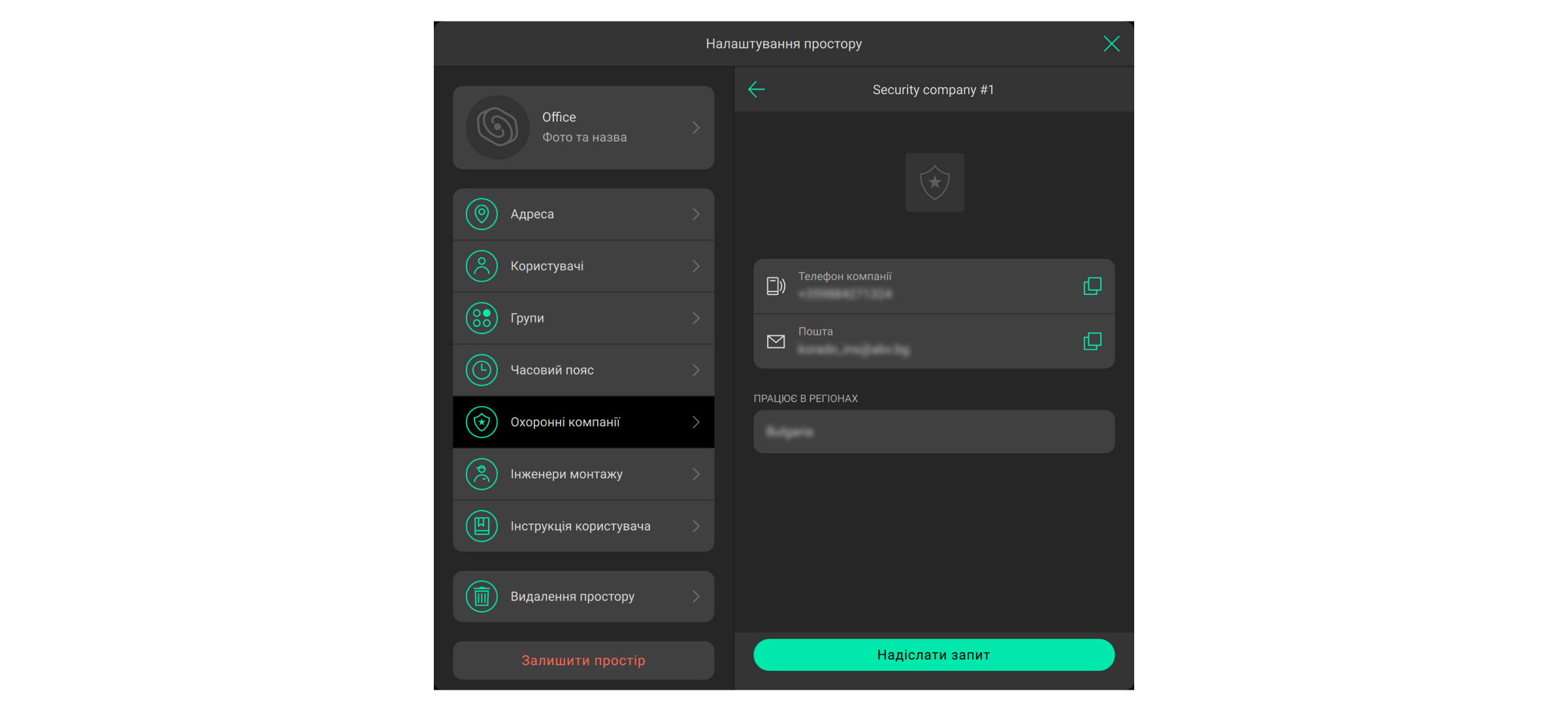
- Відкрийте меню Охоронні компанії.
- Виберіть компанію та клацніть Надіслати запит.
Запит на моніторинг також можна надіслати, якщо відома email-адреса компанії. Для цього натисніть на іконку конверта в меню Охоронні компанії, вкажіть email-адресу компанії, натисніть Продовжити. У списку виберіть компанію та підтвердіть надсилання запиту.
Щоб прийняти запит на моніторинг, у Ajax PRO Desktop:
- У модулі Об’єкти перейдіть до меню Запити на моніторинг (від користувачів) та/або Запити на моніторинг (від інженерів монтажу).
- Виберіть простір.
- Клацніть Прийняти запит. Для простору автоматично буде створена картка об’єкта для заповнення інформації.
- Введіть номер, назву об’єкта та натисніть Зберегти. У Ajax PRO Desktop з’явиться новий об’єкт.
Щоб надіслати запит на доступ до монтажу та обслуговування, у застосунку Ajax:
- Виберіть простір, якщо у вас їх кілька або ви використовуєте PRO-застосунок Ajax.
- Перейдіть до вкладки Керування та відкрийте налаштування простору.
- Відкрийте меню Інженери монтажу.
- Клацніть кнопку Додати.
- Введіть email-адресу компанії, яка вказана в меню Загальні відомості.
- Виберіть компанію та підтвердіть надсилання запиту.
Приймати запит на послуги монтажної компанії у Ajax PRO Desktop не потрібно. Після додавання компанія має 8 годин на зміну налаштувань простору, додавання пристроїв та запрошення користувачів. Коли час доступу сплине, компанія більше не може вносити зміни до налаштувань об’єкта.
У разі необхідності Інженер монтажу або Керівник монтажу може надіслати запит на тимчасовий або постійний доступ, який має підтвердити адміністратор простору або PRO-акаунт з правами на налаштування системи.
PRO-акаунт отримує постійні права на налаштування системи, якщо у просторі немає жодного адміністратора.
Перенесення об’єктів із Ajax Translator
Щоб перенести об’єкти з Ajax Translator, зверніться до служби технічної підтримки Ajax.
Налаштування об’єкта
Налаштовувати об’єкт може Інженер монтажу або Керівник монтажу, за допомогою застосунків для смартфонів та ПК. Обидва застосунки надають однакові можливості для Інженерів монтажу.
За початкових налаштувань Керівник монтажу має ті самі права на налаштування, що надані його компанії. Інженер монтажу не має доступу до налаштувань простору (якщо доступ до всіх об’єктів вимкнено), поки йому не надасть це право Керівник монтажу. Після отримання доступу Інженери монтажу можуть розпочинати налаштування об’єкта.
Надати доступ інженеру монтажу можна двома способами:
| Перший спосіб | Другий спосіб |
|
|
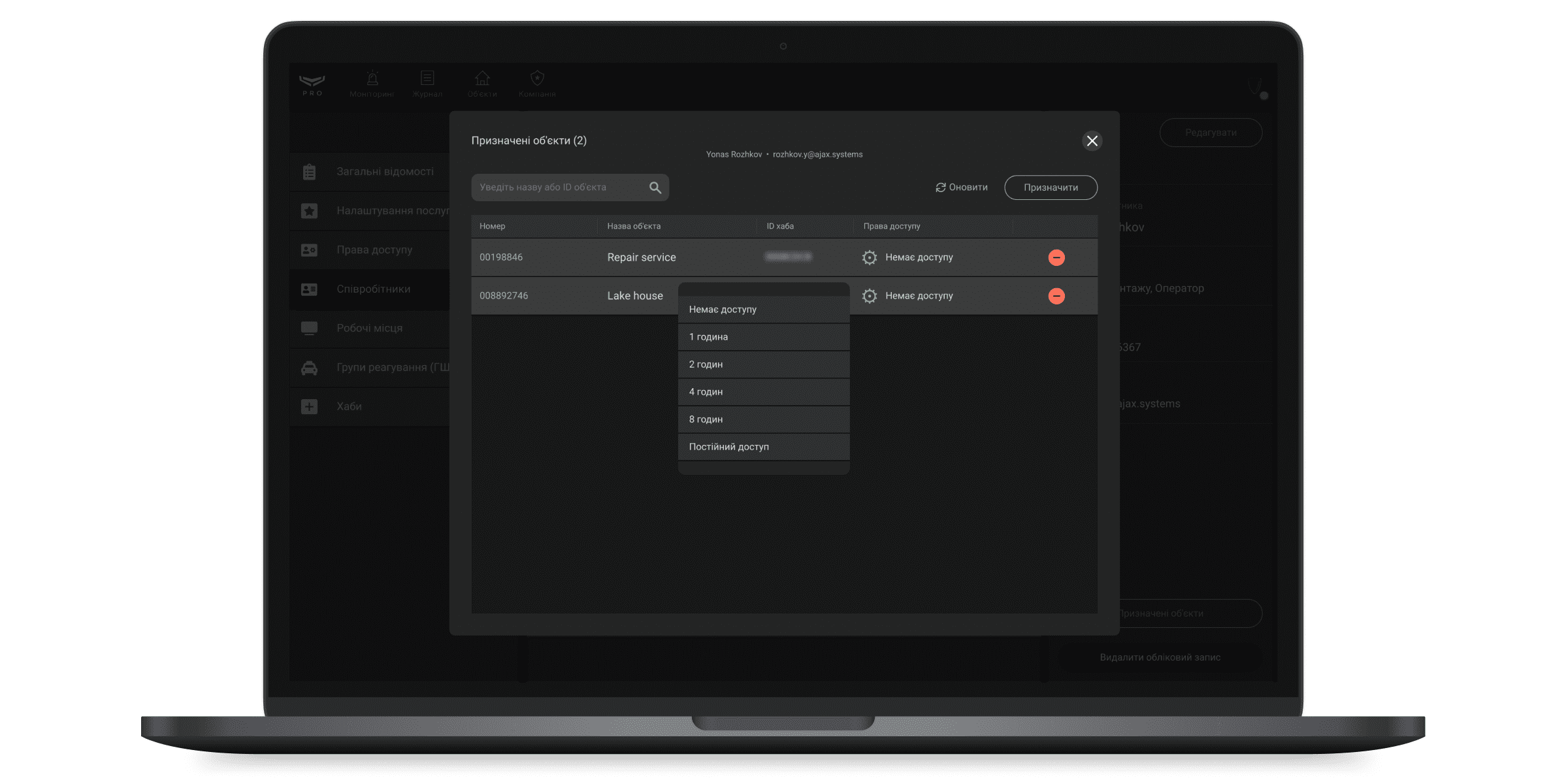
Пролонгація доступу до налаштувань простору
У зазначеному на скріншоті полі зображується час, протягом якого Інженеру монтажу надано доступ до налаштувань системи. Клікніть на поле, щоб надіслати запит на постійний або тимчасовий доступ (1, 2, 4 або 8 годин).
Якщо часу на налаштування недостатньо, Інженер монтажу може надіслати запит, щоб отримати більше часу доступу до налаштувань. Такий запит отримають усі Керівники монтажу цієї компанії або адміністратори простору.
Якщо у компанії достатньо прав, будь-який Керівник монтажу може надати це право Інженеру монтажу. Підтвердити такий запит можна лише в застосунку Ajax PRO Desktop.
Якщо прав недостатньо — наприклад, компанія має права на налаштування протягом 4 годин, а Інженеру монтажу потрібно 8 годин — Керівник монтажу може надіслати запит на права доступу адміністратору. Після підтвердження доступ буде надано компанії та відповідному Інженеру монтажу.
Система дає змогу Керівнику монтажу автоматично підтверджувати запити інженерів до налаштувань обʼєкта або до пристроїв відеоспостереження. Щоб увімкнути автоматичне підтвердження:
- Перейдіть у модуль Компанія.
- Відкрийте меню Налаштування послуг.
- Увімкніть опцію Автоматичний розгляд запитів на доступ до системи керівником монтажу.
Якщо компанія не матиме достатньо часу доступу, запит інженера буде автоматично перенаправлено адміністратору простору.
Налаштування прав компанії
Адміністратор простору або PRO-акаунт з правами на налаштування системи може призначити права доступу компанії. Ці налаштування поширюються на всіх співробітників компанії. Щоб призначити права доступу компанії, у застосунку Ajax:
- Виберіть об’єкт, якщо у вас їх кілька або ви використовуєте PRO-застосунок Ajax.
- Перейдіть у Налаштування
простору.
- Відкрийте меню Інженери монтажу.
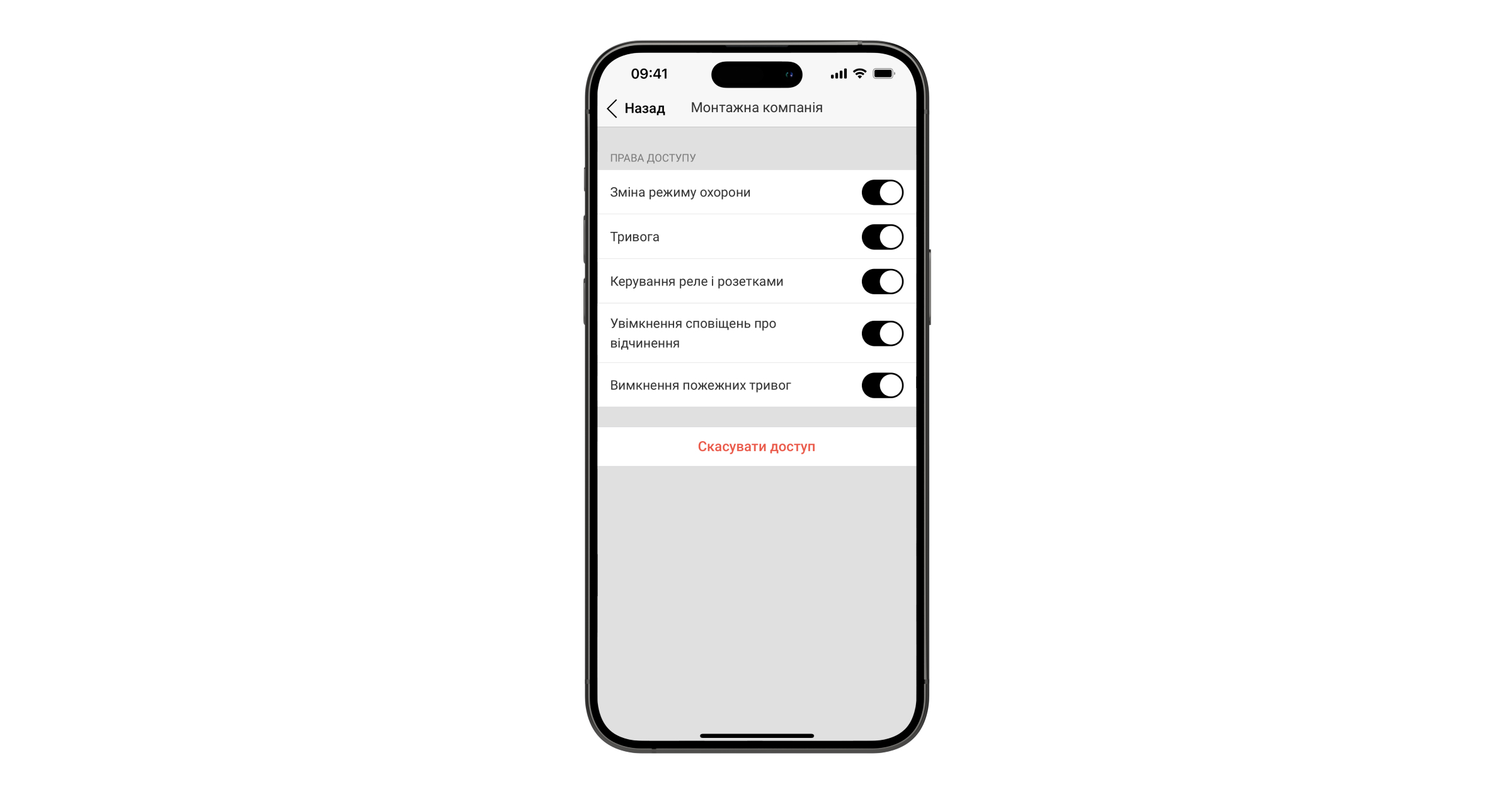
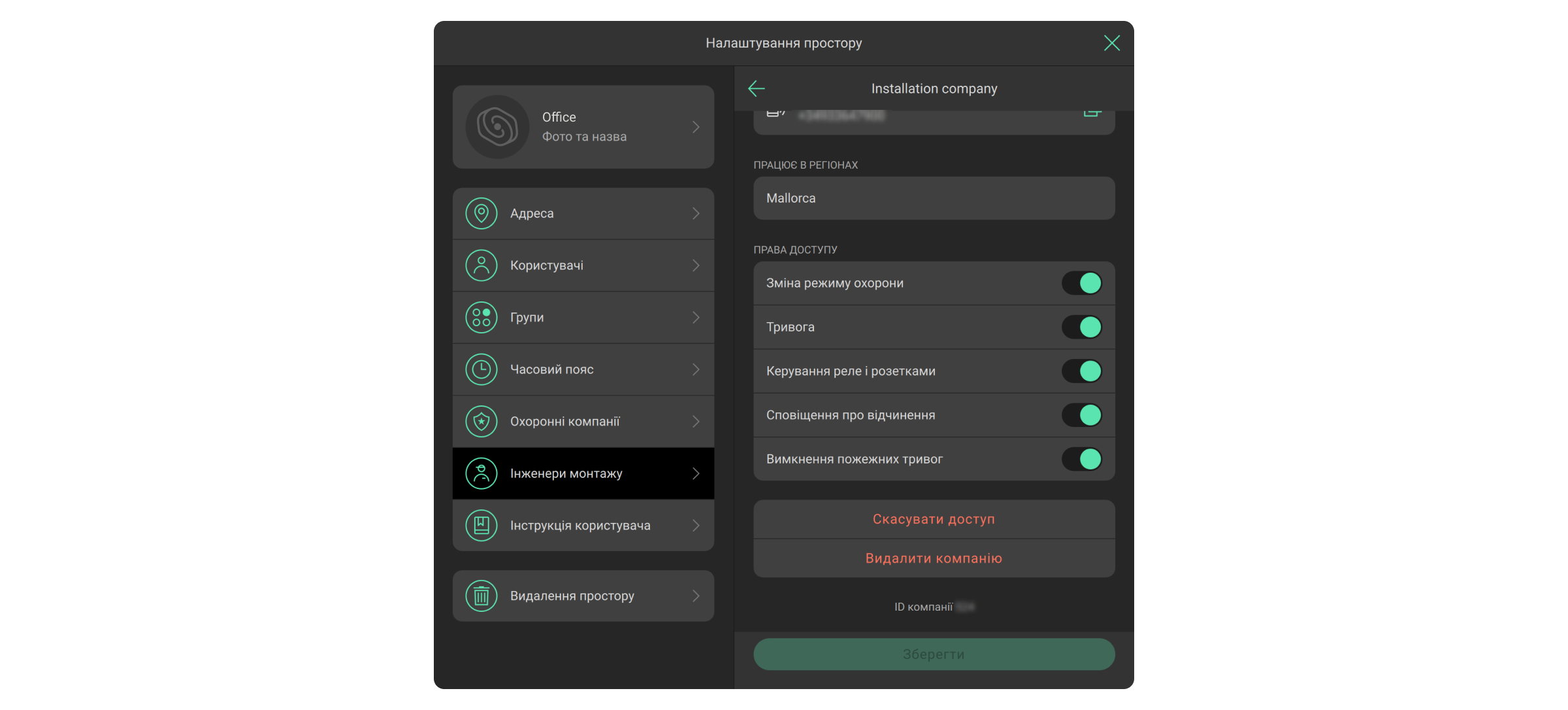
- Виберіть компанію. Перейдіть у її налаштування. Вони дають змогу надати або скасувати право на:
- Зміну режиму охорони.
- Активацію тривожної кнопки в застосунках Ajax.
- Керування реле та розумними розетками.
- Увімкнення сповіщень про відчинення.
- Вимкнення пожежних тривог.
Перелік доступних налаштувань прав доступу компанії залежить від пристроїв, доданих у простір.
Адміністратор простору або PRO-акаунт з правами на налаштування системи також може видалити компанію з простору або скасувати їй доступ.
Картка об’єкта
Дані про об’єкт можна доповнювати та редагувати. Дані розділені на вкладки:
- Обладнання — перелік пристроїв, віртуальних кімнат і охоронних груп об’єкта. Виберіть пристрій, щоб відкрити екран станів, де вказано заряд батареї, стан з’єднання, стан тампера та інші дані про роботу.
- Охоронні компанії — назва, телефон і статус охоронних компаній.
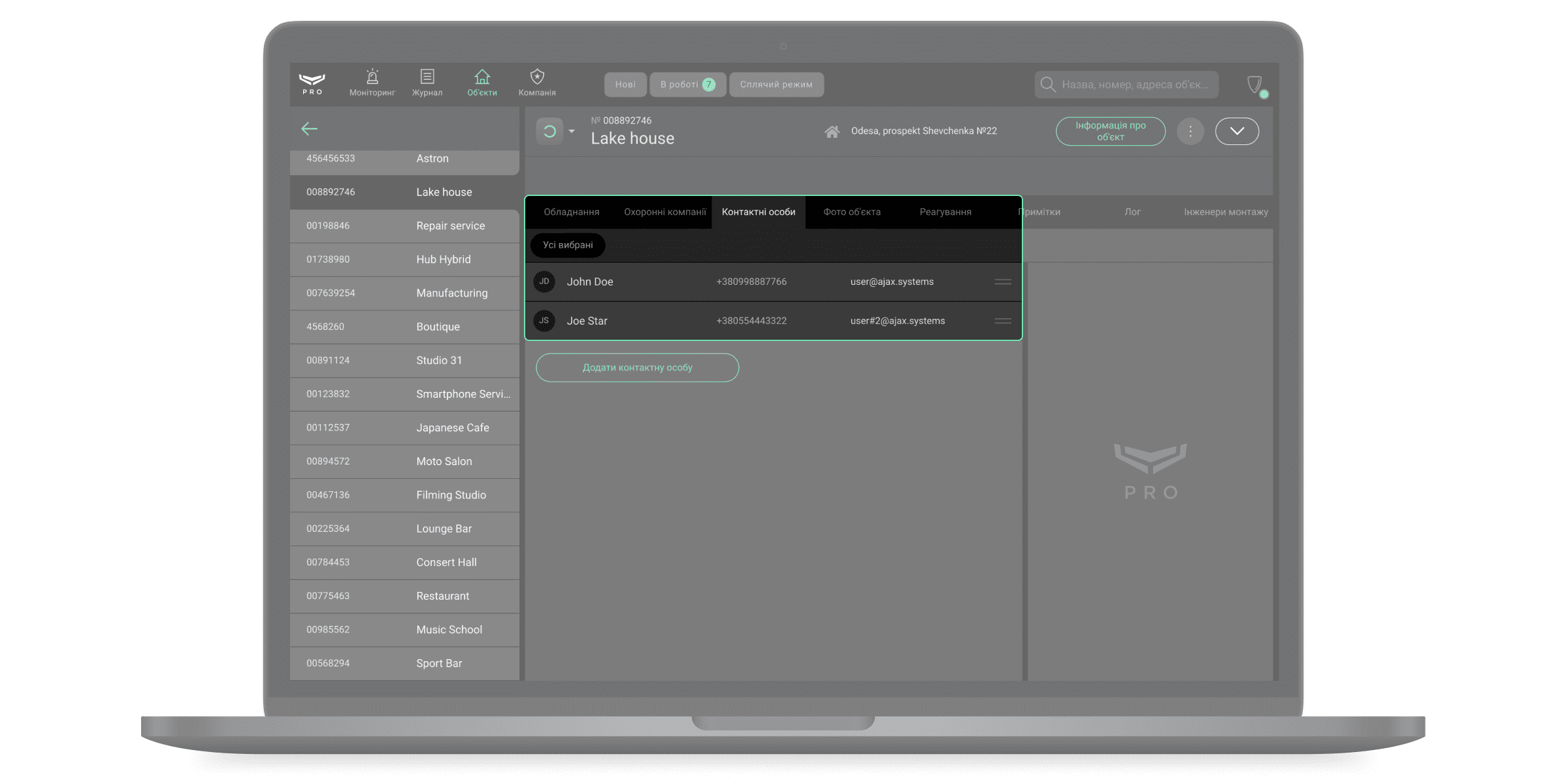
- Контактні особи — імена та телефони людей, з якими оператор може зв’язатися у разі тривоги на об’єкті.
- Фото об’єкта — фото об’єкта, мапа підступів до об’єкта, плани приміщень об’єкта та мапи проїзду до об’єкта.
- Реагування — інформація про закріплені за об’єктом основні та резервні ГШР. Щоб керувати групами в цьому меню, потрібно спочатку створити їх у модулі Компанія в меню Групи реагування (ГШР).
- Примітки — технічна інформація про об’єкт (дати та деталі монтажних робіт, підключення до пульта моніторингу, дані Інженера монтажу, закріпленого за об’єктом).
- Лог — журнал подій об’єкта.
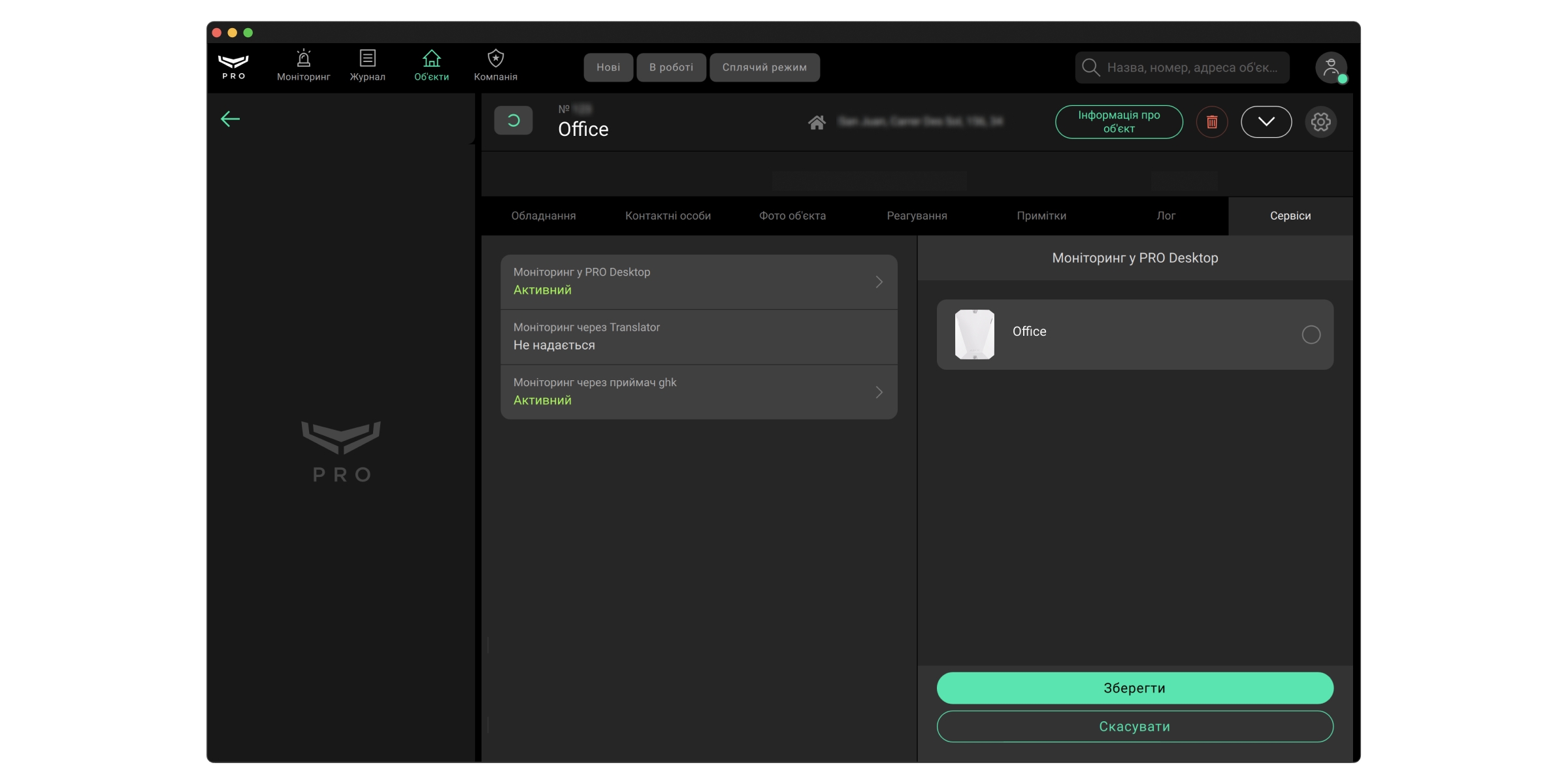
- Сервіси — інформація про моніторинг у Ajax PRO Desktop, через Ajax Cloud або Ajax Translator, монтаж та обслуговування (доступно лише для Керівника ПЦС, Інженера ПЦС, Керівника операторів та Оператора).
З версією прошивки Ajax PRO Desktop 4.0 та вище для будь-якої моніторингової компанії стала доступна активація/деактивація каналу Моніторинг у Ajax PRO Desktop. - Інженери монтажу — інформація про призначених інженерів монтажу: імʼя співробітника, електронна пошта, права доступу.
Крім часу доступу до налаштувань об’єкта, на вкладці Обладнання показано кнопку Звіти про роботу системи. Кнопка доступна лише для ролей співробітників, яким власник компанії надав таке право.
Враховуйте, що співробітники з роллю Інженер монтажу можуть створювати звіти, якщо вони мають доступ до налаштувань цього хаба.
Після натискання на кнопку можна згенерувати новий звіт або завантажити раніше створений звіт з архіву. У разі спроби створити новий звіт відкривається вкладка Звіт про роботу системи.
Відеостіна
Відеостіна призначена для одночасного перегляду відеопотоків з декількох каналів. Таким чином, PRO-користувач може відстежувати ситуацію на обʼєкті в динаміці й швидко реагувати на можливі інциденти. Відеостіна транслює відео з камер відеоспостереження як в реальному часі, так і з архіву (якщо камера або відеореєстратор Ajax має накопичувач памʼяті).
Віджет відеостіни — це спеціальний дисплей в застосунку Ajax PRO Desktop, з яким ви можете використовувати всі функції відеостіни. Щоб відкрити віджет відеостіни, виберіть вкладку Відеостіна поруч із назвою простору та увімкніть опцію Увімкнути віджет Відеостіни.
Віджет дає змогу налаштувати відеостіну, керувати камерами, переглядати відео в реальному часі, отримувати доступ до архівних відео та багато іншого.
Разом із релізом версії Ajax PRO Desktop v5.35 додано функцію відеомоніторингу кількох просторів, яка дає змогу додавати камери з різних просторів до однієї відеостіни. За допомогою цієї функції PRO-користувачі можуть створювати шаблони в розділі Відеостіна, щоб поєднати камери з будь-яких просторів, до яких вони мають доступ.
Редагування картки та видалення об’єкта
Над інформаційними вкладками об’єкта розташовані: меню керування режимами охорони, номер об’єкта, його назва та адреса, кнопки редагування й видалення, а також кнопка для перегляду контактів і деталей роботи об’єкта.
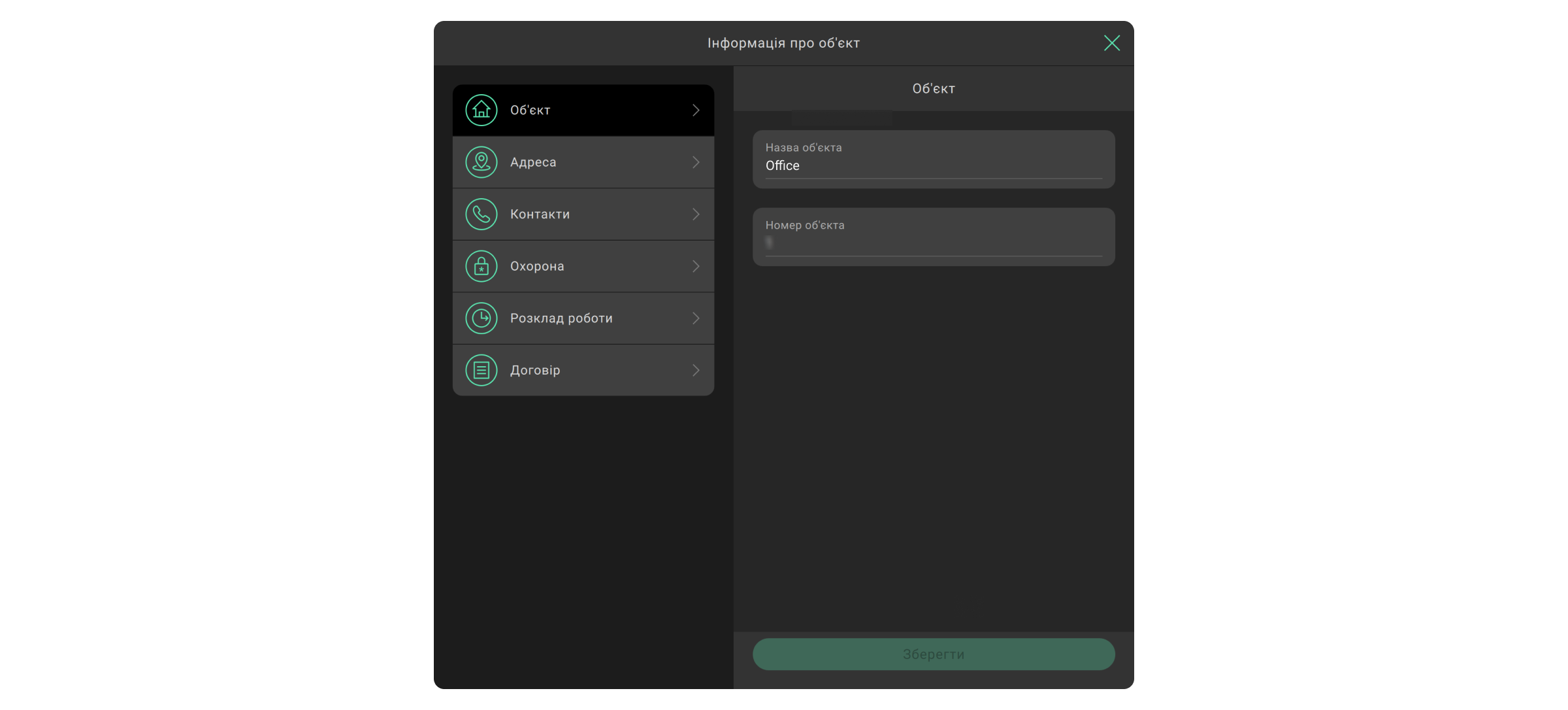
Натисніть Інформація про об’єкт, щоб змінити назву чи номер об’єкта, зазначити його місце розташування, контактні дані, кодове слово для скасування тривоги, додати розклад роботи, увімкнути тривогу в разі зняття з-під охорони у неробочий час або вказати дані договору. Ця інформація відображається в модулі Моніторинг під час обробки тривоги. Обов’язкові для заповнення поля позначені зірочкою. Після внесення або редагування даних натисніть Зберегти.
Щоб видалити об’єкт, натисніть червону іконку кошика або значок з трьома крапками, якщо компанія надає послуги моніторингу тривог і монтажу та обслуговування. Відкриється меню вибору: Припинити моніторинг або Припинити обслуговування. Припинення моніторингу та сервісного обслуговування – це різні функції. Наприклад, якщо моніторинг об’єкту активний, а сервісне обслуговування припиняється — оператори продовжать отримувати тривоги та події цієї системи, але Інженери монтажу не зможуть змінювати налаштування обладнання на об’єкті.
Після припинення моніторингу об’єкт буде переміщено до вкладки Знято з моніторингу й автоматично видалено через 7 днів. Упродовж цього часу об’єкт можна повернути до списку активних. Для цього перейдіть в меню Знято з моніторингу в модулі Об’єкти й натисніть Відновити обʼєкти. Припинити моніторинг можна тільки для тих об’єктів, які не мають відкритих інцидентів.Назва файлу має такий формат: AA_XXXXXXXX_YYYYYYY_MM
Щоб видалити об’єкти раніше ніж через 7 днів, виберіть об’єкт у меню Знято з моніторингу та натисніть червоний значок кошика. Натисніть Припинити моніторинг, щоб підтвердити.
Коли припинено сервісне обслуговування, об’єкт видаляється остаточно. Це означає, що Інженери монтажу та Керівники монтажу більше не зможуть обслуговувати цей об’єкт. Щоб відновити об’єкт, компанію потрібно заново запросити через налаштування хаба.
Простір продовжить існувати після припинення обслуговування компанією, навіть якщо вона — останній користувач простору.
Звіти про роботу системи
Звіти про роботу системи дають змогу генерувати PDF-файли, які містять інформацію про охоронні пристрої та пожежні датчики, під’єднані до хаба, та їхні стани. Звіти дозволяють регулярно стежити за станом усіх об’єктів на моніторингу.
Звіти про роботу системи можна згенерувати лише для обʼєктів із хабами.
Один звіт генерується для одного об’єкта. Мова звіту, що завантажується, відповідатиме мові, вибраній у застосунку Ajax PRO Desktop як мова для СМС-повідомлень.
Власник компанії може увімкнути або вимкнути функцію звітів про роботу системи у будь-який момент.
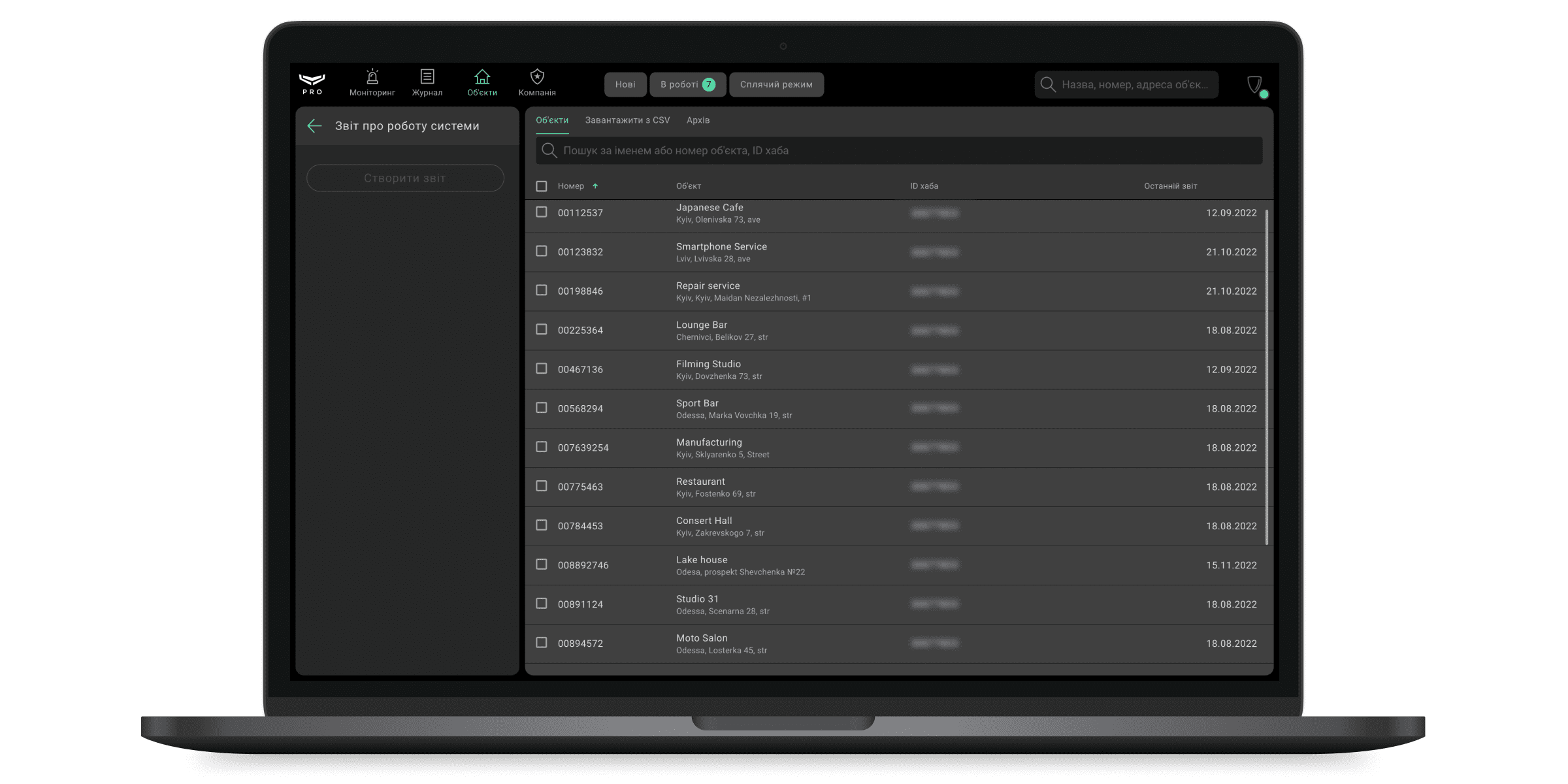
Меню звітів про роботу системи містить три вкладки:
- Об’єкти — містить список об’єктів, за якими можна згенерувати звіти про роботу системи. У цьому меню також можна генерувати ці звіти.
- Завантажити з CSV — меню завантаження списку хабів для генерації звіту про роботу системи.
- Архів — містить уже створені звіти про роботу системи.
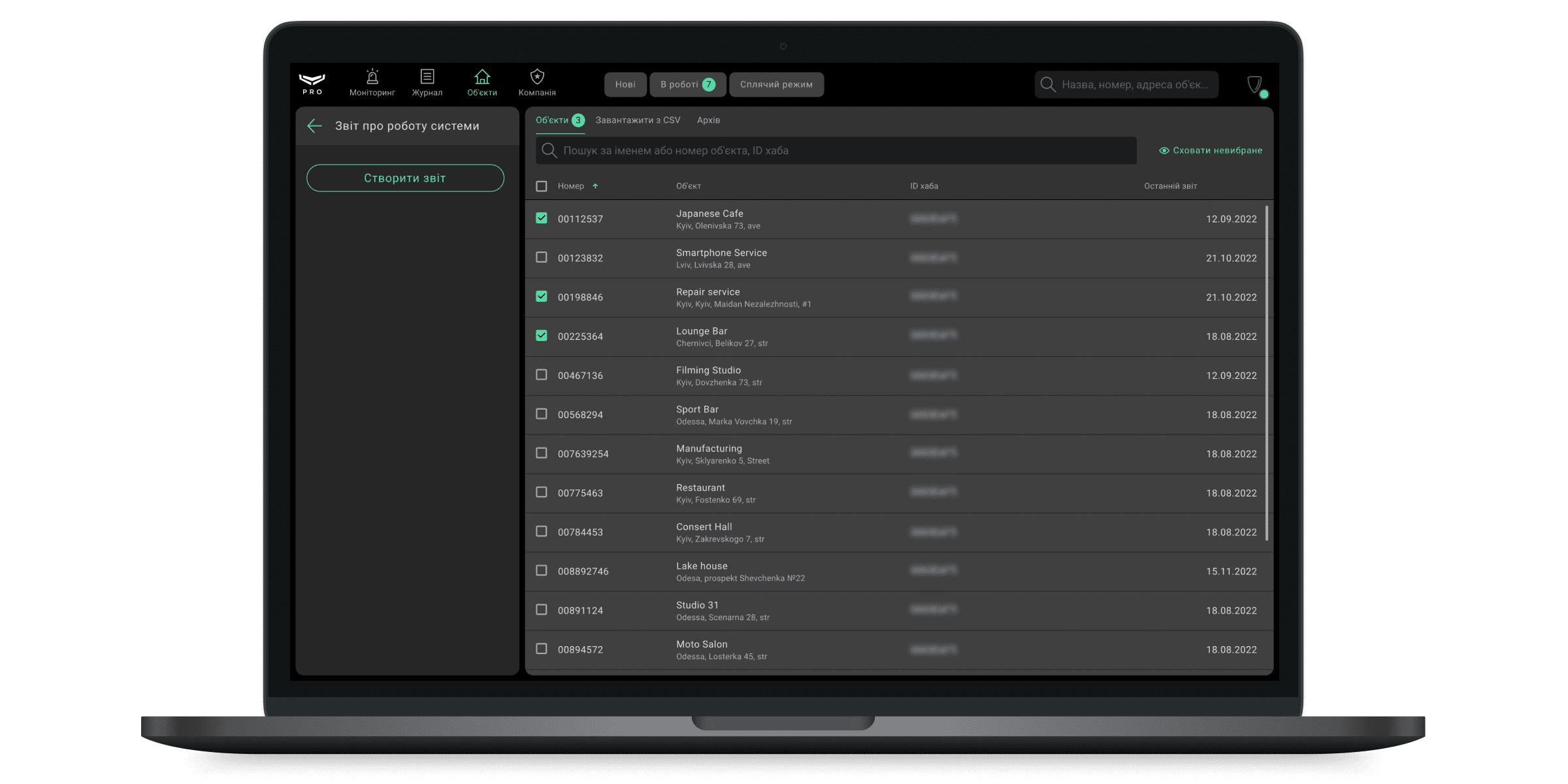
Вкладка Об’єкти
Усі об’єкти, за якими можна згенерувати звіти про роботу системи, знаходяться в цьому меню. Об’єкти можна відсортувати:
- За номером об’єкта.
- За назвою чи адресою об’єкта.
- За ID (ідентифікатором) хаба.
- За датою генерації останнього звіту.
Щоб згенерувати звіт, у меню Об’єкти:
- Виберіть потрібний об’єкт. Для зручної навігації ми передбачили пошук за ім’ям об’єкта, його номером, адресою, а також за ідентифікатором хаба. Якщо ви бажаєте приховати зайві об’єкти, увімкніть опцію Сховати невибране.
- Натисніть Створити звіт.
- Підтвердьте створення звіту, вибравши Створити.
- Дочекайтеся закінчення створення звіту.
- Перейдіть на вкладку Архів. Оберіть потрібні звіти.
- Натисніть Завантажити обране.
- Виберіть папку та збережіть файли.
Щоб вибрані звіти автоматично завантажувалися на ПК після створення, увімкніть опцію Автоматично завантажувати сформований звіт.
Пошук по вкладці обʼєкти
Пошуком по обʼєктах компанії може скористатися будь-який співробітник компанії (окрім власника компанії, якщо це його єдина роль). Можна скористатися пошуком для будь-якої категорії, в якій є обʼєкти, окрім категорій з секції Запит на моніторинг. Можна здійснювати пошук як для всіх обʼєктів, так і для вибраної категорії з меню Обʼєкти. В результаті пошуку відображається до 12 результатів, якщо потрібного результату серед них немає, необхідно уточнити запит.
Щоб скористатися пошуком:
- Натисніть на кнопку Пошук.
- Виберіть критерій пошуку:
- Базовий пошук – за назвою, номером, адресою обʼєкта, або ID хаба ( хаб ID необхідно вводити верхнім регістром).
- Імʼя хаба – за назвою пристрою, що вказана для хаба.
- Контактна особа – за телефоном або імʼям та прізвищем (в пошуку за контактною особою відображаються всі контактні особи даного обʼєкта).
- ID відеопристрою – за ID відеокамери, відеореєстратора або іншого відеопристрою.
- Договір – за номером договору або особою/компанією, з якою його укладено.
- Введіть в поле пошуку щонайменше 2 символи.
- Після виконання пошуку можна перейти до знайденого обʼєкта натиснувши на один з результатів пошуку.
Вивантаження даних у CSV
Дозвіл на вивантаження інформації у CSV файл може видавати лише власник компанії на вкладці Права доступу за допомогою опції Вивантаження даних обʼєкта. Мова файлу відповідає мові застосунку лише для Security state, інші поля завжди відображаються англійською мовою. Не вказані значення відображаються як «–».
Для того, щоб вивантажити інформацію по усім обʼєктам з певної категорії необхідно:
- Вибрати категорію з меню Обʼєкти.
- Натиснути на кнопку Вивантажити дані.
- Вибрати поля, які потрібно вивантажити:
- ID хаба (обовʼязкове поле)
- Номер обʼєкта (обовʼязкове поле)
- Назва обʼєкта
- Режим охорони
- Групи реагування (ГШР)
- Адреса
- Натиснути на кнопку Вивантажити дані.
- Натиснути на кнопку Завантажити.
- Вибрати папку до якої буде збережено CSV файл.
- Після успішного вивантаження на екрані зʼявиться відповідне повідомлення.
Вкладка Завантажити із CSV
Перетягніть потрібний файл CSV або завантажте його з комп’ютера, щоб сформувати звіт за потрібним списком об’єктів. CSV-файл має містити ID (ідентифікатори) хабів або номери об’єктів. Якщо ви завантажите файл у неправильному форматі, застосунок видасть помилку.
Після завантаження файлу звіти з потрібних об’єктів будуть згенеровані та доступні на вкладці Архів.
Зразок CSV у потрібному форматі файлу ви можете завантажити на вкладці Завантажити з CSV.
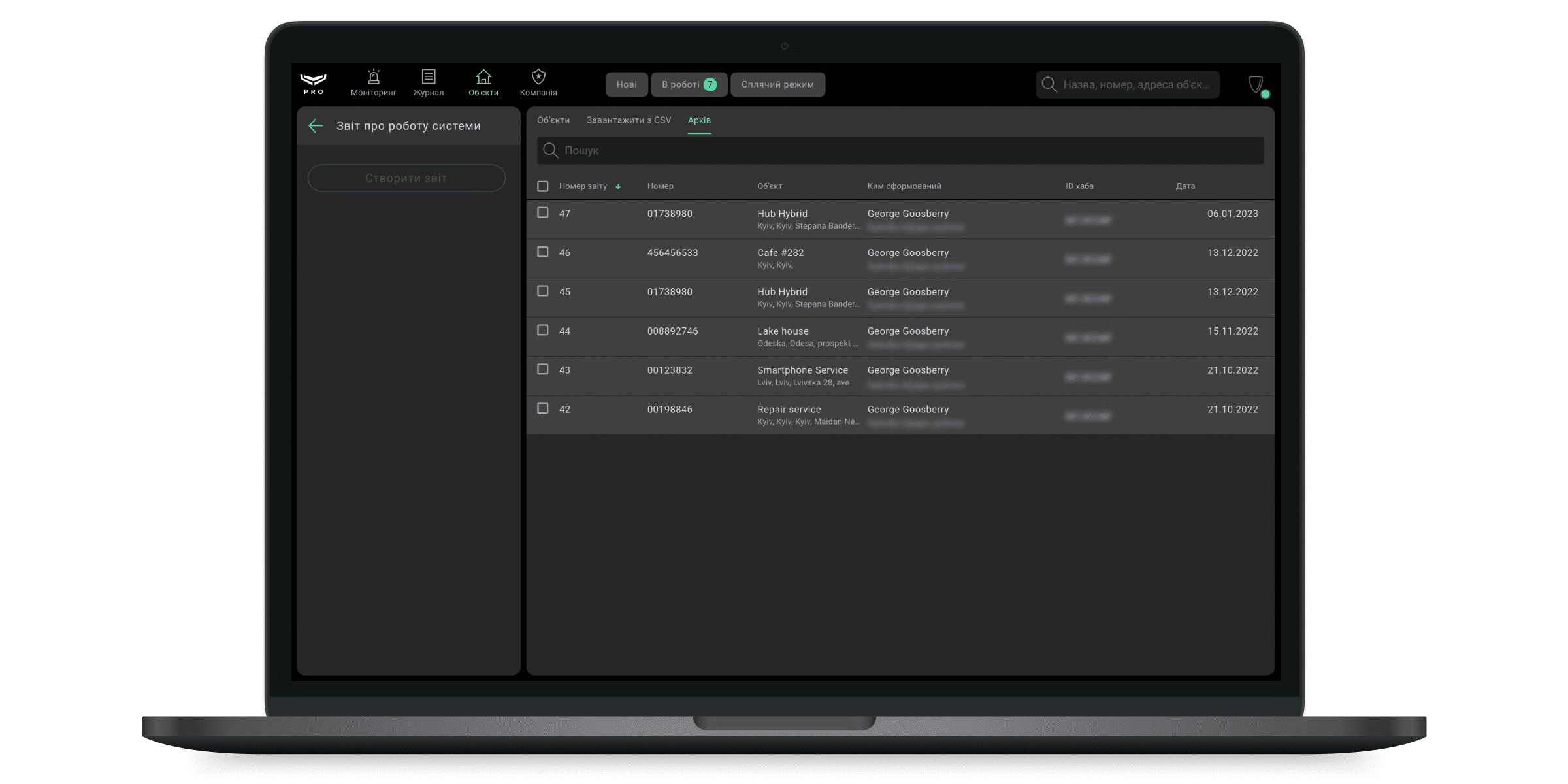
Вкладка Архів
Згенеровані звіти про роботу системи знаходяться на цій вкладці. У вкладці доступні лише останні 5 звітів для кожного з об’єктів. Раніші звіти буде видалено.
Об’єкти можна відсортувати:
- За номером звіту (що більше число, то новіший звіт).
- За номером об’єкта.
- За назвою або адресою об’єкта (одну з двох опцій можна вибрати, клацнувши на назву стовпця).
- За ім’ям або e-mail адресою співробітника компанії, який згенерував звіт (одну з двох опцій можна вибрати, клацнувши на назву стовпця).
- За ID (ідентифікатором) хаба.
Для зручної навігації ми передбачили пошук за ім’ям об’єкта, його номером, адресою, а також за ідентифікатором хаба.
Щоб завантажити звіт:
- Перейдіть на вкладку Архів.
- Оберіть потрібні звіти.
- Натисніть Завантажити обране.
- Виберіть папку та збережіть файли.
Вибравши об’єкт у вкладці Архів, ви також можете згенерувати новий звіт для об’єкта, якщо це потрібно.
PDF-файл звіту
PDF-файл звіту містить усю необхідну інформацію про об’єкт і стан усіх пристроїв системи безпеки. На початку кожного файлу, крім загальних даних, доступний також короткий підсумок перевірки: варто виїхати інженеру на об’єкт чи ні. Рекомендація виїхати на об’єкт з’являється у випадку, якщо хоча б в одного пристрою в системі виявлено несправність.
Назва файлу має такий формат: AA_XXXXXXXX_YYYYYYY_MM
- AA — підсумок перевірки.
- p — перевірку пройдено, звіт не містить несправностей.
- pw — перевірку пройдено, але звіт містить деякі несправності. Рекомендовано виїзд інженера на об’єкт для перевірки. Наприклад, якщо в одного з датчиків низький рівень сигналу з хабом чи цей датчик тимчасово вимкнений.
- f — перевірку не пройдено. Рекомендовано виїзд інженера на об’єкт для перевірки. Наприклад, один із датчиків втратив зв’язок із хабом.
- XXXXXXXX — дата створення звіту у форматі ДДММРРРР. Наприклад, 27032022.
- YYYYYYY — заданий номер об’єкта. Якщо номера немає, використовується ідентифікатор хаба.
- MM — номер звіту.
Моніторинг
Доступ до модуля: Власник компанії, Керівник ПЦС, Керівник операторів, Оператор.
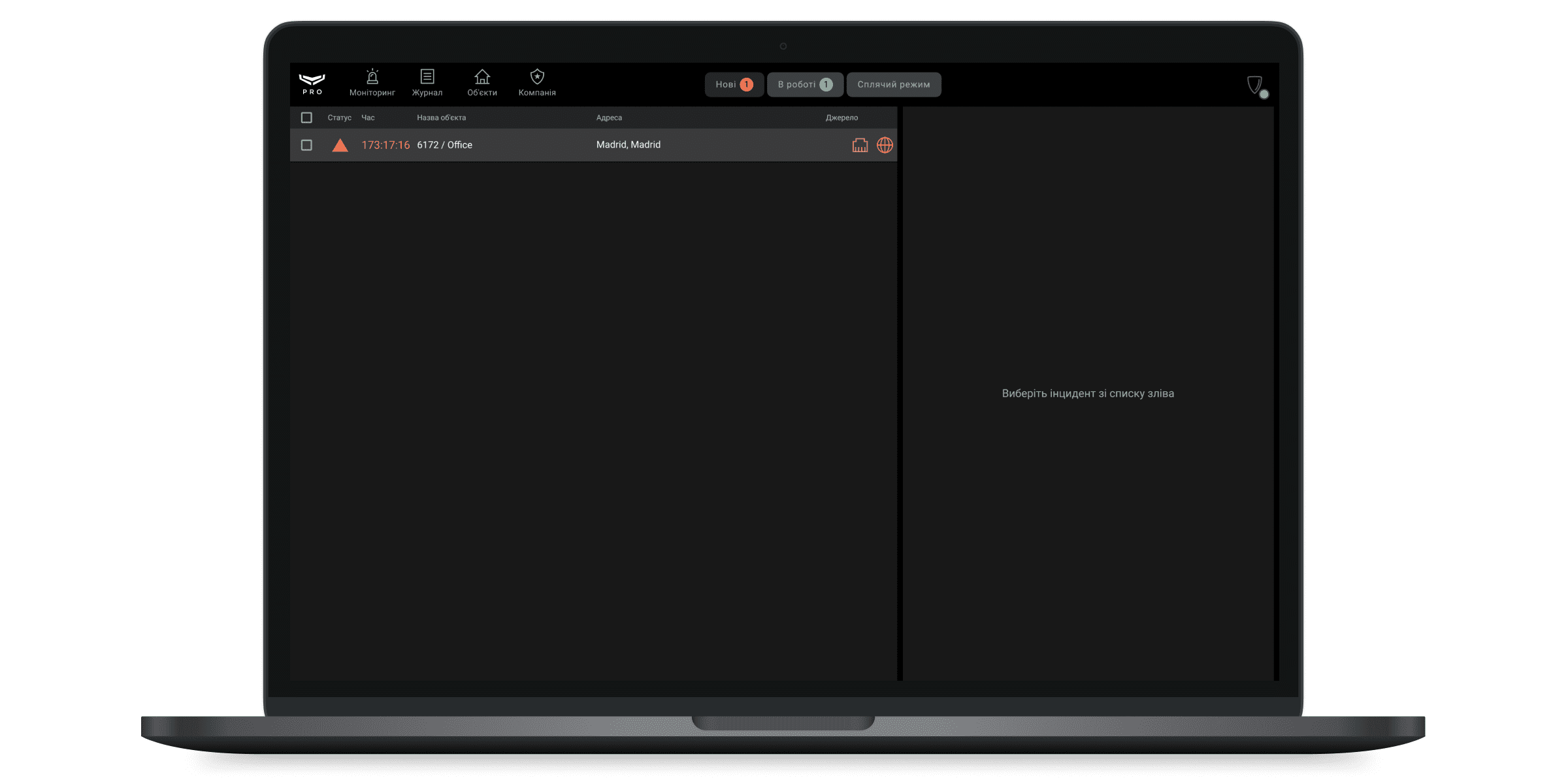
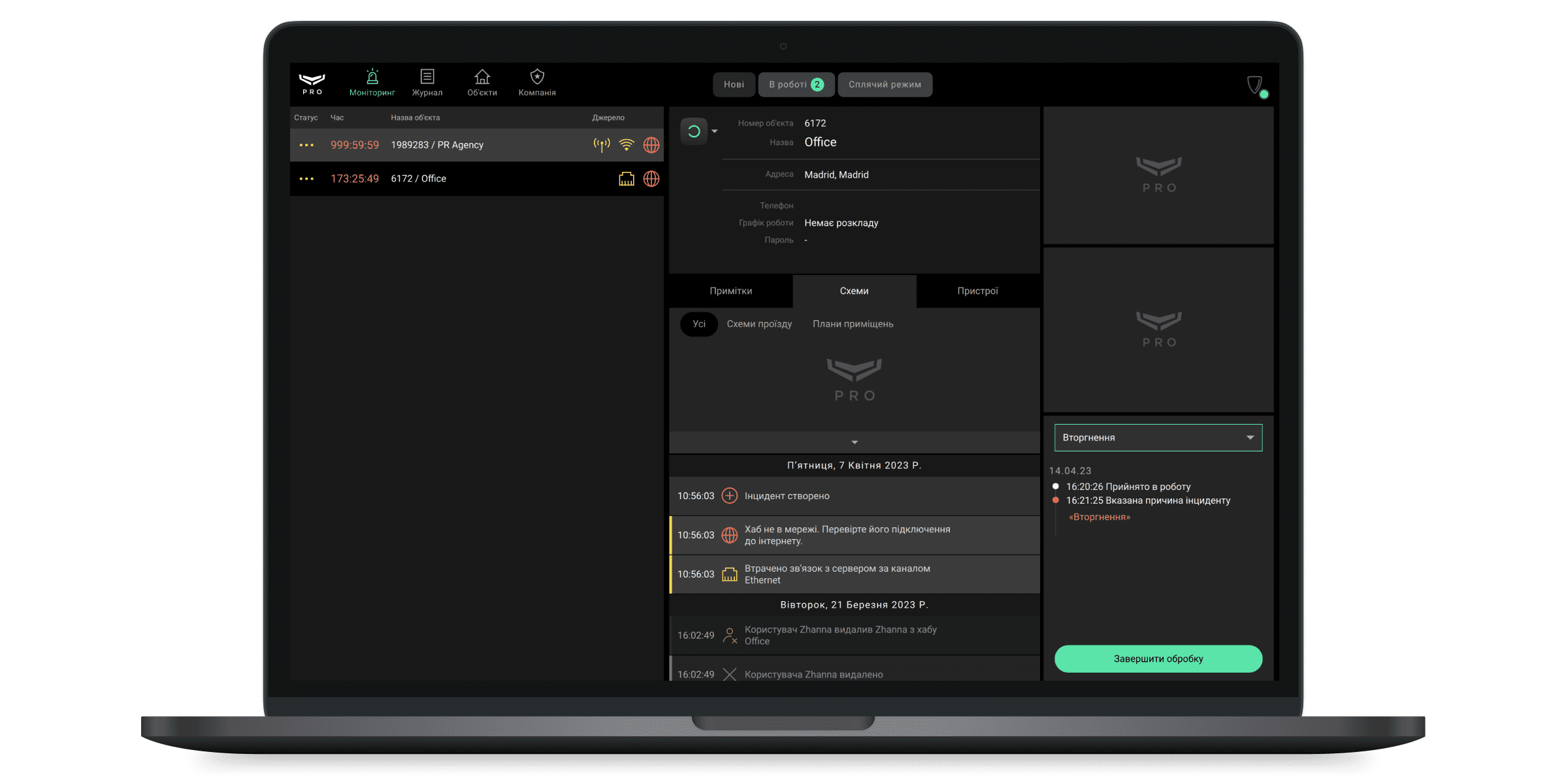
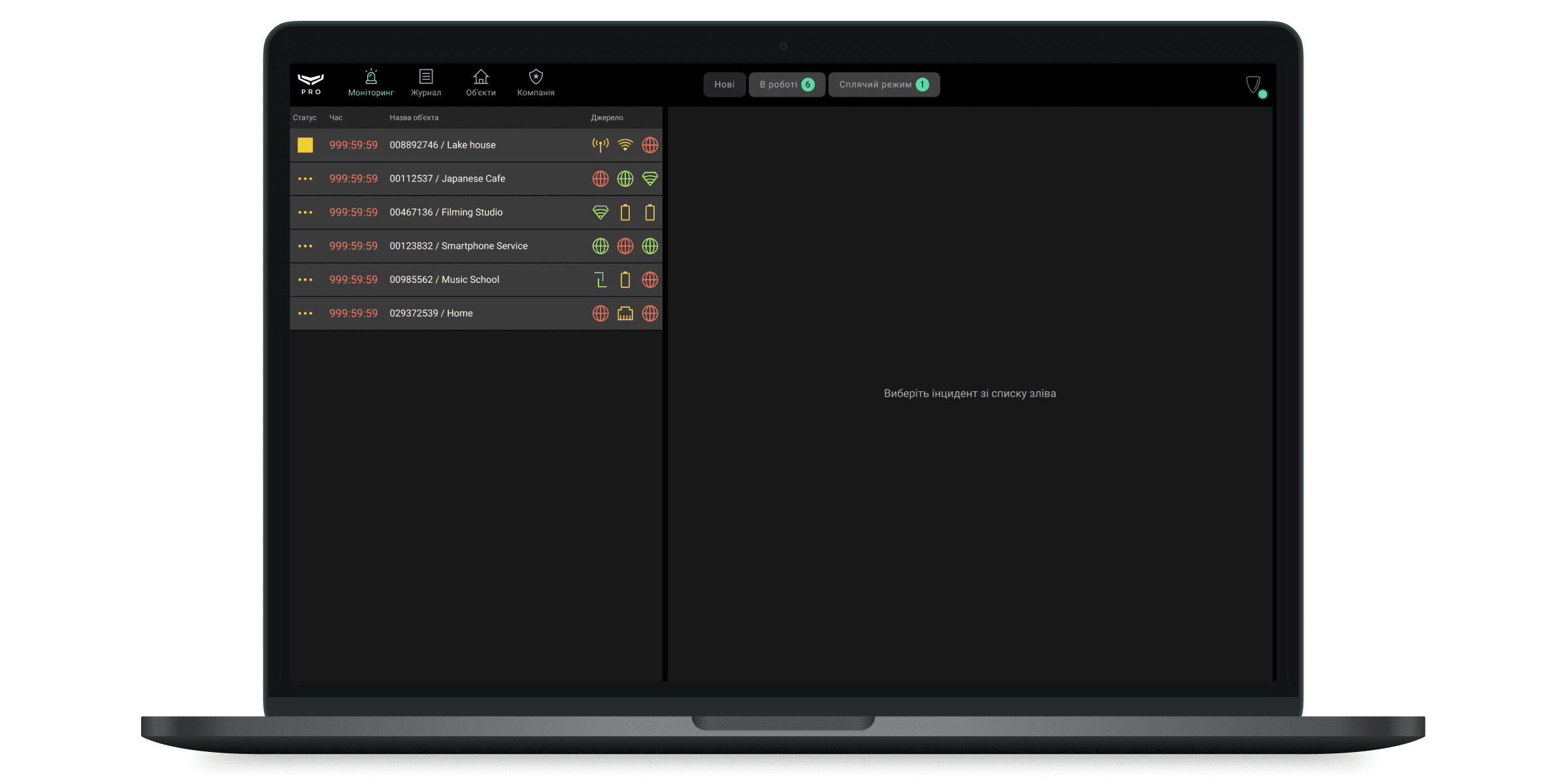
Модуль Моніторинг дозволяє обробляти події та тривоги систем Ajax, а також сповіщення про роботу операторів. Вкладки Нові, В роботі та Режим сну закріплені у верхній частині екрана Ajax PRO Desktop.
Нові тривожні сповіщення показані у вкладці Нові та до взяття в роботу супроводжуються звуком сирени. Інцидент не вважається закритим, поки його не закриє оператор. Одне сповіщення може містити кілька тривог або подій системи безпеки. Три останні з них зображуються у вигляді значків у рядку сповіщення, стовпець Джерело.
Інцидент створюється після таких подій систем Ajax:
- Тривоги датчиків.
- Спрацьовування тампера будь-якого пристрою системи.
- Спрацювання акселерометра сирен.
- Виявлення глушіння.
- Втрата зв’язку з будь-яким пристроєм системи.
- Втрата зв’язку хаба та сервера Ajax Cloud через один або всі канали зв’язку.
Система сповіщає користувача про події, які відбуваються після втрати хабом зв’язку з сервером. Сповіщення у стрічці подій містять дату і час, коли вони сталися. Якщо подій декілька, вони групуються у випадному списку. Кількість подій, що зберігаються в буфері хаба, можна встановити в налаштуваннях хаба.
- Втрата зовнішнього живлення централі, ретранслятора, vbfBridge або модулів інтеграції.
Сповіщення про втрату живлення на об’єкті можна вимкнути у меню Налаштування послуг в модулі Компанія.
- Будь-яка інша несправність пристроїв системи.
| Значення іконок тривог і подій системи | ||
| Іконка події | Опис | Іконка відновлення |
| Несправності | ||
 |
Пристрій <Імʼя пристрою> недоступний. Звʼязок каналом Jeweller втрачено. |
 |
 |
Втрачено звʼязок з сервером за каналом Ethernet |
 |
 |
Втрачено стільниковий звʼязок з сервером |
 |
 |
Втрачено звʼязок з сервером за каналом Wi-Fi |
 |
 |
Хаб не в мережі. Перевірте його підключення до інтернету. |
 |
 |
Живлення відсутнє |
 |
 |
Батарея розряджена |
 |
| Тривоги | ||
 |
Виявлено протікання |
 |
 |
Корпус хаба (пристрою) відкрито |
 |
 |
Зафіксовано рух | |
 |
Виявлено маскування датчика |
 |
 |
Розбито скло | |
  |
Відчинено |
  |
 |
Зафіксовано удар | |
 |
Зафіксовано нахил | |
 |
Зафіксовано тривогу, датчик ролета |
 |
 |
<Імʼя співробітника> натиснув кнопку тривоги | |
 |
Пристрій було зрушено | |
 |
Пожежна тривога | |
  |
Зафіксовано чадний газ (CO) |
 |
  |
Зафіксовано дим |
 |
 |
Тривогу тимчасово приглушено користувачем | |
  |
Температура перевищила порогове значення |
 |
 |
Витік газу |
 |
 |
Невідкладна допомога |
 |
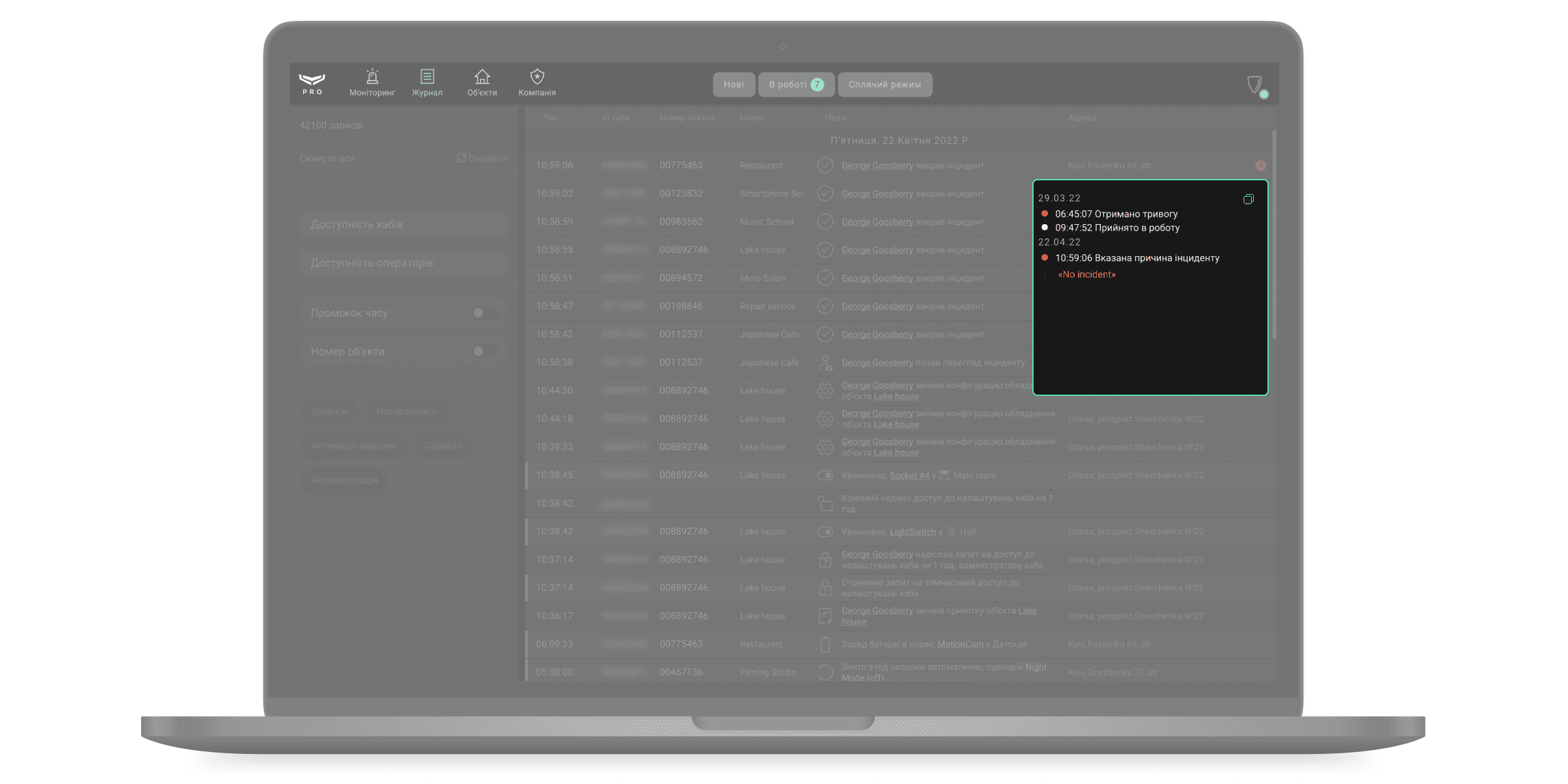
У рядку сповіщення зображується назва, адреса, номер об’єкта, а також статус і час перегляду інциденту оператором, що сплинув з моменту надходження тривоги. Хто з операторів та коли почав перегляд інциденту фіксується в модулі Журнал. Також у журналі фіксуються решта дій операторів з обробки інциденту: від взяття в роботу до закриття інциденту.
| Значки статусів перегляду інциденту оператором | |
 |
Інцидент створено |
 |
<Імʼя співробітника> почав перегляд інциденту |
 |
<Імʼя співробітника> взяв в роботу інцидент |
 |
<Імʼя співробітника> закрив інцидент |
Інциденти операторів
Окремо у списку показані інциденти зникнення зв’язку з оператором та входи оператора до PRO-акаунта з непідтвердженого комп’ютера. Ці типи інцидентів формуються згідно з робочими місцями операторів, які підтверджені в модулі Компанія, та обробляються як тривоги систем безпеки — із зазначенням причини інциденту та фіксацією в журналі.
Сповіщення Оператор не в мережі – тип інциденту, який містить інформацію про втрату з’єднання з комп’ютером, який підтверджено як робоче місце оператора в модулі Компанія.
Сповіщення Вхід з непідтвердженого комп’ютера – тип інциденту, який містить інформацію про користувача та комп’ютер, з якого здійснено вхід.
Обробка інциденту
Алгоритм обробки інцидентів
- Надсилання хабом тривоги системи Ajax.
- Автоматичне створення Інциденту в модулі Моніторинг.
- Перегляд Інциденту оператором ПЦС або керівником операторів.
- Взяття в роботу Інциденту оператором ПЦС або керівником операторів.
- Перевірка причини тривоги: зв’язок із контактними особами, перевірка фото, що надано датчиками з фотоверифікацією.
- Якщо тривога є реальною або встановити причину тривоги неможливо: надсилання ГШР. Після з’ясування причин тривоги – завершення обробки інциденту із зазначенням причини тривоги.
- Якщо тривога хибна: зазначення причини тривоги як «Хибне спрацювання» або «Немає інциденту» і завершення обробки інциденту.
Інформація на екранах обробки інцидентів
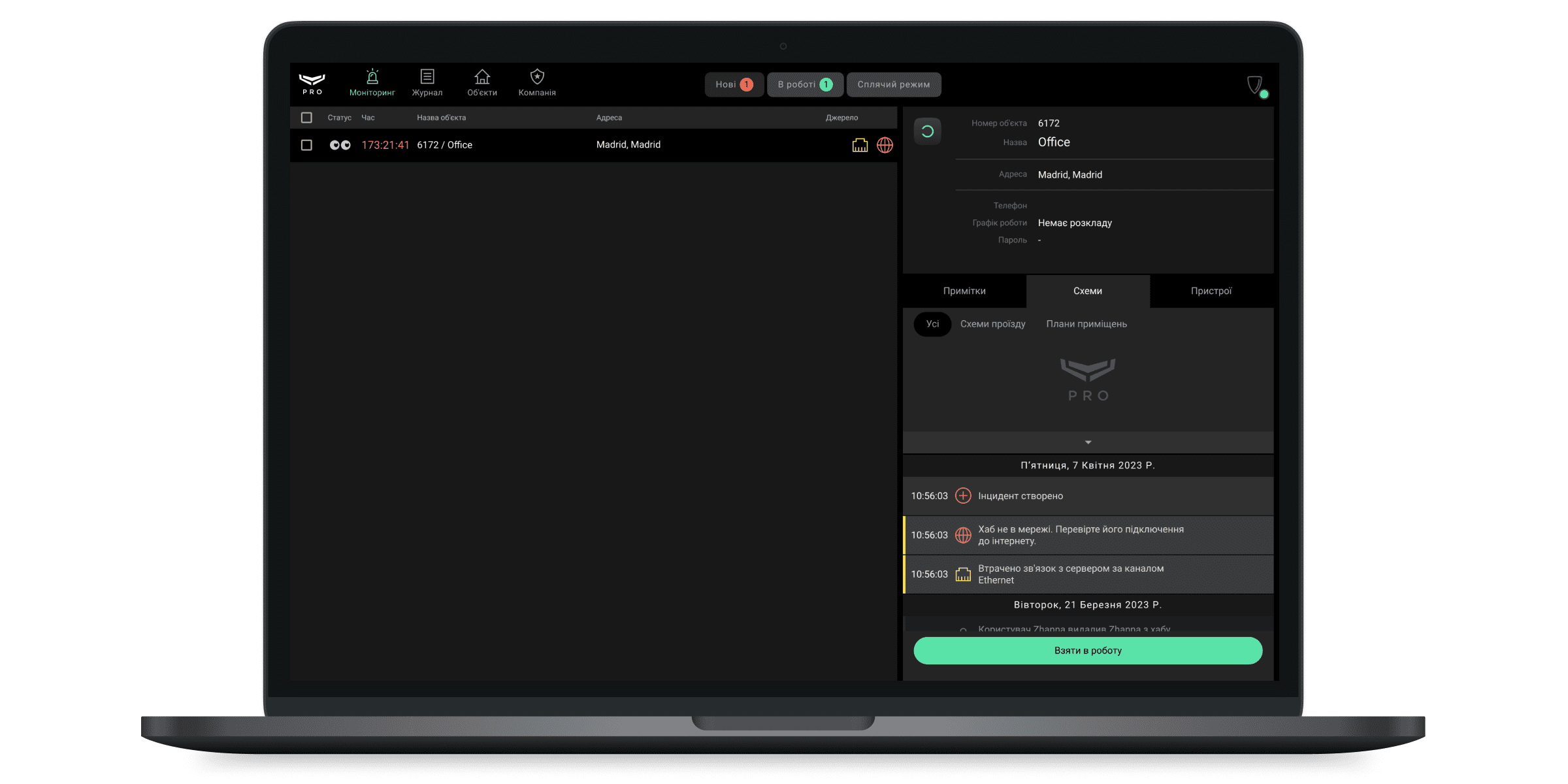
Після натискання на сповіщення відкриваються:
- Деталі інциденту — час тривоги, пристрій, що спрацював, кімната, фотопідтвердження (якщо спрацювали датчики з фотоверифікацією).
- Інформація про об’єкт — адреса, контакти, схеми приміщень та інше.
Оператор починає обробку тривоги з натискання кнопки Взяти в роботу, після цього інцидент переходить у вкладку В роботі. Оператор має обмежений доступ до вкладки: він бачить лише ті інциденти, які взяв у роботу. У Керівника операторів є повний доступ — він бачить всі інциденти в роботі в операторів і може закривати кілька інцидентів за один раз.
У центрі вкладки В роботі зображується основна інформація про об’єкт, список тривог, меню керування режимами охорони, а також примітки, перелік пристроїв, схеми проїзду та приміщень.
Якщо на об’єкті встановлено датчики руху з фотоверифікацією, для перевірки причини тривоги оператор може переглянути серії фотографій, зроблені датчиком. Фотографії зображується у вкладці MotionCam у хронологічному порядку, від останньої.
Оператор може зв’язатися з однією із зазначених у картці об’єкта відповідальних осіб — під час обробки тривоги їхні ім’я та номери телефонів показані на екрані застосунку. Ajax PRO Desktop не підтримує дзвінки із застосунку. Але оператор може скопіювати номер телефону відповідальної особи та зателефонувати їй за допомогою стороннього ПЗ. Наприклад, за допомогою застосунку для IP-телефонії.
Відповідальні особи призначаються під час створення об’єкта в Ajax PRO Desktop. Це може бути, наприклад, власник квартири або керівник служби безпеки на виробництві.
Оператор фіксує результати зв’язку і ставить позначку Дзвінок прийнято — якщо вдалося зв’язатися й відповідальна особа прийняла інформацію. Якщо зв’язку з відповідальною особою немає, то оператор ставить позначку Немає зв’язку. Перемикатися між відповідальними особами можна за допомогою стрілок. Вони з’являються, якщо всі відповідальні особи не можуть бути зображені у поточному розмірі вікна застосунку.
Закріплені за об’єктом групи швидкого реагування зображуються під відповідальними особами. Підтримуючи зв’язок із ГШР, оператор відзначає, коли група Надіслана, Прибула або Недоступна. Перемикатися між закріпленими групами можна за допомогою стрілок. Вони з’являються, якщо всі ГШР не можуть бути зображені у поточному розмірі вікна застосунку.
ГШР призначаються під час створення об’єкта в Ajax PRO Desktop.
Лог обробки інциденту зображено у правому нижньому куті екрана. Оператор може натиснути на кожний запис з логу, щоб залишити коментар до нього. У верхній частині логу обробки можна вибрати причину тривоги зі списку, що розгортається, та завершити обробку. При необхідності — причину тривоги можна доповнити коментарем. Наприклад, щоб детальніше описати причину хибної тривоги на об’єкті.
Під час обробки інциденту, пов’язаного з робочим місцем оператора, можна вказати причину зі списку, що розгортається, і за необхідності — супроводити коментарем. Під час обробки інциденту про вхід оператора з непідтвердженого комп’ютера, робоче місце можна підтвердити в цьому ж вікні. Щоб зробити це, натисніть кнопку «+» поруч із даними оператора.
Після завершення обробки інциденту його буде закрито й передано до Журналу, де зберігається лог його обробки. Повернутися до обробки інциденту неможливо.
Voice Connect
Voice Connect гарантує безпечний двосторонній голосовий зв’язок між оператором ПЦС та обʼєктом, що охороняється. Функція працює безпосередньо в Ajax PRO Desktop — зовнішній софт або SIP-інфраструктура не потрібні. Оператори можуть дзвонити на обʼєкт за допомогою SpeakerPhone Jeweller прямо з інтерфейсу Ajax PRO Desktop.
Ця функція доступна для моніторингових компаній і дає змогу власнику компанії, керівнику операторів та оператору ініціювати дзвінки.
Щоб скористатися цією функцією, PRO-користувач має додати щонайменше один SpeakerPhone Jeweller до хаба Ajax з OS Malevich 2.33 або новішою версією. Ця функція доступна в Ajax PRO Desktop версії 5.29 або новішої.
Як налаштувати Voice Connect
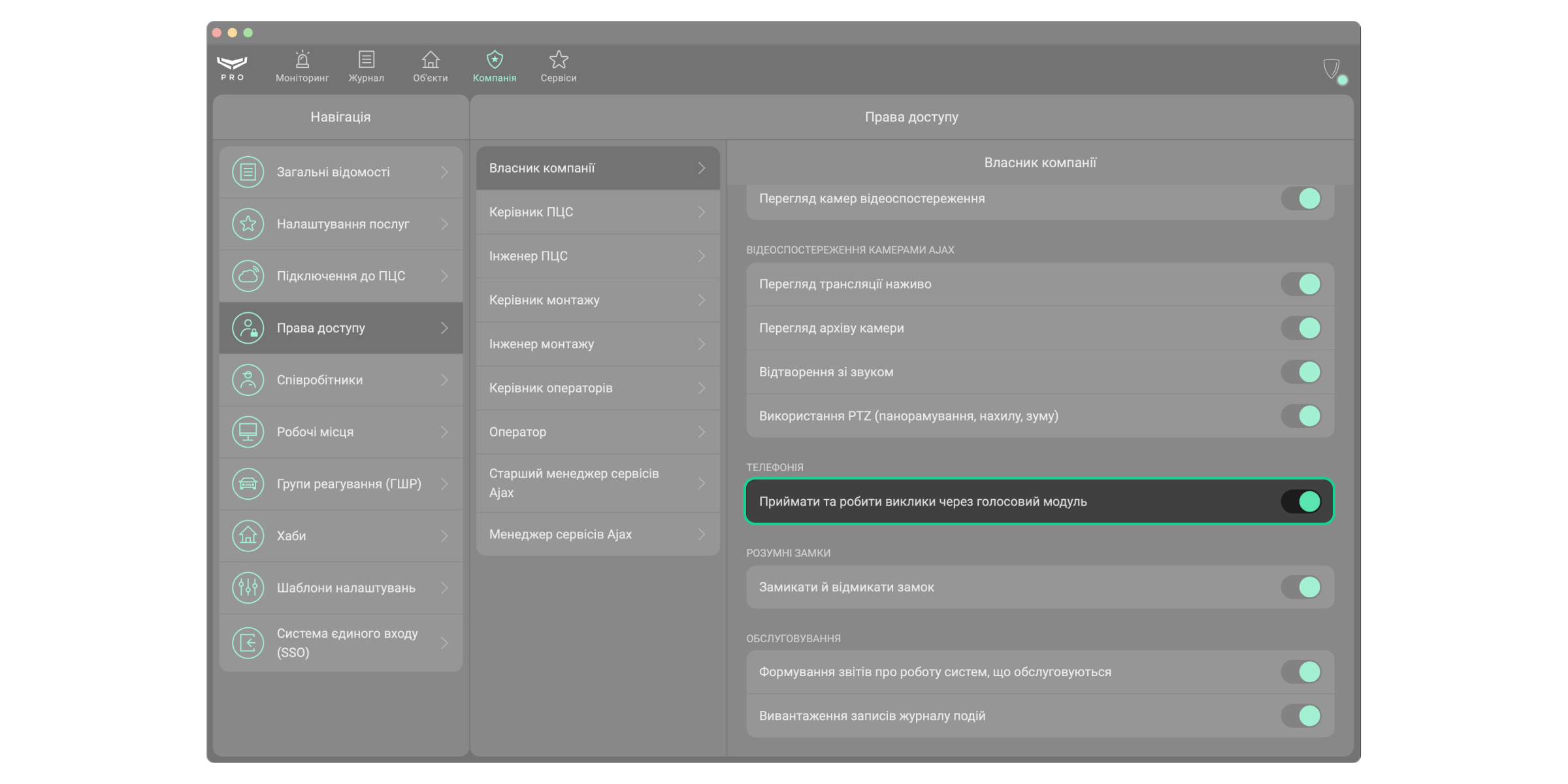
Спершу налаштуйте права доступу. Для цього відкрийте застосунок Ajax PRO Desktop:
- Перейдіть у модуль Компанія.
- Перейдіть у меню Права доступу.
- Виберіть потрібну роль — Власник компанії, Керівник операторів або Оператор.
- Увімкніть опцію Приймати та робити виклики через голосовий модуль.
- Повторіть ці кроки для інших ролей, якщо потрібно.
Після цього налаштуйте телефонію в застосунку Ajax PRO Desktop:
- Перейдіть у модуль Обʼєкти.
- Виберіть потрібний обʼєкт.
- Клацніть іконку
, щоб перейти до налаштувань хаба.
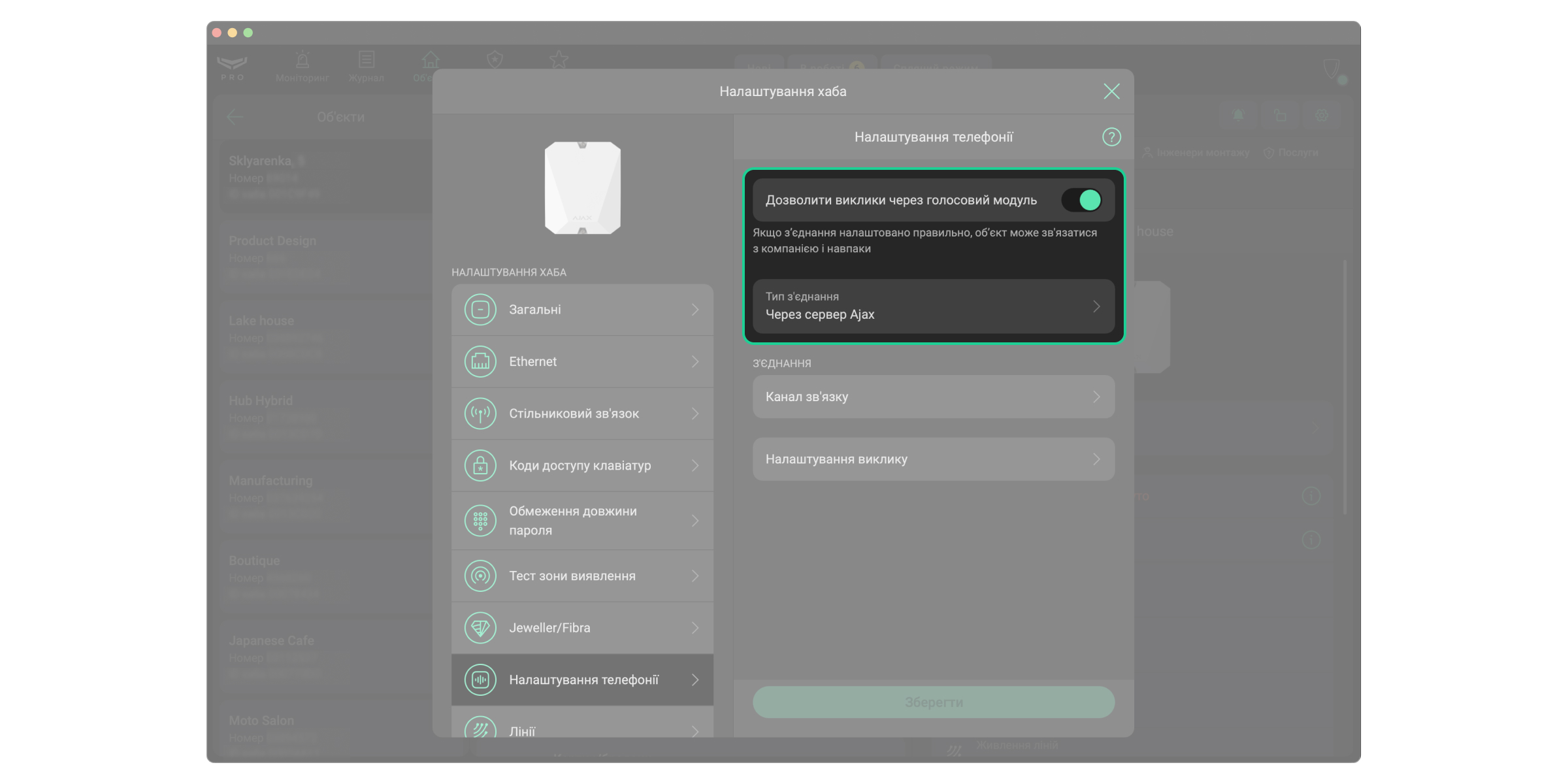
- Перейдіть у Налаштування телефонії.
- Увімкніть опцію Дозволити виклики через голосовий модуль.
- Переконайтеся, що в полі Тип з’єднання вибрано Через сервер Ajax.
- Налаштуйте Канал звʼязку та Налаштування виклику відповідно до параметрів вашої системи. Клацніть Зберегти, щоб застосувати зміни.
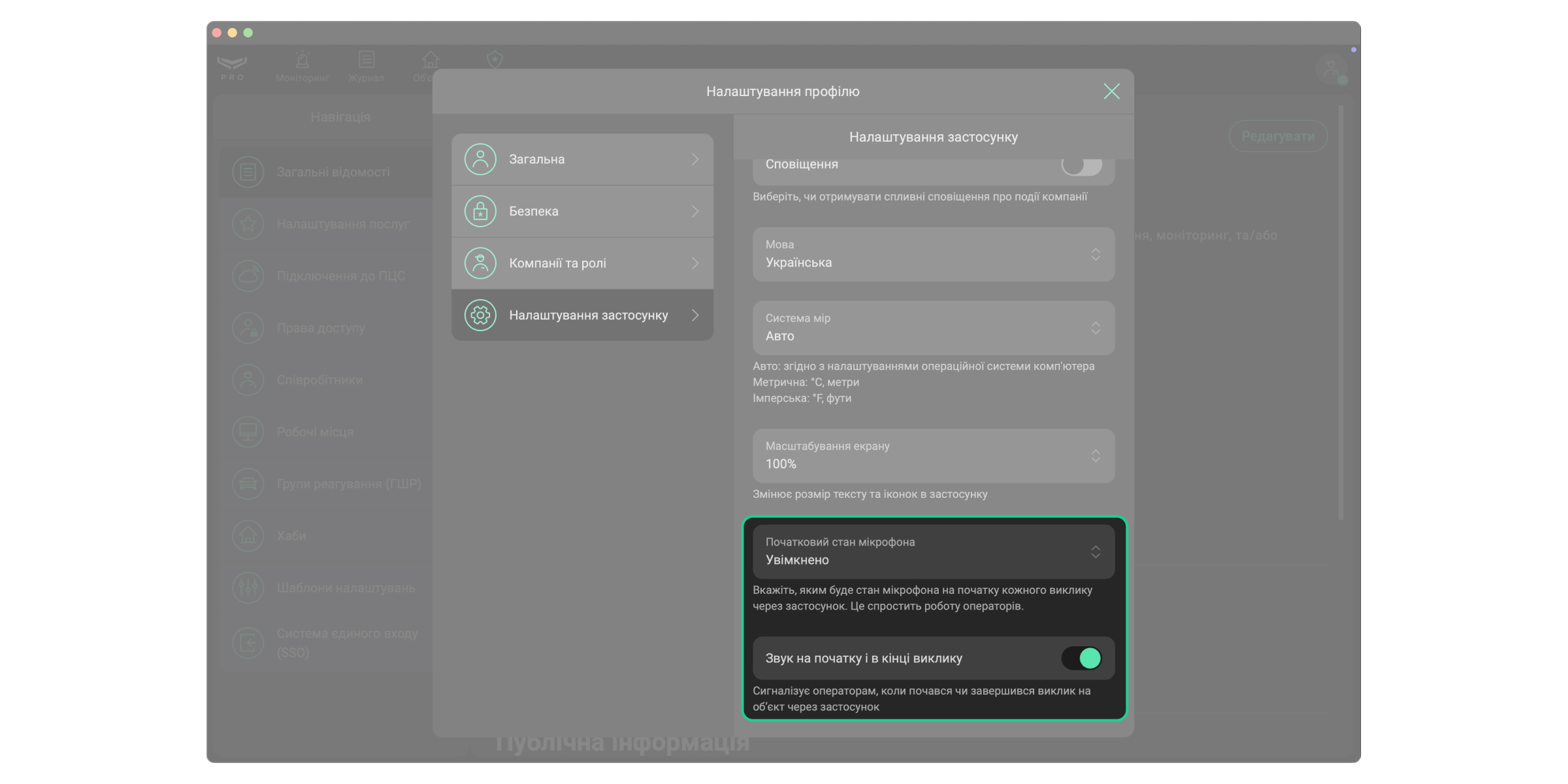
Крім того, ви можете налаштувати початковий стан мікрофона та звукову індикацію виклику. Для цього в застосунку Ajax PRO Desktop:
- Перейдіть у Налаштування профілю.
- Виберіть Налаштування застосунку.
- Установіть Початковий стан мікрофона: виберіть, чи буде мікрофон вимкненим на початку виклику через Ajax PRO Desktop.
- Увімкніть або вимкніть Звук на початку і в кінці виклику — звуковий сигнал, який сповіщає операторів про початок або закінчення виклику.
Як здійснити виклик
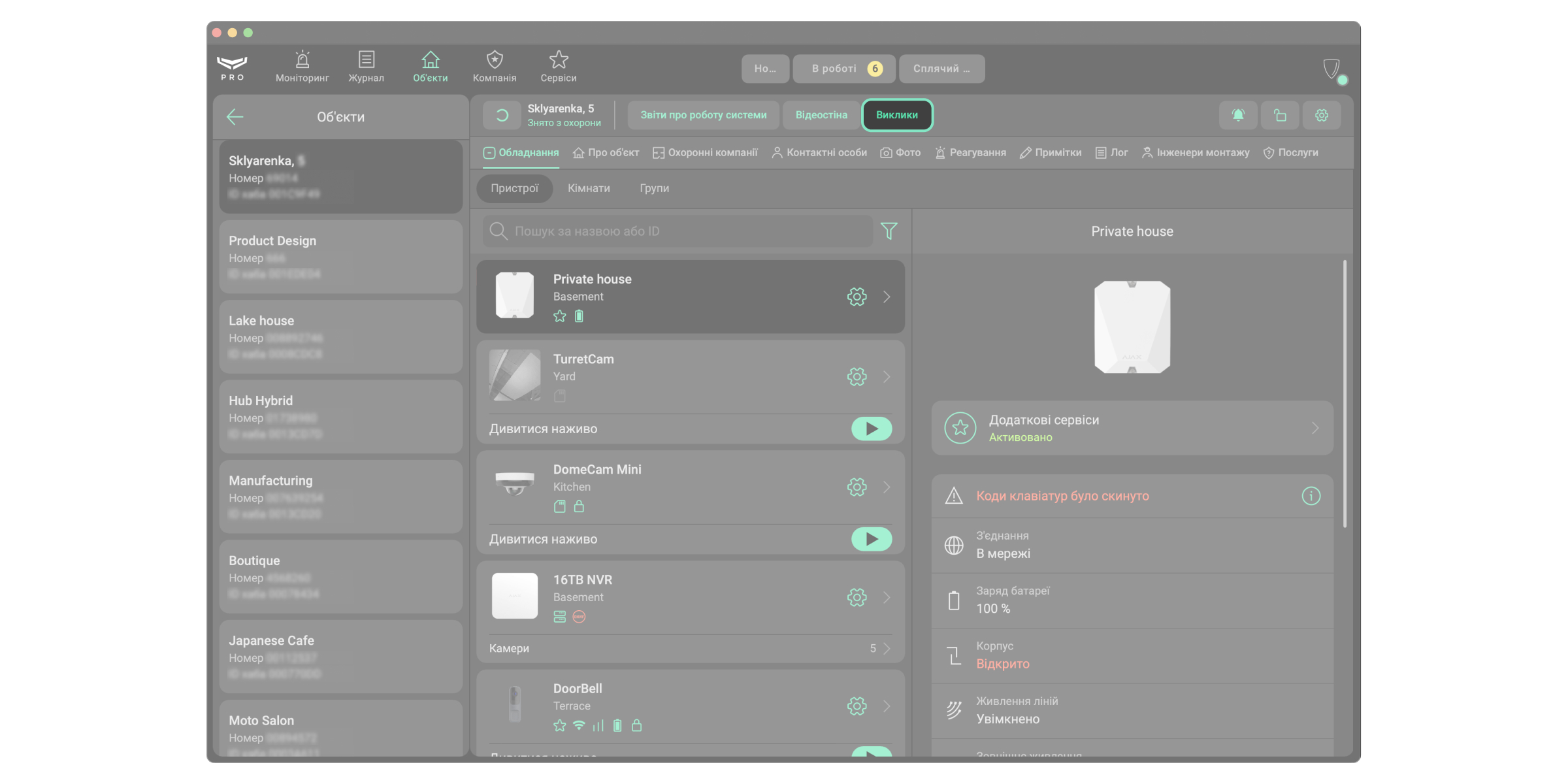
Власник компанії, керівник операторів та оператор можуть ініціювати виклики за допомогою голосового модуля в застосунку Ajax PRO Desktop. Ця функція доступна як в модулі Об’єкти, так і в модулі Моніторинг.
Зверніть увагу, що під час першого виклику компʼютер може запросити доступ до мікрофона. Обовʼязково надайте цей дозвіл, щоб увімкнути голосовий звʼязок.
Щоб здійснити дзвінок через модуль Обʼєкти:
- Відкрийте застосунок Ajax PRO Desktop та перейдіть у модуль Обʼєкти.
- Виберіть потрібний обʼєкт.
- Клацніть Виклики.
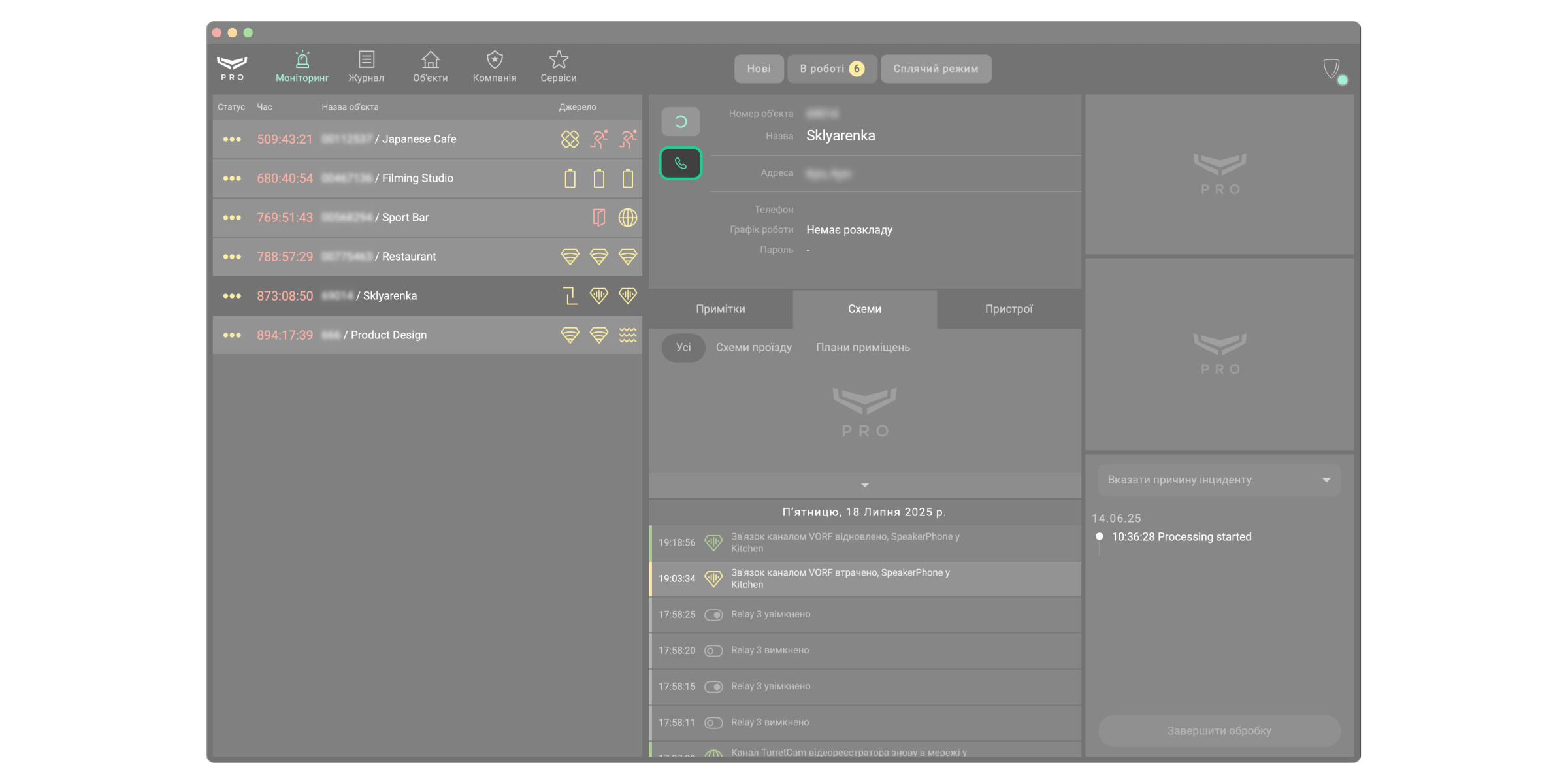
Щоб здійснити дзвінок через модуль Моніторинг:
- Відкрийте застосунок Ajax PRO Desktop та перейдіть у модуль Моніторинг.
- Виберіть потрібний інцидент.
- Клацніть іконку телефона.
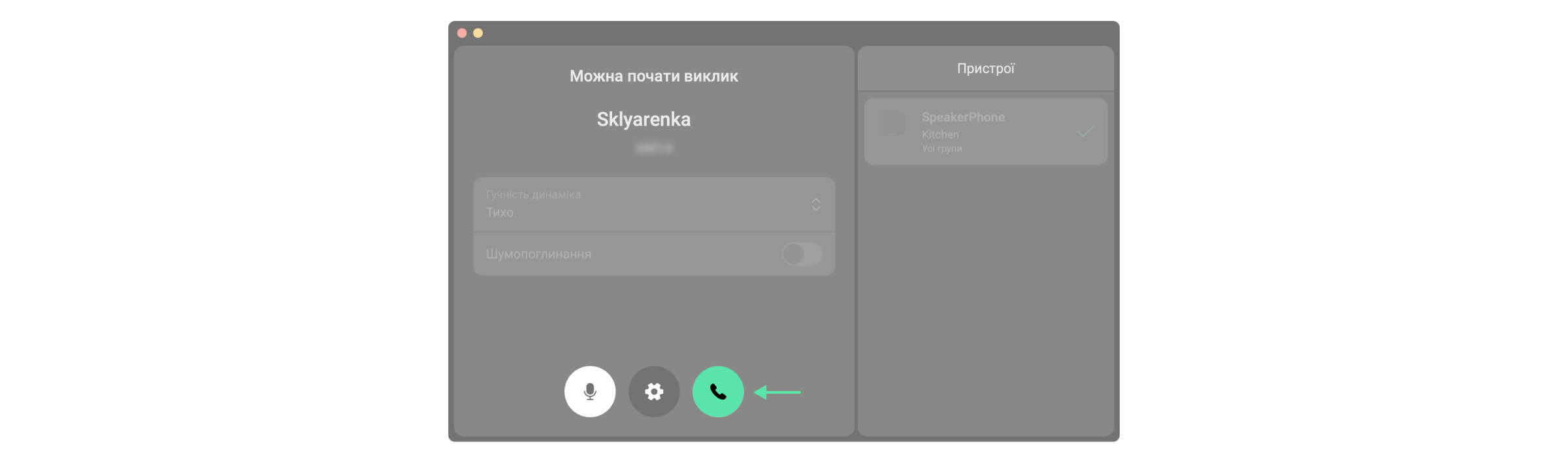
Натискання на кнопку виклику в модулях Обʼєкти або Моніторинг відкриває окреме вікно, в якому можна:
- налаштувати гучність динаміка;
- увімкнути або вимкнути шумопоглинання;
- увімкнути режим трансляції голосу на всі пристрої (доступно, коли до хаба Ajax додано два або більше пристроїв SpeakerPhone Jeweller);
- увімкнути зменшення фонового шуму;
- перемикатися між голосовими модулями, якщо до простору додано кілька пристроїв SpeakerPhone Jeweller;
- увімкнути або вимкнути мікрофон оператора;
- завершити виклик.
Режим сну
Співробітник, який має доступ до модуля моніторингу, може перевести об’єкт у Режим сну, якщо на ньому проводяться інженерні роботи або від нього надходять хибні тривоги. Об’єкти, тривоги та події яких тимчасово ігноруються — відображені у вкладці Режим сну. Перевести об’єкт у Режим сну можна у меню керування режимами охорони.
Під час активації Режиму сну оператор задає проміжок часу, після якого об’єкт повернеться до штатного режиму роботи. Можна вибрати 1, 5, 15 або 30 хвилин, а також вказати час вручну: від 1 до 300 хвилин.
Поки об’єкт перебуває у Режимі сну, Ajax PRO Desktop ігнорує його тривоги та події — вони не відображаються у вкладці Інциденти, але фіксуються в модулі Журнал. Після завершення встановленого часу об’єкт автоматично повертається до штатного режиму роботи.
Щоб вимкнути Режим сну на об’єкті до закінчення встановленого періоду:
- Відкрийте меню керування режимами охорони.
- Вимкніть Режим сну.
Журнал
Доступ до модуля: Власник компанії, Інженер ПЦС, Керівник ПЦС, Керівник операторів, Оператор, Керівник монтажу.
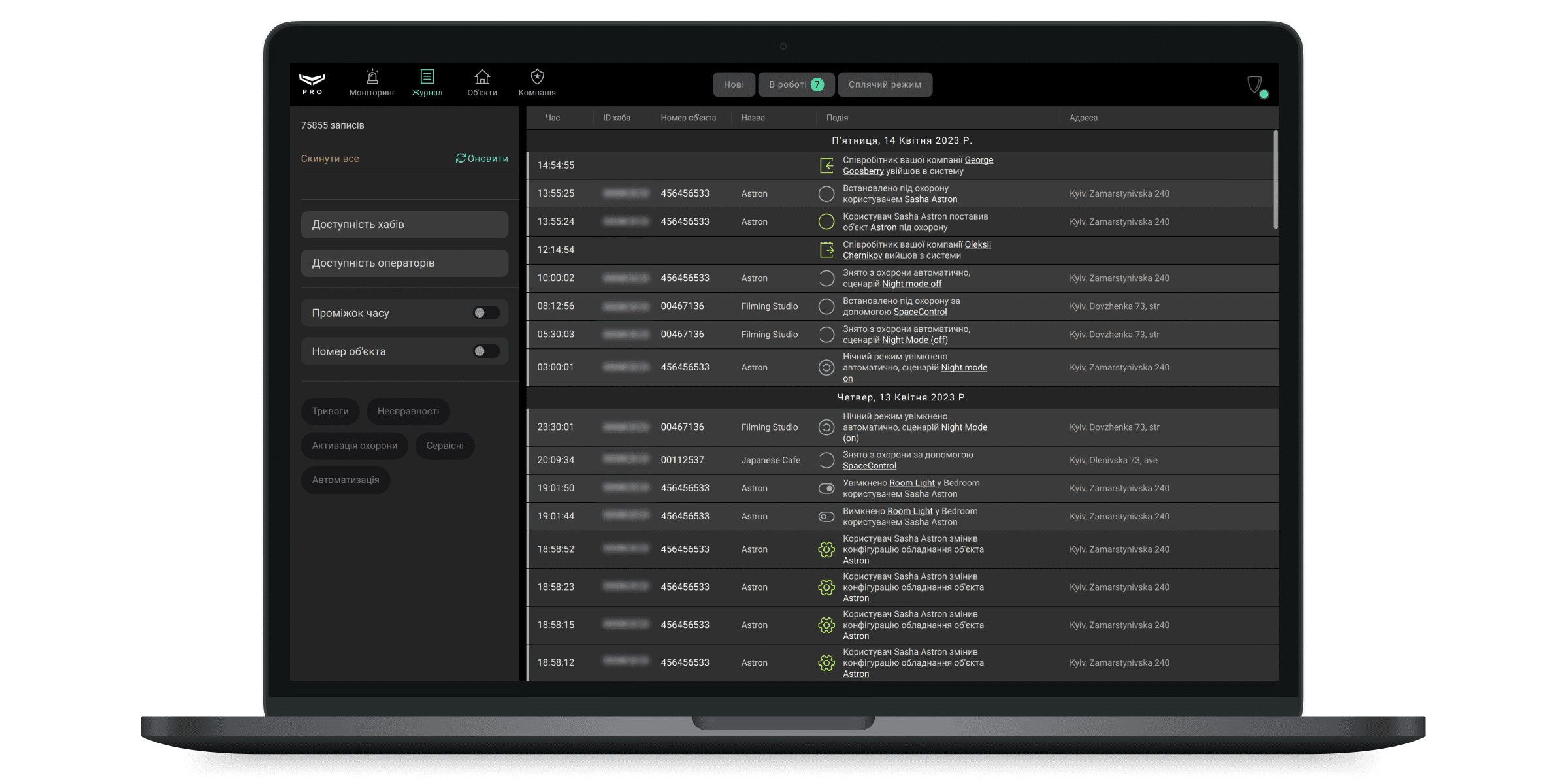
Ajax PRO Desktop веде журнал тривог та подій усіх об’єктів компанії, а також дозволяє формувати звіти про доступність хабів та операторів ПЦС. Також, журнал містить інформацію про завантаження фрагментів відеозаписів з архіву, що дає змогу відстежити хто, коли і який фрагмент завантажив. Щоб перейти до нього — виберіть Журнал у списку модулів застосунку.
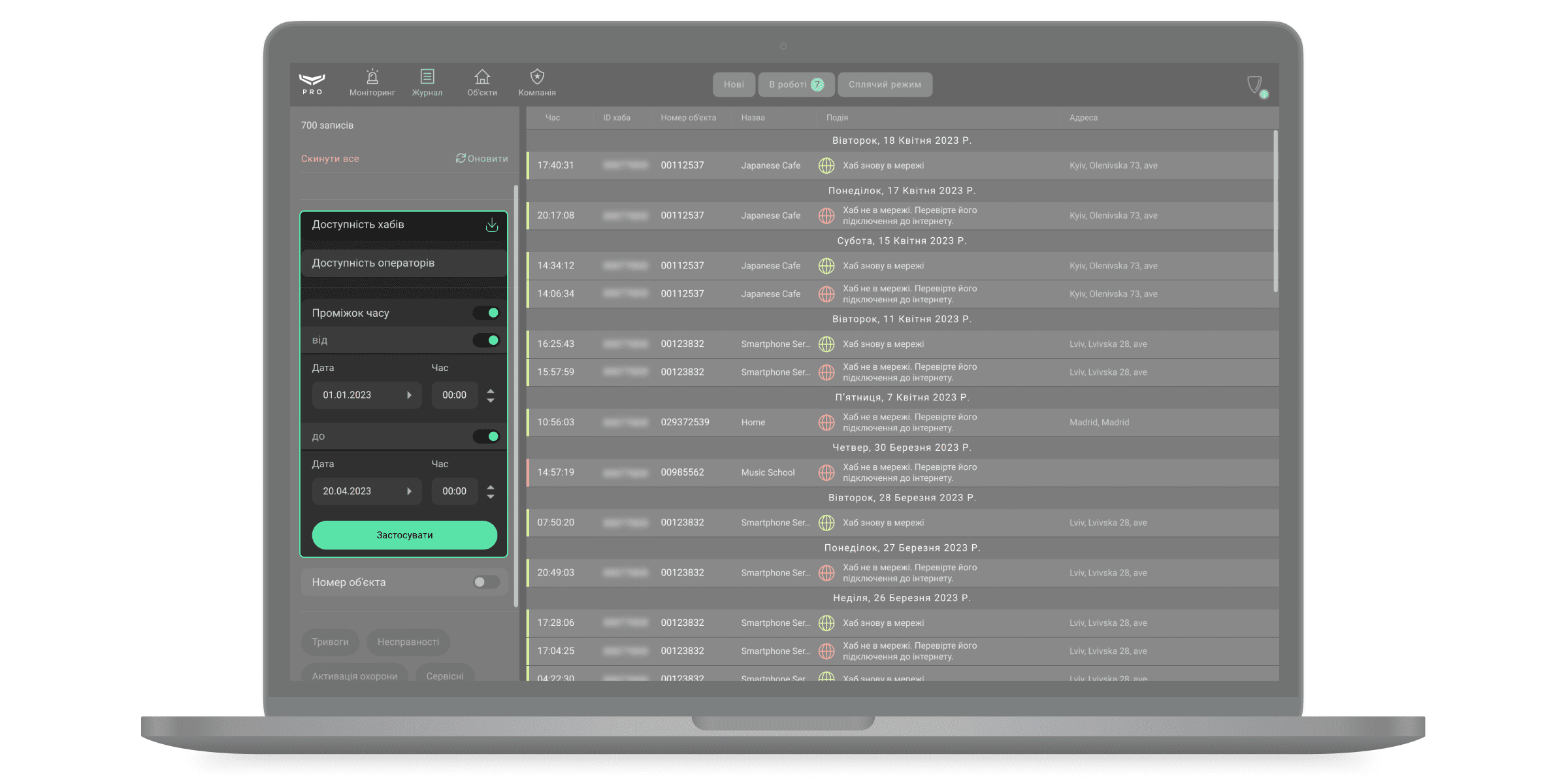
Сповіщення об’єктів зображуються у хронологічному порядку. Щоб встановити часовий інтервал сповіщень, їхній тип або номер об’єкта — скористайтеся фільтрами. Над фільтрами зображується лічильник відсортованих записів, а також кнопки скидання фільтрів та оновлення журналу.
Щоб відфільтрувати сповіщення за пристроєм або користувачем, натисніть на них у списку сповіщень. Натисніть на номер об’єкта в стовпці, щоб відфільтрувати сповіщення цього об’єкта. Сповіщення також можуть бути відфільтровані натисканням на значок події — ви отримаєте список усіх подій одного типу.
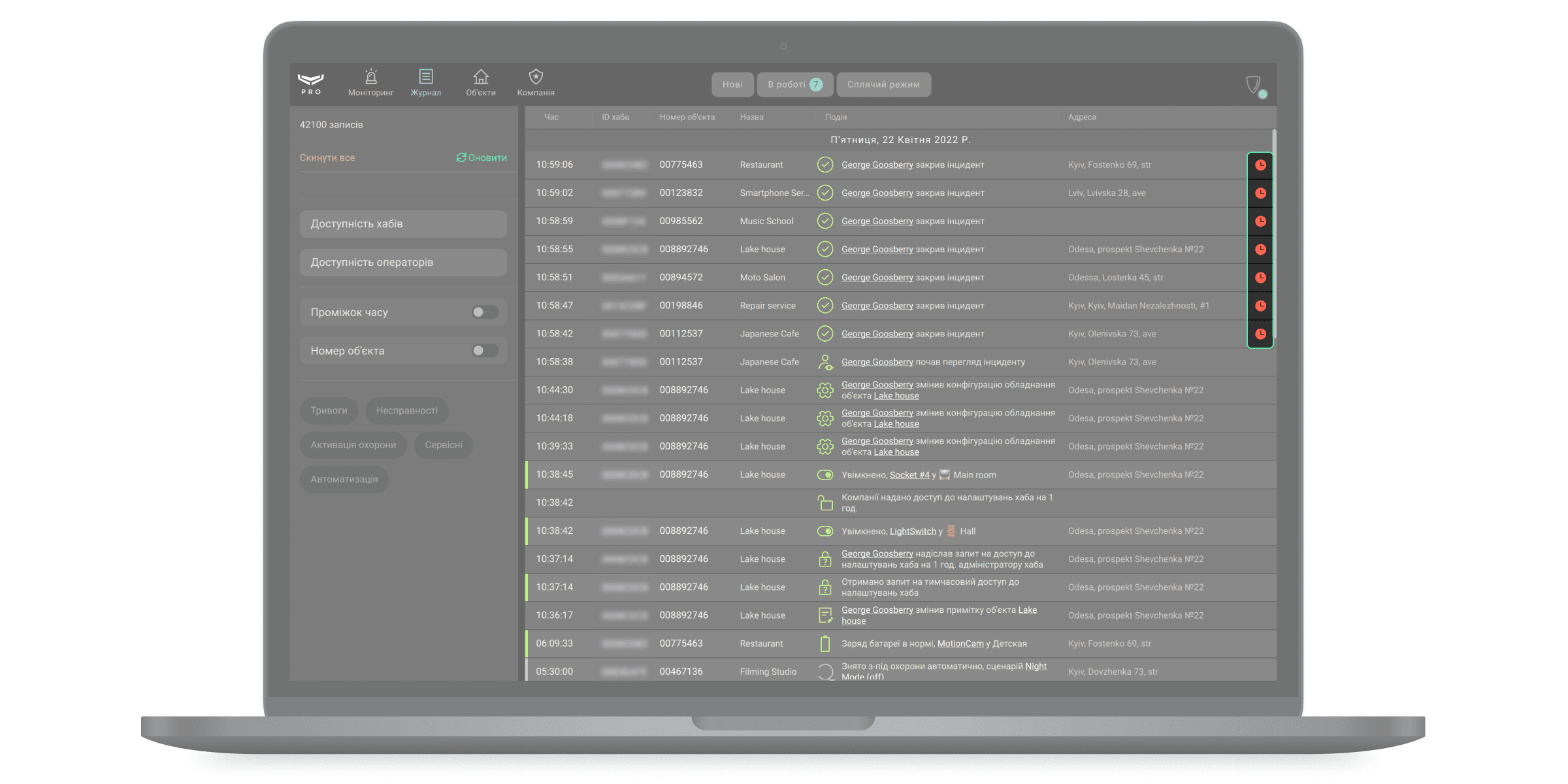
Щоб відкрити лог обробки інциденту, натисніть на значок годинника у записі про завершення обробки інциденту.
Звіти про доступність
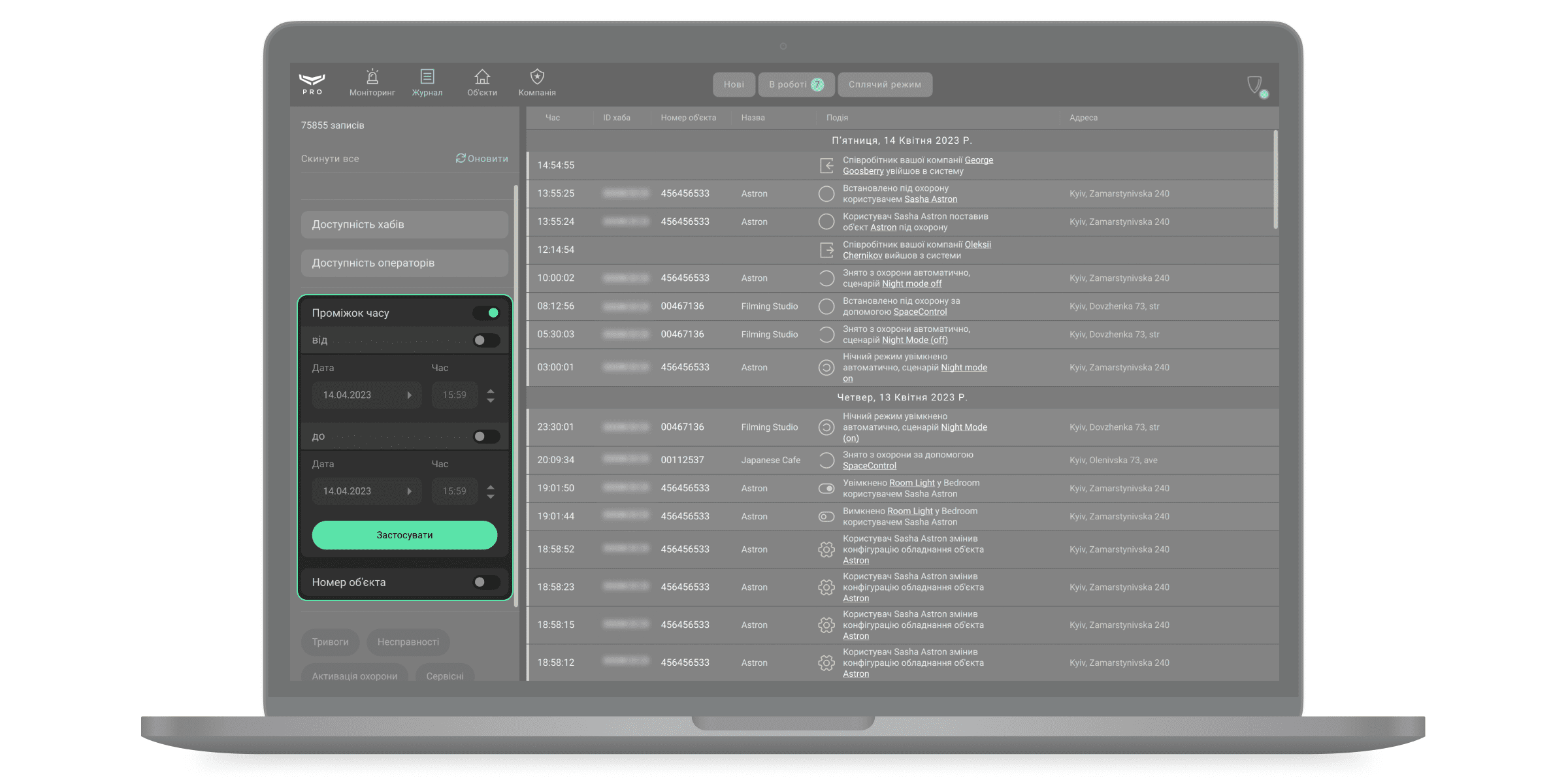
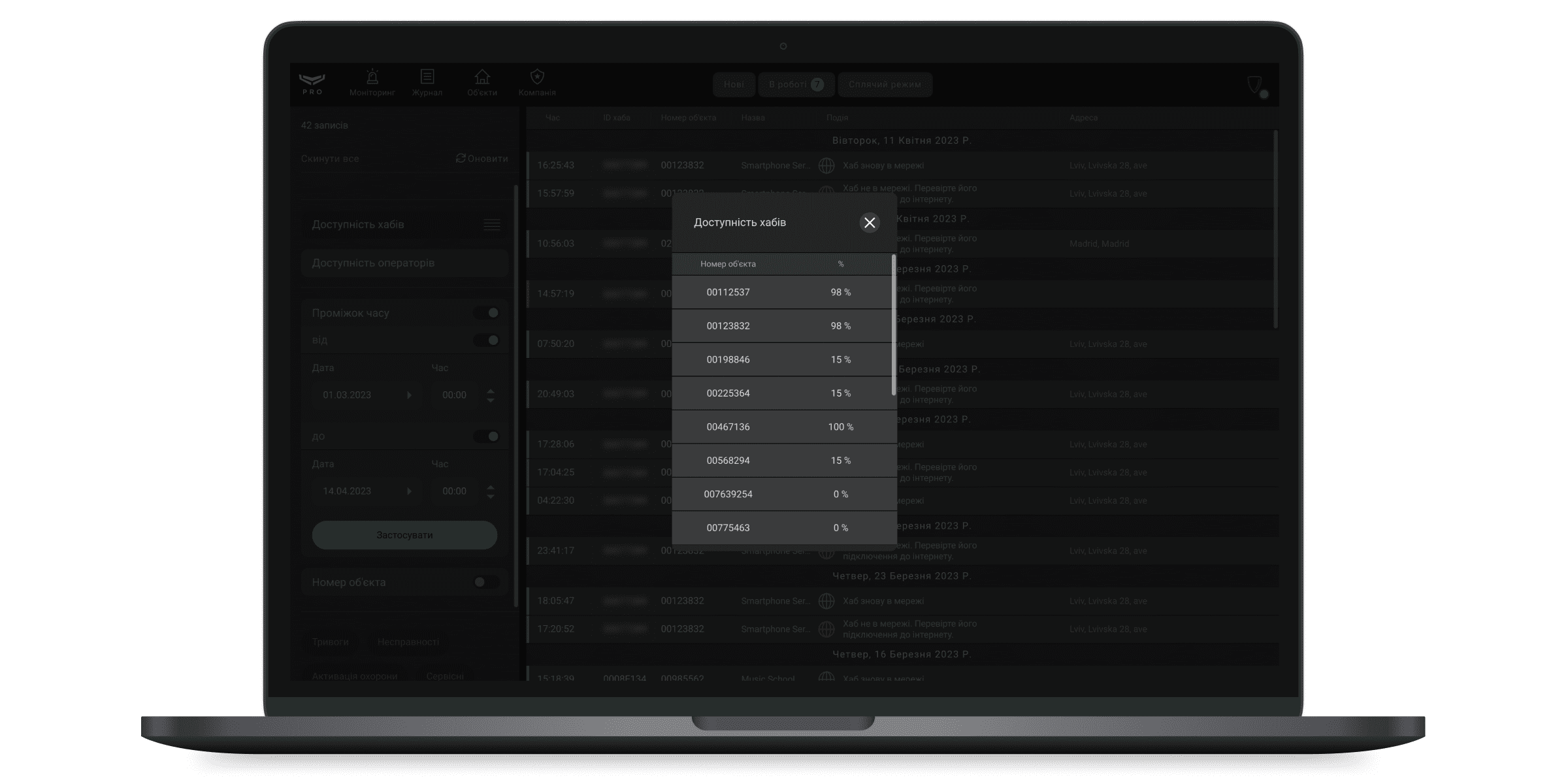
Ajax PRO Desktop може формувати звіти, що показують час зв’язку із системами безпеки (Доступність хабів). Також можна сформувати звіт про доступність операторів. Щоб створити звіти про доступність хабів, виберіть фільтр Доступність хабів. За початкових налаштувань звіт охоплює останні 7 днів. За необхідності період можна змінити у фільтрі Проміжок часу, а також задати номер об’єкта.
Звіт про доступність буде сформовано для вибраних об’єктів, якщо фільтр за номером об’єкта активний. Якщо фільтр за номером об’єкта є неактивним, звіт буде сформований про всі хаби компанії. Встановіть параметри, натисніть кнопку формування звіту біля назви фільтра – звіт відкриється у новому вікні.
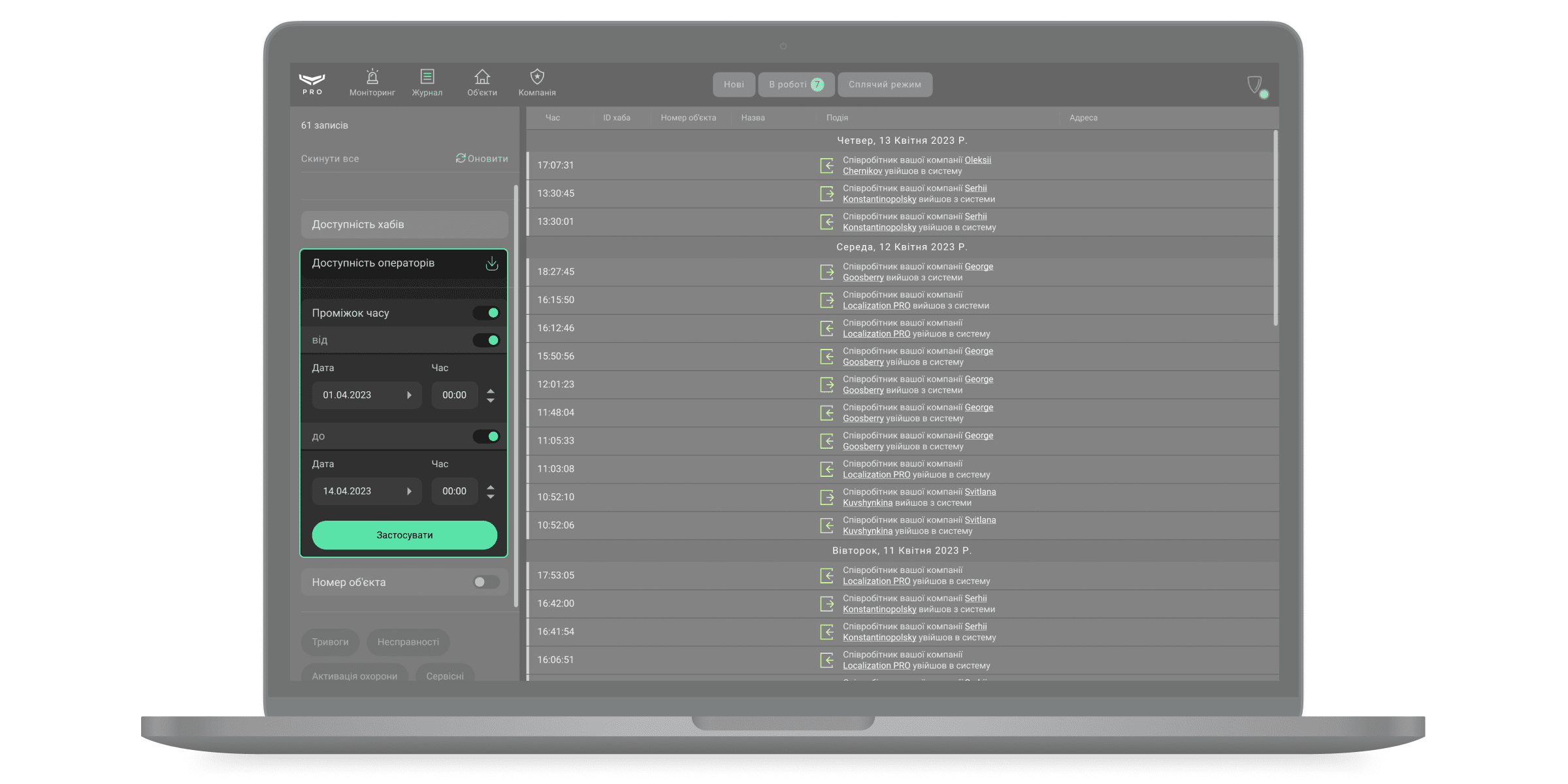
Для формування звіту про доступність операторів до уваги беруться лише робочі місця операторів, підтверджені у модулі Компанія. Для формування звіту натисніть на фільтр Доступність операторів.
Праворуч з’явиться список з подій:
- Увійшов в систему — зафіксовано вхід до облікового запису оператора.
- Вийшов з системи — зафіксовано вихід з облікового запису оператора.
- Співробітник вашої компанії створив новий приймач для моніторингу через Ajax Cloud.
- Співробітник вашої компанії змінив налаштування для приймача.
- Співробітник вашої компанії видалив приймач.
- Звʼязок з {1} втрачено — втрата інтернет-з’єднання з комп’ютером оператора.
- Звʼязок з {1} відновлено — відновлення інтернет-з’єднання з комп’ютером оператора.
- Приймач втратив зʼєднання за основною/додатковою адресою.
- Відновлено зʼєднання з приймачем за основною/додатковою адресою.
- Моніторинг тимчасово зупинено: немає звʼязку з операторами — немає жодного доступного оператора.
- Моніторинг відновлено — доступний хоча б один оператор.
- Співробітник вашої компанії прийняв обʼєкт на моніторинг через приймач.
- Співробітник вашої компанії оновив номер обʼєкта для приймача.
- Співробітник вашої компанії припинив моніторинг обʼєкту через приймач.
Події можна відфільтрувати за часом, для цього слід встановити та застосувати діапазон. Щоб сформувати звіт за заданими параметрами — натисніть кнопку формування звіту біля назви фільтра.
Експорт журналу тривог і подій
Ajax PRO Desktop передбачена можливість експорту журналу тривог і подій. Опція дозволяє отримати документ у форматі CSV, який може містити до 1000 подій.
Системні вимоги
З червня 2025 року нові версії Ajax PRO Desktop більше не працюватимуть на Windows 7, Windows 8, усіх 32-бітних версіях Windows. Також Ajax PRO Desktop та Ajax Desktop більше не працюватимуть на macOS Catalina. Щоб надалі отримувати нові функції та покращення, будь ласка, оновіть операційну систему до 64-бітної версії Windows 10 (або новішої) чи до macOS Big Sur (або новішої версії).
Ajax PRO Desktop 4.24 та Ajax Desktop 4.24 — останні версії застосунків, сумісні зі старими операційними системами. Якщо ви використовуєте 32-розрядну версію ОС Windows або Windows 7, Windows 8 чи macOS Catalina (10.15), вам потрібна попередня версія Ajax PRO Desktop. Щоб отримати посилання для завантаження, зверніться до нашої служби підтримки за допомогою форми або контактних даних, розміщених у футері.
Проте ми рекомендуємо оновити операційну систему, щоб отримувати нові функції.
| Мінімальні | Рекомендовані | |
| Операційна система | Microsoft® Windows® 10 (64-bit) та новіші версії | Microsoft® Windows® 11 (64-bit) та новіші версії |
| Процесор |
Intel: Intel Core i3 (8-го покоління або новіше) або еквівалентний (наприклад, Intel Core i3-8100) AMD: AMD Ryzen 3 (серія 1000 або новіша) або еквівалентний (наприклад, AMD Ryzen 3 1200) |
Intel: Intel Core i5 (12-го покоління або новіше) або еквівалентний (наприклад, Intel Core i5-12600K) AMD: AMD Ryzen 5 (серія 5000 або новіша) або еквівалентний (наприклад, AMD Ryzen 5 5600X) |
| Оперативна пам’ять | 8 ГБ | 16 ГБ |
| Відеокарта | Графічний драйвер з підтримкою версії OpenGL 2.1 і вище | Графічний драйвер з підтримкою версії OpenGL 2.1 і вище |
| Памʼять | 2 ГБ вільного місця | 8 ГБ вільного місця |
| Роздільна здатність екрана | 1600×900 | 1920×1080 |
| Мінімальні | Рекомендовані | |
| Операційна система | macOS® Big Sur (версія 11.6) та новіші версії | macOS® 15 (Sequoia) та новіші |
| Процесор | M1 | M3 |
| Оперативна пам’ять | 8 ГБ | 16 ГБ |
| Памʼять | 2 ГБ вільного місця | 8 ГБ вільного місця |
| Роздільна здатність екрана | 1440×900 | 2560×1600 |