To one space you can add:
- up to 200 users;
- up to 50 rooms;
- up to 25 security groups.
The hub manages all of the devices within the system and transmits alarms. ReX radio signal range extender expands the boundaries of the protected area
To one space you can add:
No, you need an Ajax hub to connect a system to monitoring software.
Other features do not depend on the adding of a hub to the space, including the Control and Rooms tabs and quick access to automation devices.
You can add an unlimited amount of Yale smart locks to one space.
Only one hub can be added to one space.
No, you only need to update your app:
Features will remain the same, including the Control and Rooms tabs and quick access to automation devices.
Space is a virtual entity where various autonomous devices located on the same physical object are gathered. To create a space, a user does not need an Ajax hub. Devices are added to a system according to the needs of the facility.
You can add a hub with detectors, only NVR with cameras, only Ajax cameras, smart locks, or combine all these devices into one system.
The space concept offers flexibility for customizing the system according to the specific needs of the facility.
No such option is provided for. Deleting security system events is prohibited under the requirements of EN 50131.
To do this, in the Ajax app:
Internal tests and feedback from partners show that the system can work stably with Wi-Fi bridges, VPN tunnels and networks where there are no traffic restrictions.
We cannot guarantee a stable system operation under any other conditions or with any other equipment. Therefore, before installing devices, we recommend testing the system with the network equipment you plan to use.
Note that the network to which ReX 2 is connected must allow broadcast requests, and the 4269 port must be open for all types of traffic.
No. Both ReX 2 and the hub must be connected via Ethernet for this communication channel to work.
In this case, all alarms, events and photos are transmitted via Ethernet.
If ReX 2 loses connection with the hub via Ethernet, the range extender continues to transmit all alarms, events and photos via radio.
If the range extender loses connection with the hub through both communication channels — users and the security company receive notifications about the loss of connection with the range extender and all the connected devices. The time it takes to send messages depends on the hub settings: the Jeweler settings for hubs that support Ajax wireless devices and the Jeweler/Fibra settings for hubs that support wired and wireless devices.
The identifier (ID) is the serial number of the device. It is located under the QR code on the body, board, and packaging of the device.
ID at the bottom of the box

ID under the lid

The ID can also be found in the device states in the Ajax app.
To transfer settings and devices from one hub to another use Data Import function.
ReX 2 with a standard power supply unit operates off 110-240 VAC mains.
To connect ReX 2 to 12-24 V circuits, use 12-24V PSU.
12-24V PSU is required to connect the range extender to the power system of a car, trailer, yacht, or an external battery/power supply.
To connect ReX 2 to 6 V circuits, use 6V PSU.
6V PSU is required to allow the range extender to run on an external battery for years — without being connected to the facility’s electric power system — and be ready to protect run-down or empty premises as well as buildings under construction against burglars, vandals, or unauthorized occupants.
You can calculate the run time of ReX 2 from an external battery using a calculator.
Central panels: ReX 2 can be connected to Hub 2 (2G), Hub 2 (4G), Hub 2 Plus, Hub Hybrid (2G), Hub Hybrid (4G).
Range extenders: ReX 2 cannot be connected to another radio signal range extender.
Integration modules: ReX 2 cannot be connected to ocBridge Plus and uartBridge.
Power supplies: ReX 2 is compatible with 12-24V PSU for Hub2/Hub 2 Plus/ReX 2.
Other devices: ReX 2 is compatible with all Ajax devices that support Jeweller and/or Wings radio protocols.
You can connect up to 5 ReX 2 range extenders to a compatible hub. Connection to another range extender is not provided.
The list of compatible hubs is available at the link. Connection to other hubs and ocBridge Plus and uartBridge integration modules is not provided.
The delivery time for photo verifications via ReX 2 range extender depends on the hub communication channel, type of detector and the resolution of the images.
Photo delivery time through the Wings radio protocol:
| Detector | Photo resolution (pixels) | Photo delivery time via range extender |
| MotionCam Jeweller MotionCam (PhOD) Jeweller |
160 × 120 | Up to 8 seconds |
| 320 × 240 (default) | Up to 18 seconds | |
| 640 × 480 | Up to 31 seconds | |
| MotionCam Outdoor Jeweller MotionCam Outdoor (PhOD) Jeweller |
320×176 (default) | Up to 14 seconds |
| 640 × 352 | Up to 20 seconds |
Values provided that the hub works via Ethernet or 4G, and there are three bars of signal strength between ReX 2 and the detector, and between the hub and ReX 2. If you use the Photo on Demand feature, there may be a delay of up to 3 seconds before the detector takes a photo.
Photo delivery time via Ethernet:
| Detector | Photo resolution (pixels) | Photo delivery time via range extender |
| MotionCam Jeweller MotionCam (PhOD) Jeweller |
160 × 120 | Up to 6 seconds |
| 320 × 240 (default) | Up to 10 seconds | |
| 640 × 480 | Up to 16 seconds | |
| MotionCam Outdoor Jeweller MotionCam Outdoor (PhOD) Jeweller |
320×176 (default) | Up to 10 seconds |
| 640 × 352 | Up to 17 seconds |
Values provided that the hub works via Ethernet or 4G, and the signal strength between ReX 2 and the detector is three bars. If you use the Photo on Demand feature, there may be a delay of up to 3 seconds before the detector takes a photo.
If the detector is connected via a range extender, alarms are delivered in 0.3 seconds.
If the connection between the hub and ReX 2 is lost, all devices connected to the range extender also lose their connection with the hub.
Devices that have lost connection with the hub cannot transmit events, alarms, or photos to users and the security company monitoring station until connection is restored.
Thanks to OS Malevich, the range extender combines detectors into an autonomous group. If ReX 2 receives an alarm signal from the detector after the loss of communication, the range extender will activate the siren connected to it.
The number of scenarios by alarm, Button press, and by schedule depends on the hardware capabilities of the hub: Hub supports up to 5 scenarios, Hub 2 and Hub Hybrid — up to 32, Hub Plus and Hub 2 Plus — up to 64.
At the same time, only one reaction to arming/disarming for every automation device can be created. Scenarios of this type are not included in the general limit of the scenarios.
The list of ReX compatible devices:
| Security detectors | |
| Fire detectors | |
| Leakage detectors | |
| Automation devices | |
| Control devices | |
| Sirens | |
| Integration modules |
ReX is not compatible with ocBridge Plus, uartBridge, MotionCam and MotionCam Outdoor.
The SIM card number can be determined using two methods:
The functioning of the feature depends on whether the manufacturer recorded the number-related information on the SIM card
The number of ReX range extenders connected to the Ajax security system depends on the hub model:
| Hub | 1 |
| Hub Plus | 5 |
| Hub 2 (2G) | 5 |
| Hub 2 (4G) | 5 |
| Hub 2 Plus | 5 |
| Hub Hybrid (2G) | 5 |
| Hub Hybrid (4G) | 5 |
Only hubs on OS Malevich 2.8 and higher support the connection of several ReX.
Alarms are communicated within 0.3 seconds.
In the event of a loss of connection between the hub and ReX, all devices connected to the range extender also lose connection with the hub.
By copying the system information from the hub, ReX creates an autonomous group of devices and responds to events instantaneously. If ReX continues to communicate with the connected devices when the connection with the hub is lost, ReX assumes the role of the control panel: it will receive an alarm signal from the detector and activate the siren.
Users can manage the security modes of ReX and of the devices connected to the range extender only after the connection between the range extender and the hub is restored.
ReX functions at a distance of up to 1,800 meters from the hub and can double the radio communication range between the Ajax devices and the hub.

The communication range between ReX and a paired device is limited by the radio signal range of the device (the relevant parameter is indicated in the device’s specifications on the website and in the User Manual).
You can significantly expand the coverage area of the Ajax radio network using several ReX in the security system. However, keep in mind that ReX can only be connected directly to the hub and connecting one range extender to another is not supported.
The number of ReX connected to the security system depends on the hub model.
No. ReX expands the security system’s radio communication coverage, thereby enabling the installation of Ajax devices at greater distances from the hub or in locations where a reliable signal reception from the control panel cannot be ensured.
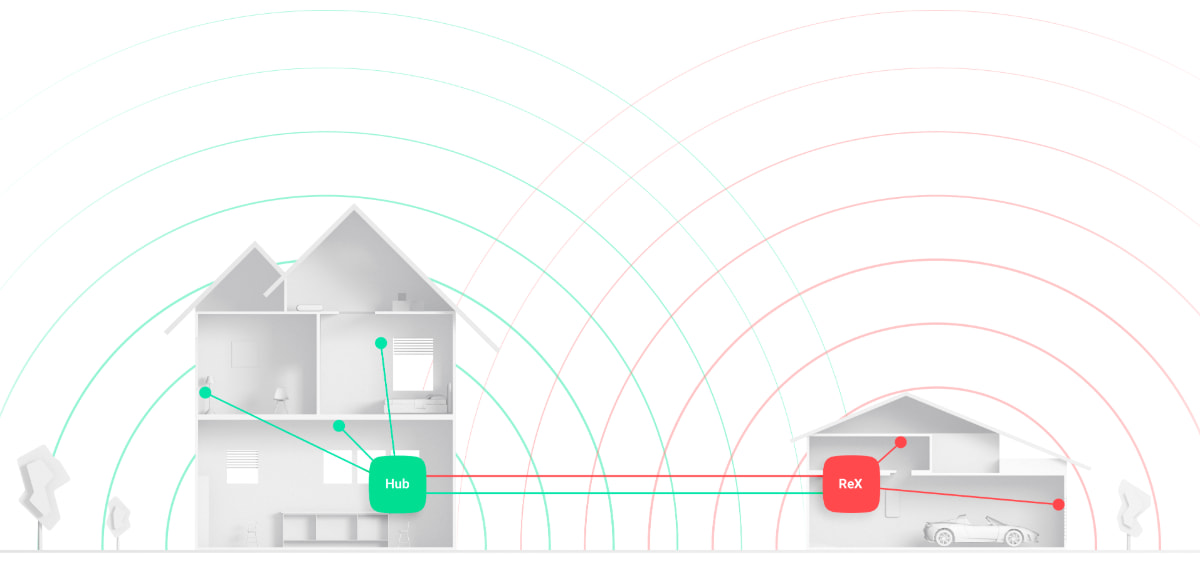
ReX expands the hub’s radio communication coverage.
ReX receives hub signals and transmits them to the devices connected to the range extender. It also transmits signals received from the devices to the hub. Two-sided connection is provided by the Cargo protocol operating over the Jeweller radio protocol.

Unlike regular range extenders that only re-broadcast signals, ReX controls the functioning of the security system devices. By copying the system information from the hub, ReX creates an autonomous group of devices and responds to events instantaneously. If the hub disconnects from the network for whatever reason, ReX receives an alarm signal from the detector and activates the siren.
ReX does not increase the number of devices connected to the hub!
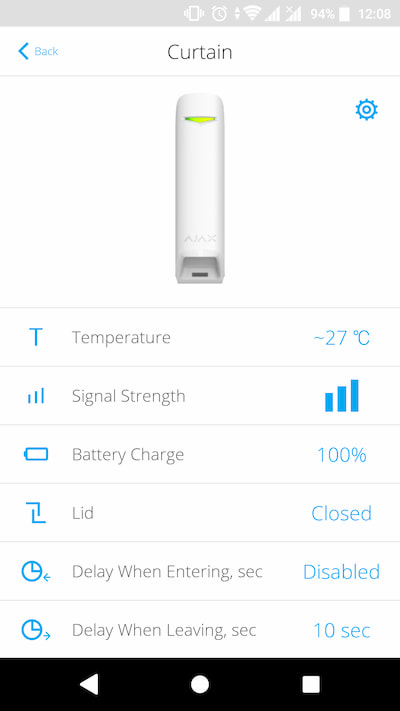
Tamper is a miniature button on the device board. It reports an alarm in case of opening the device enclosure, removing the device from the mounting panel, or detaching it from the surface.


The tamper status is displayed in Ajax apps, in the Enclosure section in the states of each device. When the body status is Open, a fault symbol appears on the device icon.
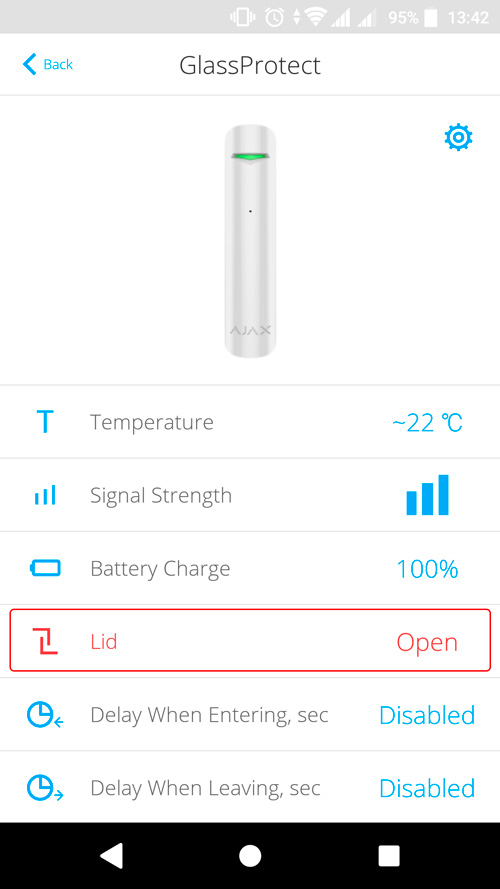
The maximum distance between the hub and the device can reach 2,000 meters in an open space.
Walls, ceilings, and other structures that interfere with the radio signal to get through can significantly reduce the range. In this case, maximum distance mainly depends on the structures’ material, thickness, and arrangement.
You can expand the coverage area of Ajax security systems with the help of radio signal range extenders
The Hub will be receiving new software features as long as its electronic components can support their functioning. Once its development potential is exhausted, the software will be updated to ensure compatibility with the Ajax server and applications.
The aim of developing Ajax is to provide current and future owners of our systems with greater opportunities. New products of the Ajax range will be operated under the control of Ajax hubs if such support can be ensured by updating the control panels software. In the future, the capacities of the new devices might require other hardware components of the central unit, and a new control panel will be needed to run them.
The Ajax control panels have different purposes. The standard Hub provides a basic set of features ensuring integrated security of an apartment, a house, a store, or an office. The advanced Hub 2 Plus has unique communication capacities: the control panel is equipped with Wi-Fi and Ethernet modules and two 2G / 3G SIM card slots, and it can ensure security of large facilities, which is attributed to its 150 detectors, 25 groups, 99 users, and 50 cameras, works up to 16 hours from backup battery. For the time being, less than 50% of the Hub 2 Plus hardware capabilities are utilized. Future software updates will uncover the full potential of the device.
We are developing Ajax to provide our customers with more opportunities and increase the level of security and resilience of the system. This process cannot affect negatively the user experience and limit the existing opportunities. The central units of all generations will be supported by the Ajax servers and applications.
The type of SIM card used is Micro-SIM.
SIM-card must be inserted with the front part (with the operator’s label) towards the cavity marked with the Hub:



In order to allow automatic updating of the firmware of the Hub, select the Hub in the device list, go to the settings , select Service and turn on the option Automatic software update.
Auto-Update is turn on by default.
Press the power button (the Ajax logo will turn off) and hold for 30 seconds, until the logo is flashing red. This will remove all detector connections, room configurations, and user setting. User accounts will remain connected to the system.
Most likely, several users are receiving SMS alerts. For example, if three people receive SMS alerts, then each notification is sent out three times.
No, Ajax Hub can work without port forwarding.
Yes, as long as the test shows a good enough radio communication. But you will still need to secure the Hub on the table with the provided screws. This is required to ensure the alarm will work if an intruder tries to dismantle Ajax Hub.
To make SIM card work properly, please do the following steps:
Detectors’ LED indication turns only in armed mode in case of alarm. While the detector is disarmed, it won’t blink with the LED in case of actuation.
The functioning of the detector may be checked using the Detection Zone Test
Check if both LEDs are lit on the Ethernet port when the cable is connected. If they aren’t, connect another Ethernet cable. If they are, check your router settings. It should be set to DHCP mode.
The system uses our own two-way protocol, Jeweller. The protocol allows Ajax Hub to monitor securely all network devices up to 2,000 meters away in open space, helps to identify detector failures and radio jamming, and carries out radio and detection zone tests.
By default, Ajax apps notify about the loss of hub connection with the Ajax Cloud server when there is no connection via all the connection channels: Ethernet, Wi-Fi, cellular (connection channels depend on the hub model).
Ajax apps can notify about such an event in two ways: with a push notification, with a siren sound (enabled by default).
To be notified about the connection loss, even on one of the channels, in the Ajax app:
Ajax’s security system can use the following connection channels with the Ajax Cloud server and the security company: Ethernet, Wi-Fi, or cellular. The number and the type of connection channels depends on the hub model. If connection is lost on any of the channels, the hub will instantly switch to another channel available.
When several channels are connected to the hub, priority is given to the faster ones: Ethernet and Wi-Fi (connection channels depend on the hub model). Cellular is used as a backup channel and consumes minimum of traffic. It is impossible to change this priority.
You will receive a push-notification. If you’ve activated SMS alerts, you will receive an SMS alert.
Yes. The battery inside the hub will provide for up to 16 hours of system operation. In the case of switching to backup power, a push-notification and an SMS-message will be sent.
Also hub can be connected to 12V⎓ sources.
The Ajax security system supports connection to Ajax Cloud via all connection channels at once: Ethernet, Wi-Fi, and cellular (channels depend on the hub model). This is necessary to ensure that in case of loss of connection on any of the channels, the hub instantly switches to another channel.
Most of the data is transferred via Ethernet and Wi-Fi, and fewer data is transferred via cellular. It is impossible to change this priority.
The hub update does not exceed 1 megabyte.
The user identifier is a unique number which is assigned by the hub to the specific user being added.
If the user has several hubs, they will be assigned their own unique number in each hub
Your own user identifier can be found in the profile settings (Hub → Settings → User settings
).
Your identifier and combinations for using the keypad personal password are displayed in the settings menu.
Ajax encrypts data using its own proprietary floating key protocol. This protocol is resistant to breaking: even with the power of a supercomputer, it will take years to break the key by a Brute-force search.
Let’s assume a situation where an attacker was able to compromise the key. In this case, the protocol is still protected by the session counter: a new encryption key is generated within each device-hub communication session.
Even if an attacker bypasses the session counter, he will be stopped by device authentication: a secure communication channel is created between the detector and the hub, followed by an ID check.
Each device has a personal ID by which the hub recognizes it.
If the device fails the ID check, the hub will ignore its commands.
Moreover, the hub will detect the loss of the Ajax device that the attackers want to replace with the fake one. The detection time depends on the device type: 3 seconds for wired Ajax devices and the time set in Jeweller settings — for wireless ones. The lost connection notification will be sent to the security company and system users.
To delete a group:
At the moment, it is impossible to delete all groups from the hub. To completely remove all groups, the hub must be returned to the factory settings!
To disable the group mode, go to groups settings (Hub → Settings → Groups) and deactivate the group mode.
The ID of the group is a number of the group, which is necessary for arm separate groups from the keyboard.
The group number (ID) is displayed in the group settings (Hub → Settings → Groups).
In hubs with the firmware version OS Malevich 2.6 and latest hub administrator can limit the user’s access to the following functionality:
All these settings you can find in the user’s settings (Hub → → Users → User settings
).
The rights to the group, viewing notifications, devices and rooms can only be removed from the user account!
The second IP address is a backup in case of direct connection to the Central Monitoring Station (CMS).
If the main IP address is not available, the hub uses the second IP address to send events.
When the Hub communication with the server fails (the Ajax logo lights red), the security system continues autonomous operation responding to all events, executing the enabled scripts, and activating the siren when applicable.
The events during the communication failure are recorded in the Hub buffer and are delivered to the Ajax applications when communication with the server is restored.
The hub buffer can store up to 130 events (Hub model — up to 64 events)
Since the Ajax applications communicate with the Hub via the server, you cannot operate the Hub via applications in the case of Internet connection failure.
If the hub connection to cellular network is active, it continues calling and sending SMS to users — if these notification methods are enabled.
The direct connection (Monitoring Station tab) is the channel used to transmit hub events directly to the Central Monitoring Station (CMS) of the security provider, bypassing our server.
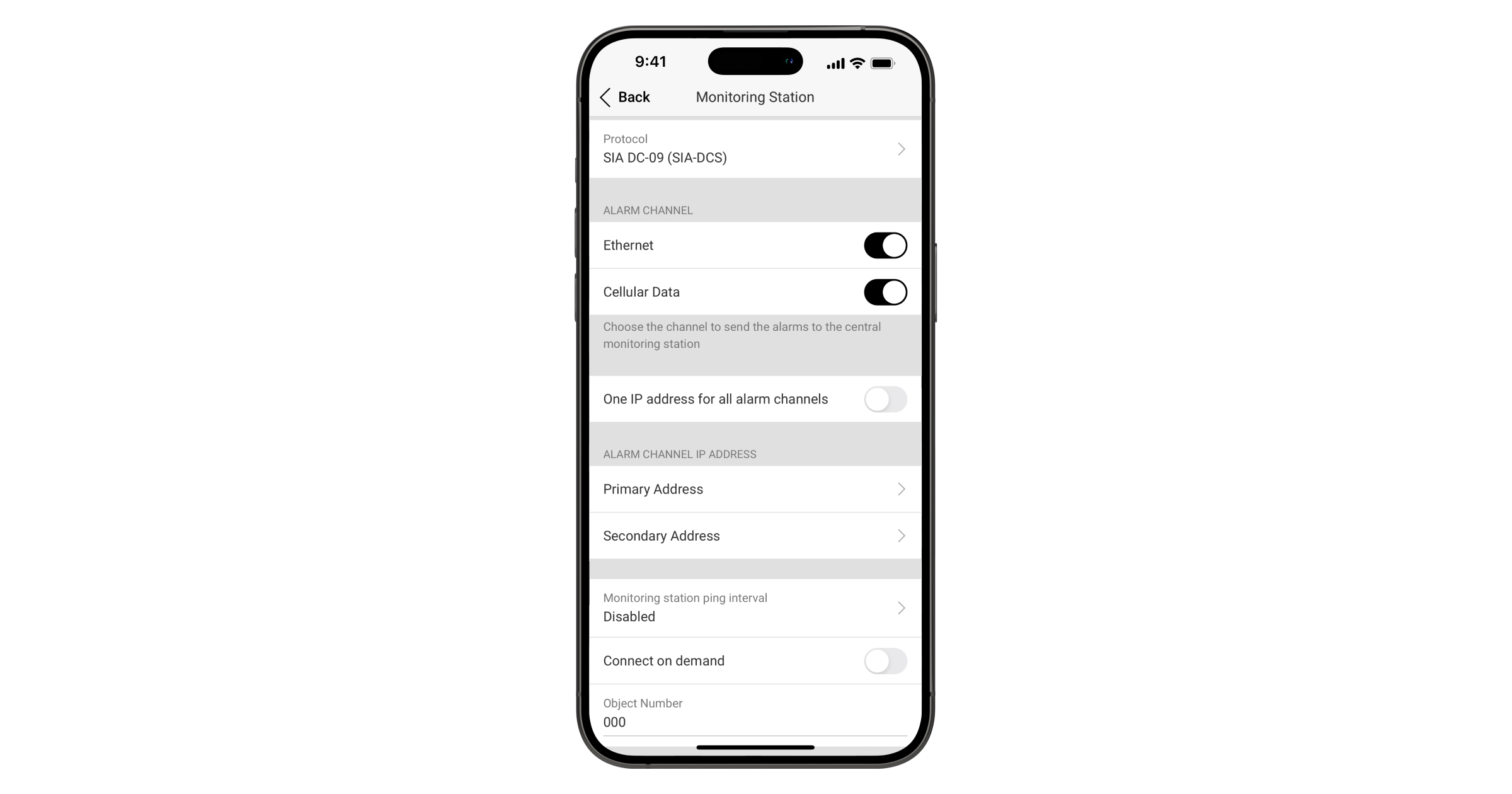
When direct connection is used, all events are communicated directly to the security company’s central monitoring station without affecting the functioning of the Ajax apps. If the direct connection is lost for any reason, the server acts as a redundant communication channel.
By default, the hub is set to a hub–detector ping interval of 36 seconds and 30 undeliverable data packets to consider the device lost. With these settings, the hub will detect the loss of the detector in 18 minutes.
To reduce this time, go to the hub settings in the Jeweller section and change the settings. The minimum time for detecting loss of connection with the device is 36 seconds (3 polls of 12 seconds each).
The time before raising the alarm by the communication loss between hub and device is calculated with the following formula:
Detector Ping Interval × Number of missed pings to determine connection failure
Note that with the minimum ping interval, short-term interference can lead to loss of connection with the device. Therefore, set the minimum values only if it is critically important to promptly inform about events in the system.
At the moment, such an opportunity is not provided, since the equipment of other manufacturers uses other frequencies and communication protocols with the control panels.
The automatic update is optional and can be disabled. To do this, go to the service settings of the hub (Devices → Hub → Settings
→ Service) and disable Firmware Auto-Update.
Change the SIM card is possible, while you need to clarify the tariff, tariff conditions and APN data from the operator whose SIM card you plan to use.
After changing the SIM card, you need to make changes to the GSM connection configuration in the Ajax application.
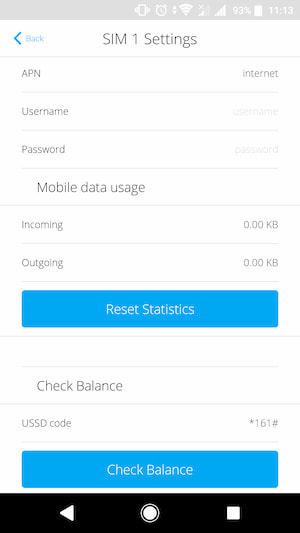
The number to top up is on the plastic card holder of the SIM card, included in the box. Top up like any other mobile phone account.
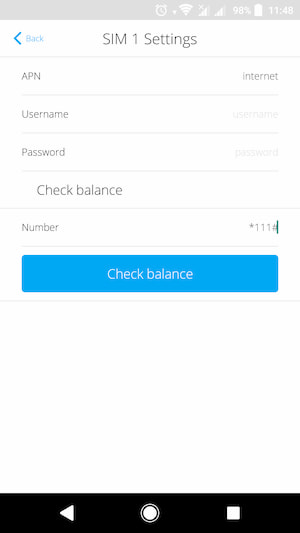
You need to click on the Number field, enter the balance check USSD code (available from the mobile phone service provider).
After entering the number, click “Check balance”. It takes about a minute to complete the request. After the query is executed, you will see the status of the SIM card account.
The hub consumes mobile traffic regularly to check the functioning of the GSM channel and its availability as a backup communication channel.
The volume data depends on the settings and the number of devices assigned to the Hub. Working in the regular mode without alarms, the Hub uses up to 10 Megabytes per day.
The loop (zone) number is required to describe all devices connected to the hub when adding a protected facility to the security company monitoring station.
The number is assigned when adding a device to the hub. The first added device has the first loop (zone) number. After removing the device from the system, its number becomes available. This number can be assigned to the next device to be added to the system.
The loop (zone) number is available in the states of each device in the Ajax app:
Monitoring Station — is a function used by security companies to configure a Direct Connection to the Hub with the CMS. When the Direct Connection is enabled, the Hub will send events directly to the IP and the port specified in the settings (without the participation of our server).
The firmware version can be found in the device states in the Ajax app.
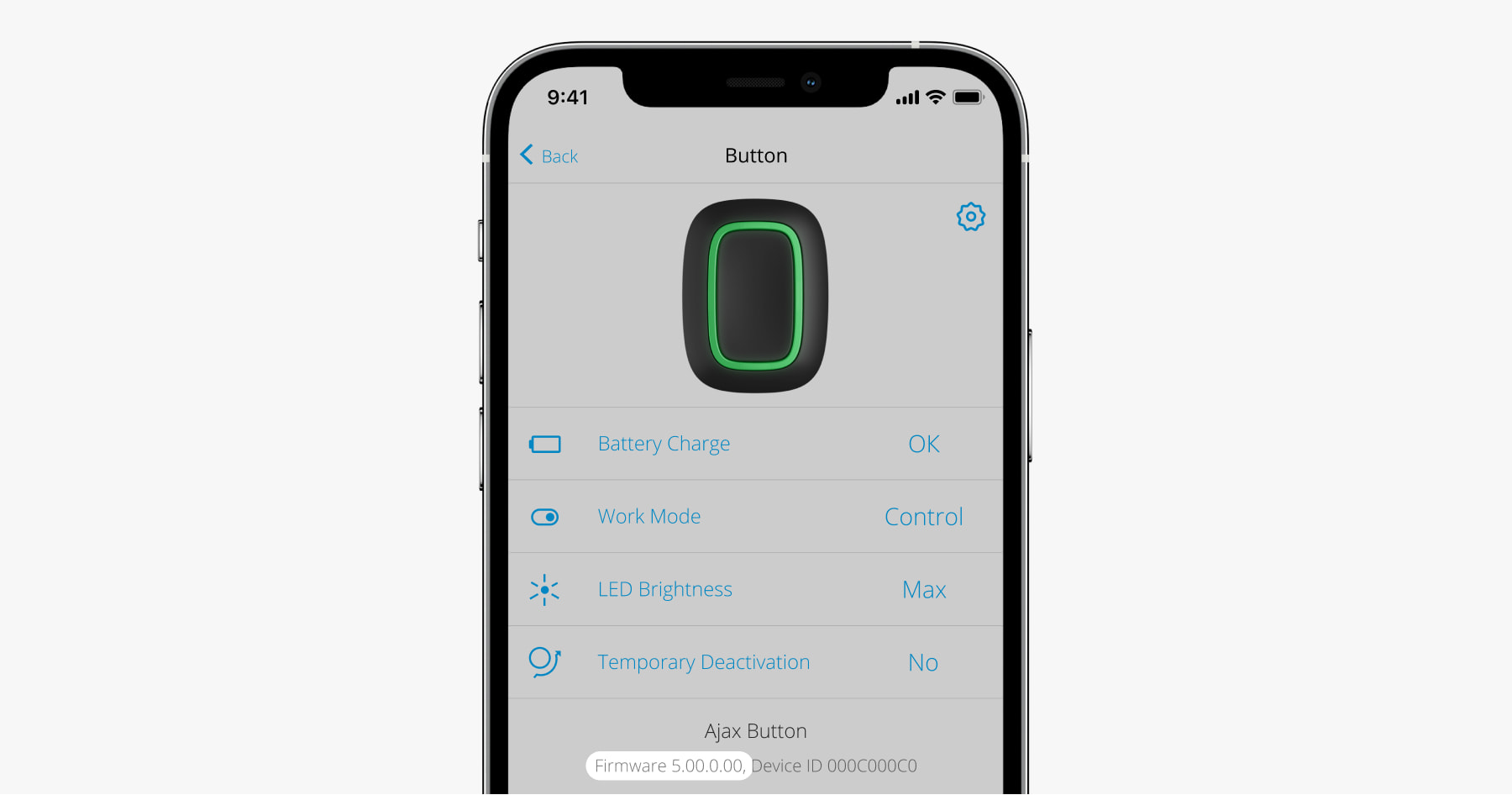
Go to the hub settings (Ajax Application → Devices → Hub → Settings
).
In the Cellular tab, select SIM card, enter the balance check USSD code (most often *111#), and click on the Check Balance button.
It is possible. In the Ajax Security System application, on average, you can add up to 50 Hubs. Such an amount can withstand the average user’s smartphone, the number of the attached Hubs is not limited and depends only on the phone characteristics.
However, we do not recommend using the Ajax Security System application to monitor a large number of objects, for these purposes there is a solution for professional installers, Ajax PRO: Tool For Engineers.
The detection time of communication failure with the server depends on two parameters in the Hub settings (Hub → Settings → Service):
The connection delay is activated after 4 failed pings.
The time until the message about the loss of communication between the Hub and the server is generated is calculated by the formula:
(Ping interval * 3) + Connection Delay
With the default settings, the server records the loss of the hub after 8 minutes:
(60 s * 3) + 300 s = 8 minutes
Reducing the time of registration the loss of communication with the Hub can be achieved by reducing the values of the ping interval and the connection delay. But this increases the likelihood of a false event of loss of connection with an unstable Internet connection.
Go to the Devices tab , select the device you want to check.